The Sophos Lively Adversary Report celebrates its fifth anniversary this yr. The report grew out of a easy query: What occurs after attackers breach an organization? Realizing the adversary’s playbook, in any case, helps defenders higher battle an energetic assault. (There’s a purpose we began life as “The Lively Adversary Playbook.”) On the similar time we have been discussing methods to instrument a testing surroundings to reply that what-happens query, Sophos was making ready to launch an incident response (IR) service. A cross-team challenge was born.
 For 5 years, we’ve offered our knowledge – first solely from the IR service, however finally increasing to incorporate knowledge from IR’s sister crew supporting present MDR clients — and offered evaluation on what we expect it means. As we proceed to refine our course of for amassing and analyzing the info, this report will deal with some key observations and evaluation – and, to have fun a half-decade of this work, we’re giving the world entry to our 2024 dataset, in hope of beginning broader conversations. Extra data on that, and the hyperlink to the Lively Adversary repository on GitHub, could be discovered on the finish of this report.
For 5 years, we’ve offered our knowledge – first solely from the IR service, however finally increasing to incorporate knowledge from IR’s sister crew supporting present MDR clients — and offered evaluation on what we expect it means. As we proceed to refine our course of for amassing and analyzing the info, this report will deal with some key observations and evaluation – and, to have fun a half-decade of this work, we’re giving the world entry to our 2024 dataset, in hope of beginning broader conversations. Extra data on that, and the hyperlink to the Lively Adversary repository on GitHub, could be discovered on the finish of this report.
Key takeaways
- Variations between MDR and IR findings present, quantitatively, the statistical worth of energetic monitoring
- Compromised credentials proceed to result in preliminary entry; MFA is important
- Dwell time drops (once more!)
- Attacker abuse of living-off-the-land binaries (LOLBins) explodes
- Distant ransomware poses a novel problem / alternative for actively managed methods
- Assault impacts comprise classes about potential detections
The place the info comes from
As with our earlier Lively Adversary Report, knowledge for this version is drawn from chosen instances dealt with in 2024 by two Sophos groups: a) the Sophos Incident Response (IR) crew, and b) the response crew that handles essential instances occurring amongst our Managed Detection and Response (MDR) clients. (For comfort, we discuss with the 2 on this report as IR and MDR.) The place acceptable, we evaluate findings from the 413 instances chosen for this report with knowledge from earlier Sophos X-Ops casework, stretching again to the launch of our IR service in 2020.
For this report, 84% of the dataset was derived from organizations with fewer than 1000 staff. That is decrease than the 88% in our earlier report; the distinction is primarily (however not solely) because of the addition of MDR’s instances to the combination. Simply over half (53%) of organizations requiring our help have 250 staff or fewer.
And what do these organizations do? As has been the case in our Lively Adversary Reviews since we started, the manufacturing sector was the most definitely to request Sophos X-Ops response companies, although the proportion of shoppers hailing from Manufacturing decreased from 25% in 2023 to 16% in 2024. Training (10%), Development (8%), Data Know-how (7%), and Healthcare (6%) spherical out the highest 5. In whole, 32 trade sectors are represented on this dataset.
Additional notes on the info and methodology used to pick instances for this report could be discovered within the Appendix. SecureWorks incident response knowledge is just not included on this report.
The principle occasion: MDR vs IR
 As we compiled and normalized the IR and MDR datasets, the Lively Adversary crew hypothesized that we’d doubtless observe higher safety outcomes in organizations the place expert energetic monitoring and logging have been already in place – in different phrases, the MDR instances. Whereas which will appear apparent, it’s the magnitude of among the variations that shocked us, and it’s these variations we’ll spotlight on this report.
As we compiled and normalized the IR and MDR datasets, the Lively Adversary crew hypothesized that we’d doubtless observe higher safety outcomes in organizations the place expert energetic monitoring and logging have been already in place – in different phrases, the MDR instances. Whereas which will appear apparent, it’s the magnitude of among the variations that shocked us, and it’s these variations we’ll spotlight on this report.
We’re one (however we’re not the identical): Ransomware and dwell time
Within the earlier report cycle, we noticed, however didn’t report on, distinct variations between the assault sorts prevalent for MDR clients and people prevalent for IR clients. This was the primary sturdy indication of the hole between the 2 datasets, and it was that distinction which set the tone and focus for this report.
In all earlier stories, ransomware has dominated the charts, as one may anticipate from IR-derived knowledge. A ransomware assault is just too damaging for a lot of organizations to remediate on their very own, particularly smaller organizations which will lack the sources essential to mount a full response.
The earlier 4 years of IR-only knowledge noticed ransomware prevalence differ between 68% and 81% of instances. For 2024 it’s all the way down to 40% of instances, dropping its prime spot to community breaches at 47%. Once we break it down by knowledge origin, the proportion for IR instances seems to be very very like all earlier knowledge. Ransomware (65%) is the dominant assault sort, adopted by community breaches (27%). The MDR knowledge paints a distinct image, by which community breaches (56%) outpace ransomware (29%) nearly two to at least one.
Determine 1: The change in attack-type findings in our dataset is placing – in 2024, community breaches overtook ransomware because the assault sort we mostly noticed. On the backside of the chart, nonetheless, there’s one other exceptional story – regardless of the dataset, each time the yr, no assault sort rises above 10 p.c of all instances seen; whether or not ransomware or community breaches are the principle occasion in a given yr, every little thing else is frankly secondary
The second set of information supporting our speculation considerations dwell time. Earlier years have seen dwell time lowering however stabilizing in the previous couple of stories. (We handled dwell time to a deep evaluation in our 1H 2024 report.) So far as we have been involved, dwell time was useless — till we noticed the statistics for this yr.
We received’t bury the lede: Median dwell time for all instances in 2024 was a swift two days. We see a well-recognized sample emerge in IR instances: General median dwell time is 7 days, with ransomware instances at 4 days and non-ransomware instances at 11.5 days. MDR dwell occasions, alternatively, have been decrease throughout the board, and the order of dwell occasions for ransomware (3 days) and non-ransomware (1 day) assaults have been inverted.
We consider it’s because sure actions (as an example, exfiltrating the info) can not go any quicker, since they depend on human exercise, knowledge throughput, or different pretty inflexible time frames. That’s to not say the assaults can’t be accomplished quicker, as a result of they’ll, however the knowledge reveals that ransomware assaults have historically required longer timeframes than different assault sorts. The truth that dwell occasions for ransomware instances dealt with by every service have been roughly equal is subsequently not stunning.
Non-ransomware instances, alternatively, have fewer velocity bumps, and right here’s the place the info highlights the variations between the companies. For instance, with IR instances, an attackers could reside within the sufferer’s community undetected for for much longer, till an occasion happens that causes ample noise or affect. An attacker utilizing legitimate credentials, who silently exfiltrates knowledge from a community over anticipated channels, may not be detected till they contact the sufferer, in the event that they ever do. (It also needs to be famous that the ransomware sector has attracted an awesome lots of the extra amateurish sort of attacker, which is normally much less adept at preserving quiet and protecting its tracks. Ransomware remains to be a numbers sport, so getting knocked off a excessive proportion of methods is simply a part of the enterprise mannequin.)
MDR instances for non-ransomware (or pre-ransomware) incidents, alternatively, are generated extra rapidly attributable to a mixture of detection engineering and fixed vigilance. Suspicious occasions are investigated sooner, and people who warrant further investigation are escalated. Briefly, quicker detection typically results in aborted ransomware, which implies the next proportion of assaults categorized as community breaches — and higher outcomes for the victims.
Come collectively: Root trigger
In distinction, we didn’t see a lot distinction between IR and MDR instances when it got here to root causes. Right here we see the acquainted mixture of compromised credentials (41%) and exploiting vulnerabilities (22%) main the way in which as soon as once more, and brute power assaults (21%) muscling their method to third place, as proven in Determine 2.
Determine 2: Root trigger in 2024 assorted between MDR and IR instances, however compromised credentials are nonetheless the main explanation for ache in each datasets
Brute power assaults have been perennially relegated to the also-ran class within the IR knowledge, however noticed a dramatic improve within the MDR knowledge, which vaulted the assault sort up the rankings for 2024. This can be all the way down to a distinction within the out there root-cause knowledge. In IR investigations, logs are sometimes unavailable, which reduces the investigative crew’s means to find out the basis causes of the assault. In distinction, MDR investigations have extra constant knowledge sources out there, which permits for extra exact analyses.
A have a look at the year-to-year knowledge, as proven in Determine 3, reveals the change in percentages between earlier years and 2024.
Determine 3: Compromised credentials in 2024 retreated from earlier excessive ranges as the most typical root explanation for issues, but it surely’s nonetheless a nasty state of affairs. (Knowledge from 2020 instances is just not represented on this chart attributable to a change in our knowledge labeling for this class)
In 2024, logs have been lacking in 47% of instances – 66% for IR, 39% for MDR. The main purpose for lacking logs in all instances was that they have been merely unavailable (20%) to analysts through the investigation, adopted by 17% of logs being cleared by the attackers and seven% lacking attributable to inadequate retention intervals.
(One software that usually will get used to clear logs is the Microsoft binary wevtutil.exe [the Windows Event Utility]. This can generate Home windows occasion log IDs 1102 [for security logs] and 104 [for system logs]. Organizations ought to contemplate configuring their safety instruments and menace hunts to detect this exercise.)
The rise in brute power as a root trigger aligns effectively with preliminary entry (TA0001) statistics. Exterior Distant Providers (T1133) was the favored preliminary entry technique, noticed in 71% of instances. As we’ve acknowledged beforehand, that is typically tightly coupled with Legitimate Accounts (T1078); this yr the duo teamed up in 78% of instances. Exploiting a Public-Going through Software (T1190) was the second-most single contributor to preliminary entry. The highest vulnerability instantly exploited for preliminary entry was CVE-2023-4966 (Citrix Bleed; 5%). Different components included uncovered Distant Desktop infrastructure (18%), weak VPNs (12%), and uncovered inside companies (11%).
You down with TTP?
We demonstrated in a earlier report that there have been few variations in TTPs between assaults with quick (5 days or fewer) versus lengthy (greater than 5 days) dwell occasions. These knowledge have been solely IR instances. Trying on the TTPs from this yr’s report, we see the sample maintain when evaluating IR and MDR instances.
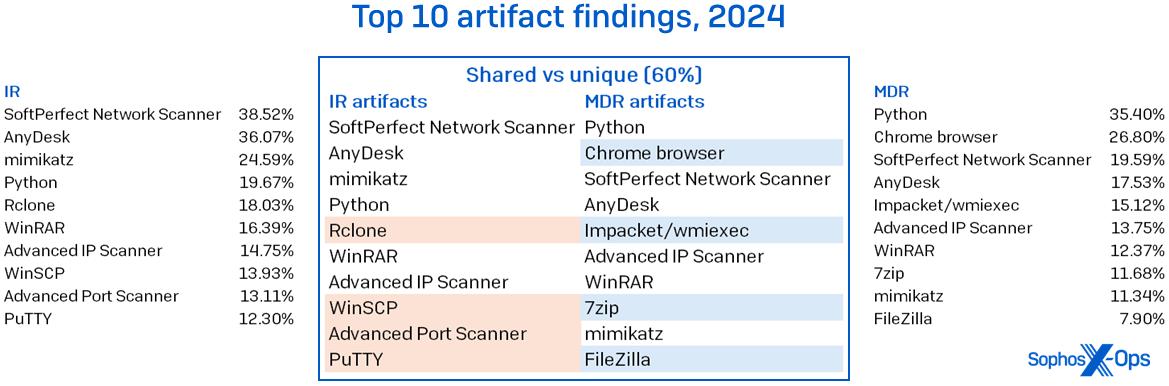
There have been barely extra artifacts seen in MDR instances (+24%), although the MDR dataset was round 240% bigger than that taken from IR. There was a 60% overlap within the 10 instruments most utilized by attackers. Among the many prime reputable instruments being abused have been some acquainted names: SoftPerfect Community Scanner, AnyDesk, WinRAR, and Superior IP Scanner, as proven in Determine 4.
Determine 4: The instruments seen abused in IR and MDR instances didn’t differ a lot on the prime of the charts, however sure variations and absences are placing
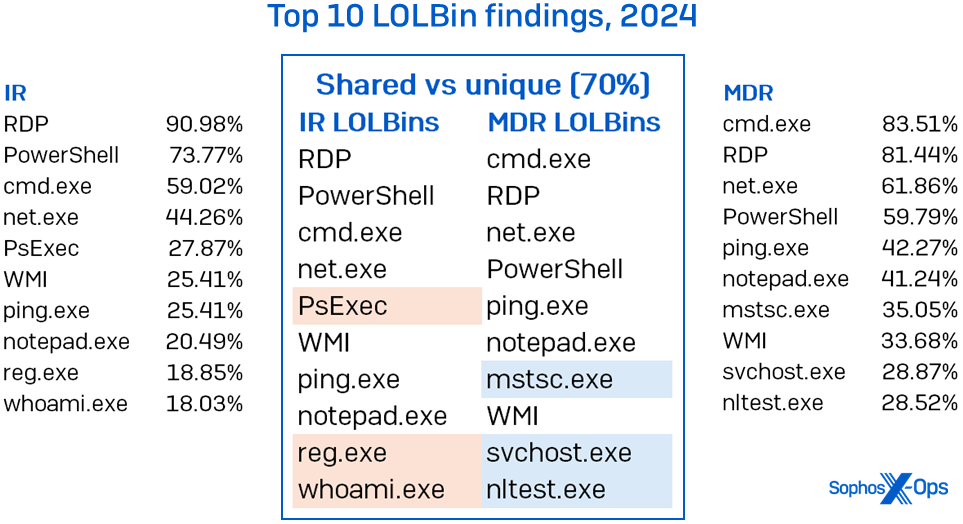
Microsoft binaries exhibited a tighter correlation between the datasets. The highest 10 abused LOLBins had a 70% overlap, as proven in Determine 5. There was a slight shuffle within the prime spot, with cmd.exe beating out RDP as probably the most abused LOLBin within the MDR case load. This isn’t solely stunning, since many MDR instances have a restricted blast radius: When licensed to take action, analysts will mechanically isolate affected hosts, thereby limiting attackers’ lateral-movement capabilities.
Determine 5: LOLBin abuse presents itself a lot the identical irrespective of which crew is trying; particularly, the distinction between MDR and IR in the case of RDP abuse exists however is just not substantial
The ultimate comparability seems to be on the “different” class, by which we group methods and traces that don’t fall into the opposite two classes. The highest 10 had an 80% overlap in IR and MDR instances; creating accounts, deleting recordsdata, putting in companies, malicious scripts, and modifying the registry have been the dominant methods, as proven in Determine 6. Others, comparable to SAM (Safety Account Supervisor) dumping, have been extra widespread in a single crew’s dataset.
Determine 6: As we see, in additional than half of all instances, the attackers used acquainted and comparable TTPs. (Observe that percentages add as much as over 100%, since most instances have a number of findings on this class)
The chew from inside (reprise)
As has develop into the norm at Lively Adversary HQ, we wish to test in on a few of our findings from earlier stories, particularly these for which the info interval is lower than 12 months. The following part seems to be on the key takeaways from our earlier report (protecting the primary six months of 2024) and compares them to the total yr’s dataset.
LOLBins
The abuse of Microsoft binaries continued unabated within the second half of 2024, and the ratio of distinctive LOLBins to earlier years additionally continued to rise. Within the first half of 2024 we noticed a 51% rise within the depend of distinctive LOLBins, which completed the yr at 126% over 2023 counts. There was a 17% case rise in 2H 2024 and a 24% rise in distinctive binaries used. There have been no significant variations within the particular person binaries used all year long. Between the primary half and second half of the yr, there was a 95% overlap within the 20 most-abused instruments in IR and MDR instances. Instruments that can be utilized for enumeration – along with reputable and malicious makes use of — continued to be extremely represented in each datasets, making up 50% of the 20 most-abused binaries.
Notepad.exe was a brand new entry on this yr’s prime 10. This software was predominantly used for searching recordsdata on the community, together with recordsdata containing passwords saved in plaintext (5%). Instruments like Notepad present an attention-grabbing detection alternative. We’d argue that almost all customers will not be utilizing Notepad in favor of different Workplace applications. However there’s additionally a giant distinction between clicking on the Notepad icon, typing notepad in Home windows search, or typing notepad.exe on the command line. Having the ability to discriminate between these three completely different launch strategies can inform the intent of its use.
The identical is true of instruments like PowerShell. We’re not going to recommend that IT groups cease utilizing it, however there are some fast heuristics that may be utilized utilizing detection engineering. Was that PowerShell script closely obfuscated, and did it attain out to the web? If it did, it ought to in all probability be investigated.
The principle concern with LOLBins is they have a tendency to generate quite a lot of noise. The problem for IT groups is knowing the place the sign exists.
RDP
RDP detections proceed to prime the chart of abused Microsoft instruments. In 2024, it was utilized by attackers in 84% of instances, with 67% getting used just for inside lateral motion and three% getting used solely externally. That’s earlier than we add the instances the place it was used each internally and externally. The addition of these instances brings the totals to 83% and 19% respectively.
Regardless of RDP’s continued abuse – and our pleas for it to be banished past the wall – we perceive why it persists in networks. To that finish, it gives us with a possibility to discover how we’d each constrain its use and instrument some detections for its abuse.
Ideally, all RDP use is constrained by each community choke factors and consumer identities. The place doable we want so as to add MFA to the authentication circulation and apply the precept of least privilege. By constraining its use, and understanding what regular seems to be like, it turns into simpler to detect anomalies.
There are a number of methods to detect authentication occasions, however broadly talking, you’ll be able to search for Home windows logging occasion IDs 4624 and 4625. The previous is a profitable authentication occasion, whereas the latter signifies a failed try. Profitable login occasions can assist you catch an attacker utilizing legitimate credentials outdoors of regular use, whereas a number of failed makes an attempt may give you an early warning to any brute power exercise in opposition to your accounts.
For those who use a company customary for naming your gadgets, as many firms do, you should use that as one other indicator. Any profitable authentication that doesn’t conform to the usual ought to be investigated. In case your group doesn’t have a normal, this may very well be a possibility to implement one and create passive journey wires for attackers. Then once more, if the hostname “kali” reveals up in your community, because it did in 6% of instances, it is best to examine.
Lastly, you’ll be able to benefit from time-zone bias in RDP logging. That is the distant consumer’s time offset from UTC. If most of your customers are in UTC-6, however an otherwise-unremarkable distant consumer logs in utilizing legitimate credentials and a traditional trying hostname, however has a time-zone bias of +3, run like hell to seek out out why. (After which there are the occasions we’ve seen innocuous-looking machines linked, however sharing a Russian-named printer for some purpose…)
The concept behind these detection alternatives is to take impartial, however generally noisy or weak indicators, and sew them collectively to realize a stronger, extra dependable sign. Or, because the cool youngsters name it, protection in depth.
These eager to know extra about RDP and the way to detect its abuse can discover further particulars in our RDP collection.
Attribution
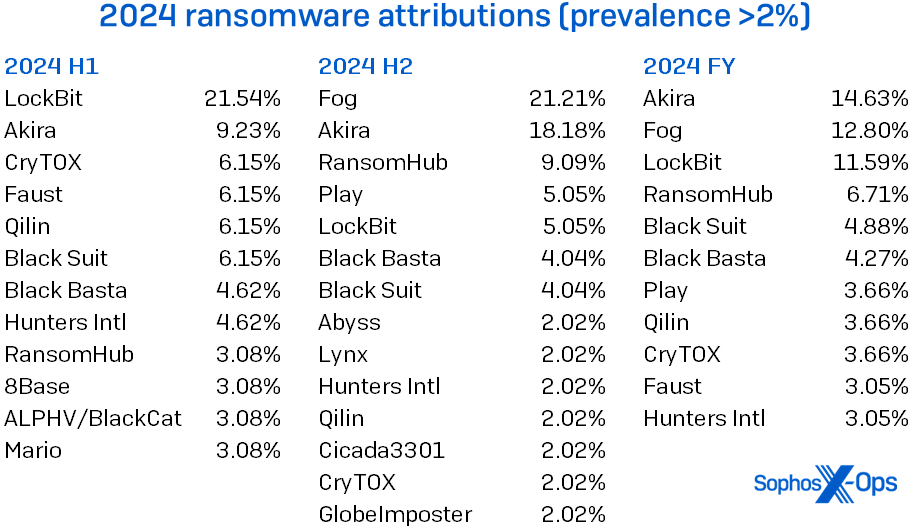
Within the final report, we predicted that in 2024 there would in the end be no overwhelmingly dominant ransomware adversary; with a regulation enforcement takedown early within the yr kneecapping LockBit, 2023’s main miscreant, the sector opened up for the Subsequent Massive (Dangerous) Factor. Because the desk in Determine 7 reveals, this was right – Akira rose to the highest of the pack, however solely simply. (LockBit was, alternatively, so dominant in the beginning of final yr that it nonetheless got here in third within the rankings regardless of the takedown.) Through the second half of the yr, Fog seeped onto the charts, edging out Akira for the highest spot. (The MDR crew did see a few trailing-edge LockBit infections early within the second half, however even these traces evaporated by yr’s finish.) The sample could but break down in 2025 because of doubtless adjustments in (amongst different issues) law-enforcement effort coordination – and LockBit nonetheless swears they’re making a comeback. We’ll be watching with curiosity.
Determine 7: Fame is fleeting, as LockBit’s perpetrators realized within the latter half of 2024; in the meantime, a heavy Fog rolled in
Having the ability to attribute bother to a particular adversary is soothing, one way or the other. However practitioners are sometimes combating forces which might be nominally on their aspect, whereas coping with selections made by the bigger enterprise that really feel like another battle to be dealt with. Our case research on this report describes how that went for one “unfortunate” MDR buyer.
Case research: Two in opposition to one
Whereas we proceed to reiterate basic safety tenets (shut uncovered RDP posts, use MFA, and patch weak methods), within the face of enterprise change processes past practitioners’ management, it’s not all the time that simple. Safety practitioners will not be solely combating the battle in opposition to the threats posed by exterior adversaries, however an inside battle with enterprise processes and alter administration. This tug-of-war got here again to chew one MDR buyer. Following a community breach by which the menace actor gained preliminary entry by means of a weak VPN, the shopper confronted a two-month estimated timeframe to patch the VPN equipment. With a ransomware gang ready within the wings, the battle between safety priorities and people of the bigger enterprise resolved in simply concerning the worst manner doable.
You and me in opposition to me
The Sophos MDR crew just lately responded to this buyer’s essential incident, with preliminary entry recognized as considered one of our ordinary suspects – an unpatched VPN equipment. On this case, a FortiGate firewall was operating on firmware model 5.6.11, which was launched in July 2010; the firewall itself reached end-of-life in October 2021. As well as, MDR recognized a misconfiguration in VPN user-access controls, which considerably elevated the chance of unauthorized entry.
After gaining preliminary entry, the menace actor moved laterally to the area controller, leveraged AV-killer instruments, carried out enumeration, and gained persistence on a variety of gadgets inside the property. At this stage, MDR’s response crew disrupted the attacker exercise, and calm resumed.
The MDR crew really helpful the shopper (at minimal) patch the 14-year-old VPN firmware with urgency, and disable the SSL VPN within the meantime. Nonetheless, the shopper’s enterprise processes weren’t cooperative; disabling the VPN altogether would trigger unacceptable enterprise affect, and the patches couldn’t be utilized for 2 months (!). The misconfiguration, the shopper estimated, would take one week to treatment.
Already combating
It’s an unlucky truth of incident-response life that we can not compel; we will solely suggest – and, generally, we will solely stand by watching historical past repeat itself. And it was repeating: The identical buyer had already skilled a comparable breach, involving the identical weak VPN, 14 months earlier. In that case, the shopper didn’t but have MFA enabled for VPN logins; a brute power assault was profitable, and the attacker was capable of disable protections and dump credentials. Within the course of, the attacker managed to compromise a key service account, leaving the shopper unable to carry out a vital credential reset attributable to – once more – enterprise necessities. (Do not forget that service account; we’re about to see it once more.)
The hole between the primary breach and the second was, as talked about, 14 months. The hole between the second and the third was far shorter.
So what’s one other one?
The second incident concluded. The VPN and that service account – one factor out of help for almost 4 years, one factor known-compromised for over a yr – waited in business-process limbo, as did the VPN misconfiguration. The safety practitioners have been affected person. The attacker wasn’t. 9 days after the shut of the second breach, CryTOX roared in. Utilizing the compromised service account and taking full benefit of the unpatched and (nonetheless) misconfigured VPN, the ransomware ran rampant by means of the system, transferring laterally, killing endpoint-security processes, and in the end encrypting your entire property.
It could be mentioned on this case that ransomware received the tug of struggle between safety practices and enterprise change processes. (Silver lining: After the third incident, the VPN was lastly disabled, although affected accounts have been nonetheless re-enabled with out credential resets.) Whereas not all organizations are so unfortunate, on this case the anticipate enterprise change approval was a risk-assessment gamble that failed terribly.
Better of the remainder
As we wrap up our 2024 findings, let’s test in on different statistics that drew our consideration.
Along with an elevated variety of instances, this yr’s dataset included the largest year-to-year improve in all noticed TTPs. Compared with 2023, the variety of abused instruments was up 80%, LOLBins have been up 126%, and every little thing else (“different”) was up 28%. What’s attention-grabbing about these numbers is the lengthy tail for every class – that’s, the variety of instruments or LOLBins or “different” that appeared ten occasions or fewer within the dataset. Once we tally each single discovering in each single case, these rarities account for 35% of all software use (689 findings of 1945 whole; 334 distinctive objects), 12% of all LOLBin use (508 findings of 4357; 184 distinctive objects), and 12% of all “different” (476 findings of 4036; 189 distinctive objects). A biologist may name these vestigial tails; we name them a decrease investigation precedence than the dominant beasts on the tops of the TTP charts.
No time to waste
In the case of sure goals, attackers don’t fritter and waste the hours in an offhand manner. We first reported on the race to Lively Listing compromise in 2023. This statistic has continued to pattern downward, and the median now stands at 0.46 days. In different phrases, as soon as an attacker enters the surroundings, it’s solely 11 hours earlier than they go after the AD server. Most (62%) of the compromised servers have been operating working methods that have been out of mainstream help.
Video games with out frontiers
One other time-related statistic that we first reported on in 2023 was the time of day that attackers selected to deploy ransomware payloads. Whereas extra knowledge softens the values considerably, the outcomes are nonetheless compelling. In 2024, 83% of ransomware binaries have been deployed outdoors the goal’s native enterprise hours; the all-time statistic stands at 88%. Whereas it seems that ransomware deployments solely come out at evening, there doesn’t nonetheless appear to be any lingering desire in days of the week.
Instruments to stroll by means of life
The proportion and kinds of instruments – each reputable and malicious – that make up this class have remained comparatively secure for a few years. Listed here are some highlights from this yr’s knowledge, along with the problems lined above.
We’ve seen a giant drop within the proportion of assaults that use Cobalt Strike. This software occupied the highest spot in abused instruments from 2020-2022, dropping to second place in 2023. This yr noticed it slip all the way in which all the way down to thirteenth on our record, showing in simply 7.51% of instances. As a consequence of its historic recognition with attackers, it nonetheless occupies the highest spot within the all-time rankings, the place it has been concerned in 25% of assaults prior to now 5 years. We consider the lower is because of elevated prevention and detection capabilities. Cobalt Strike was fashionable as a result of it was efficient. Now that its effectiveness has declined, so has its use. Whereas that is welcome information, it additionally means that one thing else has or will take its place.
A software that has seen an order of magnitude improve in abuse is Impacket. Impacket instruments have been round for at the very least a decade and may carry out a wide range of actions, together with manipulating community protocols, dumping credentials, and reconnaissance. Its use has steadily grown in recent times, from 0.69% in 2021 to 21.43% in 2023; attackers actually ramped up their use of Impacket in 2024, when it overtook all different instruments and landed within the prime spot. Probably the most used Impacket software was wmiexec.py, which featured in 35% of assaults. (In our statistics, we determine the particular Impacket subclass each time doable; if there’s doubt, we merely classify it as Impacket, no subclass.)
A venerable software seeing a slight year-on-year decline is mimikatz. The credential-harvesting software was reliably noticed in round 1 / 4 of assaults in earlier years however slipped to fifteen% in 2024. Whereas we will’t decisively attribute its decline to anybody factor, it’s doable that it’s associated to the elevated use of Impacket instruments; particularly, the secretsdump.py script that can be utilized to dump hashes from distant machines. This correlates with a year-on-year improve in distant registry dumping and a halving of LSASS dumps (mostly attributed to mimikatz in our knowledge). Secretsdump.py was seen in at the very least 6% of assaults and was the second most used Impacket software after wmiexec.py.
Of the highest 15 instruments being abused, 47% are sometimes used for exfiltration of information. These instruments embrace well-known archiving software program and file switch instruments.
Different findings
Since we began monitoring the supply of multifactor authentication (MFA) in breached organizations, the information has gotten worse. In 2022, we noticed 22% of victims didn’t have MFA configured. That proportion almost tripled to 63% in 2024. That is one space the place there was no significant distinction between IR and MDR instances. MFA was unavailable in 66% of IR instances and 62% of MDR instances. This highlights a technique by which even probably the most succesful detection and response program can nonetheless go away organizations weak to assault.
One other regarding metric was the proportion of unprotected methods present in breached organizations. In 40% of the instances we investigated, there have been unprotected methods. Once we contemplate there have been additionally weak VPNs (12%), weak methods (11%), and end-of-life methods (5%) in a few of these environments (this report’s case research, as an example, had all three), attackers may really feel like a crafty fox within the rooster’s lair.
Some could ask why we’re nonetheless seeing ransomware instances in any respect in an MDR service. One massive purpose has to do with unprotected methods and their relationship with distant ransomware. All that malicious exercise – ingress, payload execution, and encryption – happens on unmanaged machines, subsequently bypassing the group’s safety instruments. The one indication of compromise is the transmission of paperwork to and from different machines. Our telemetry signifies that there was a 141% year-on-year improve in intentional distant encryption assaults since 2022, as proven in Determine 8. (We’ve talked beforehand about distant ransomware and the way to parry it, together with a deep dive into our CryptoGuard know-how; because the numbers rise, distant ransomware could also be a significant subject in a later Lively Adversary Report.)
Determine 8: In accordance with Sophos X-Ops knowledge, 2024’s distant ransomware tally was 141% of that of 2022; observe the startling rise in instances during the last 18 months of the info
The dearth of visibility for recordsdata transferring across the community – and of lacking logs – additionally contributes to exfiltration statistics. In 2024, analysts have been capable of affirm that exfiltration occurred in 27% of instances. Once we embrace proof of information staging and doable exfiltration, this rises to 36%. Ransomware victims had their knowledge exfiltrated in 43% of the incidents we investigated. A further 14% had doable exfiltration or proof of information staging. In contrast to time-to-AD, exfiltration findings happen in the direction of the top of an assault. There was a median time of 72.98 hours (3.04 days) between the beginning of an assault and exfiltration, however solely 2.7 hours (0.11 days) from exfiltration to assault detected for ransomware, knowledge exfiltration, and knowledge extortion instances.
Carry the noise
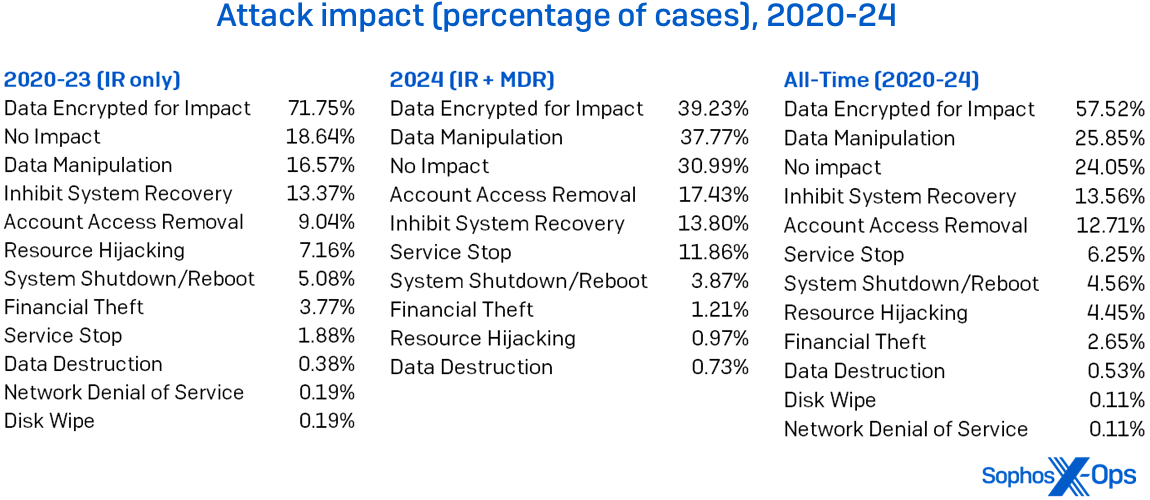
Lastly, this report has historically checked out MITRE impacts (TA0040). Given ransomware’s prevalence within the knowledge, it’s not stunning that as proven in Determine 9, Knowledge Encrypted for Affect (T1486) tops the chart, because it has yearly. However the remainder of the impacts, we see a possibility for defenders: The causes of lots of the different impacts are occasions that may be detected.
Determine 9: MITRE’s Affect classes change over time, however Knowledge Encrypted for Affect’s reign on the prime of the Lively Adversary charts is unbroken all through our five-year historical past, together with each IR’s and MDR’s instances this yr. (Observe that percentages add as much as over 100%, since some instances have a number of impacts)
For example, Inhibit System Restoration (T1490) is commonly invoked as a result of the menace actor deleted quantity shadow copies. Instruments like vssadmin.exe, the shadow-copy administration software (seen abused in 10% of all instances), or the WMI command line (seen abused in 24%) are used to do the deed. You may also detect when vssadmin is used to create shadow copies, which precedes its exfiltration. Likewise, we noticed attackers delete recordsdata in 26% of all instances. In that circumstance, waiting for surprising use of del.exe could also be an indication of adversary motion. Detection engineering can hear for suspicious occasions of this ilk, to listen to the noise attackers make once they’re making an attempt to trigger you hurt.
Conclusion
To the practitioners on the market, we see you. You’re doing the work and the enterprise. You additionally know the restrictions of what you’ll be able to accomplish. The excellent news is that you just don’t have to be helplessly hoping issues will get higher, particularly when assist is offered.
To the enterprise and tech leaders, give your groups an opportunity. We all know cash and sources are tight. That usually means loading up your IT workers with extra work and duty than they’ll deal with. Although it might sound self-serving coming from a analysis crew hooked up to a safety vendor, we consider IT groups must deal with how they permit the enterprise and let consultants do the soiled work of combating the attackers. As a result of one factor is obvious from the info: When there’s somebody taking note of the surroundings and they’re able to act rapidly and decisively, outcomes dramatically enhance. The choice is repeating errors from the previous. The selection is yours: You may get with this, or you will get with that. We expect you’ll get with this, for that is the place it′s at.
Acknowledgements
The authors want to thank the Sophos IR and MDR groups, Mark Loman, Chester Wisniewski, and Matt Wixey for his or her contributions to the AAR course of.
Appendix: Demographics and methodology
For this report, we targeted on 413 instances that may very well be meaningfully parsed for data on the state of the adversary panorama all through 2024. Defending the confidential relationship between Sophos and our clients is after all our first precedence, and the info herein has been vetted at a number of levels throughout this course of to make sure that no single buyer is identifiable by means of this knowledge – and that no single buyer’s knowledge skews the combination inappropriately. When unsure a few particular case, we excluded that buyer’s knowledge from the dataset.
Determine A1: We get round: It’s Sophos Incident Response and MDR at work all over the world (map generated courtesy of 29travels.com)
The next 57 nations and different areas are represented within the full dataset:
| Angola | Hong Kong | Qatar |
| Argentina | India | Romania |
| Aruba | Indonesia | Saudi Arabia |
| Australia | Israel | Singapore |
| Austria | Italy | Slovenia |
| Bahamas | Jamaica | Somalia |
| Bahrain | Japan | South Africa |
| Belgium | Kenya | South Korea |
| Bolivia | Kuwait | Spain |
| Botswana | Malaysia | Sweden |
| Brazil | Mexico | Switzerland |
| Canada | Netherlands | Taiwan |
| Chile | New Zealand | Thailand |
| Colombia | Nigeria | Turkey |
| Egypt | Panama | Turks and Caicos Islands |
| Finland | Papua New Guinea | United Arab Emirates |
| France | Philippines | United Kingdom |
| Germany | Poland | United States of America |
| Honduras | Portugal | Vietnam |
Industries
The next 32 industries are represented within the full dataset:
| Promoting | Monetary | Information Media |
| Agriculture | Meals | Non-profit |
| Structure | Authorities | Pharmaceutical |
| Communication | Healthcare | Actual property |
| Development | Hospitality | Retail |
| Training | Data Know-how | Providers |
| Electronics | Authorized | Transportation |
| Vitality | Logistics | Journey and tourism |
| Engineering | Manufacturing | Utilities |
| Leisure | Mining | Wholesale |
| Finance Providers | MSP/Internet hosting |
Methodology
The info on this report was captured over the course of particular person investigations undertaken by Sophos’ X-Ops Incident Response and MDR groups. For this primary report of 2025, we gathered case data on all investigations undertaken by the groups all through 2024 and normalized it throughout 52 fields, inspecting every case to make sure that the info out there was acceptable intimately and scope for combination reporting as outlined by the main focus of the proposed report. We additional labored to normalize the info between our MDR and IR reporting processes.
When knowledge was unclear or unavailable, the authors labored with particular person IR and MDR case results in clear up questions or confusion. Incidents that would not be clarified sufficiently for the aim of the report, or about which we concluded that inclusion risked publicity or different potential hurt to the Sophos-client relationship, have been put aside. We then dissected every remaining case’s timeline to realize additional readability on such issues as preliminary ingress, dwell time, exfiltration, and so forth. We retained 413 instances, and people are the inspiration of the report. The info supplied within the downloadable dataset has been additional redacted to make sure buyer confidentiality.