Malware analysis includes finding out risk actor TTPs, mapping infrastructure, analyzing novel methods… And whereas most of those investigations construct on current analysis, generally they begin from a hunch, one thing that appears too easy. On the finish of 2023, we stumbled upon an installer named HotPage.exe that deploys a driver able to injecting code into distant processes, and two libraries able to intercepting and tampering with browsers’ community site visitors. The malware can modify or substitute the contents of a requested web page, redirect the consumer to a different web page, or open a brand new web page in a brand new tab primarily based on sure situations.
The installer was detected by most safety merchandise as an adware part however what actually piqued our curiosity was the embedded driver signed by Microsoft. In accordance with its signature, it was developed by a Chinese language firm named 湖北盾网网络科技有限公司 (machine translation: Hubei Dunwang Community Know-how Co., Ltd), the lack of expertise about which was intriguing. The distribution methodology remains to be unclear however in accordance with our analysis, this software program was marketed as an “Web café safety resolution” geared toward Chinese language-speaking people. It purports to enhance the online searching expertise by blocking advertisements and malicious web sites, however the actuality is kind of totally different – it leverages its browser site visitors interception and filtering capabilities to show game-related advertisements. It additionally sends some details about the pc to the corporate’s server, probably to assemble set up statistics.
On prime of its apparent mischievous habits, this kernel part unintentionally leaves the door open for different threats to run code on the highest privilege degree accessible within the Home windows working system: the SYSTEM account. As a result of improper entry restrictions to this kernel part, any processes can talk with it and leverage its code injection functionality to focus on any non-protected processes.
We reported this driver to Microsoft on March 18th, 2024 and adopted their coordinated vulnerability disclosure course of. Microsoft Safety Response Heart (MSRC) decided that that is not a vulnerability because the offending driver was faraway from the Home windows Server Catalog on Could 1st, 2024. ESET applied sciences detect this risk as Win64/HotPage.A and Win64/HotPage.B.
Who’s 湖北盾网网络科技有限公司 ?
Throughout its execution, the HotPage malware installs a driver, however earlier than diving into the technical particulars of its internal workings, we needed to be taught extra in regards to the code-signing signature of this driver. What first caught our consideration was the signing certificates’s proprietor, as illustrated in Determine 1.
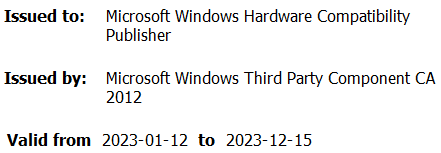
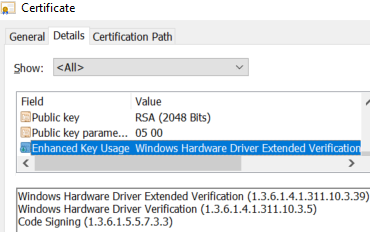
Because the 64-bit model of Home windows 7, kernel-mode drivers have been required to be signed to be loaded by the working system. As beforehand detailed by Mandiant Intelligence, SentinelLabs, and G DATA groups, the signing course of is constructed on belief however there have been instances the place this was abused. Plainly the Chinese language firm went via Microsoft’s driver code-signing necessities and managed to acquire an Prolonged Verification (EV) certificates as proven in Determine 2.
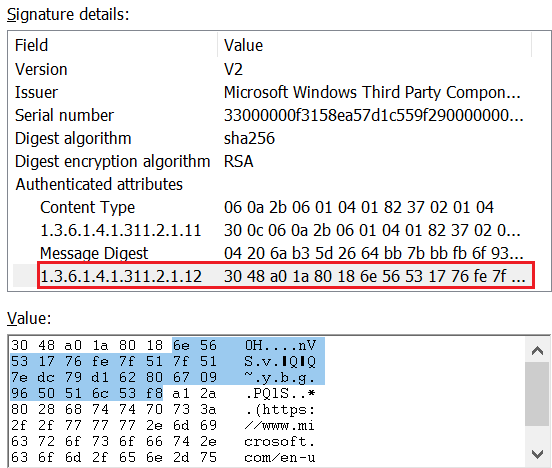
With a view to retrieve the corporate title related to this signature, the extraction of the signers’ attributes was mandatory. Determine 3 reveals the SpcSpOpusInfo attribute recognized by the thing ID 1.3.6.1.4.1.311.2.1.12.
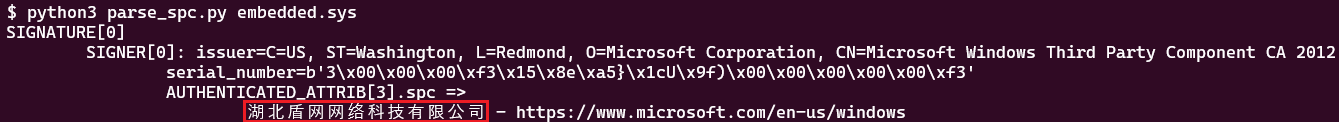
Utilizing the LIEF binary parser, it’s doable to extract the construction member programName that identifies the corporate behind this signature, as displayed in Determine 4.
We discovered a reference to this firm within the Home windows Server Catalog, as proven in Determine 5. The corporate used varied product classes when submitting its drivers for certification. Primarily based on its title, it seems the corporate developed two community filtering packages: a netfilter part and the HotPage driver referred as adsafe or by its inside title KNewTalbeBase (Word the [Tt]albe typo, which additionally happens elsewhere within the HotPage code).
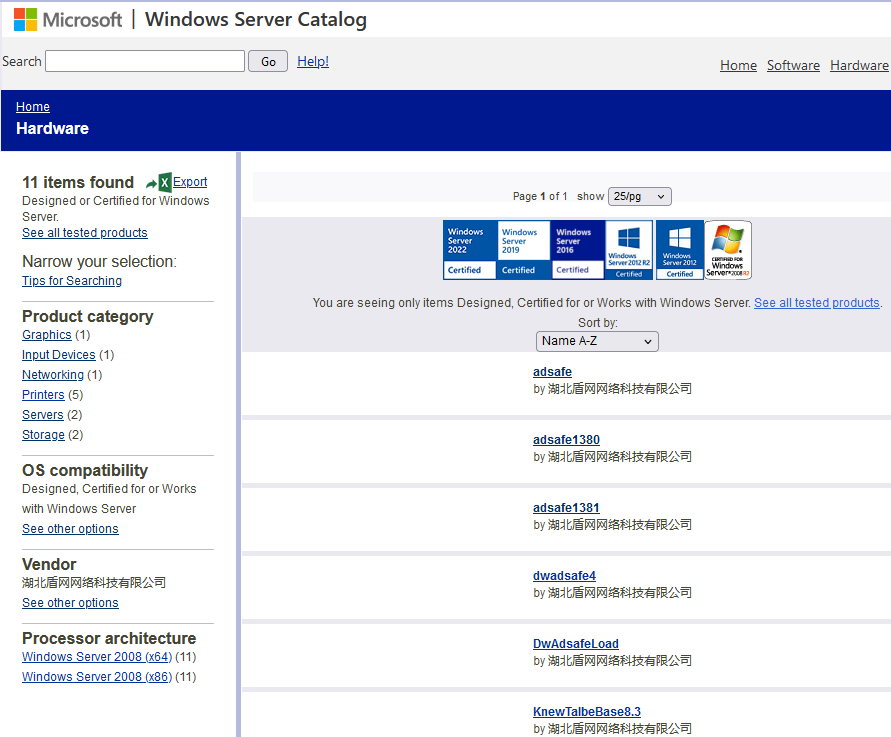
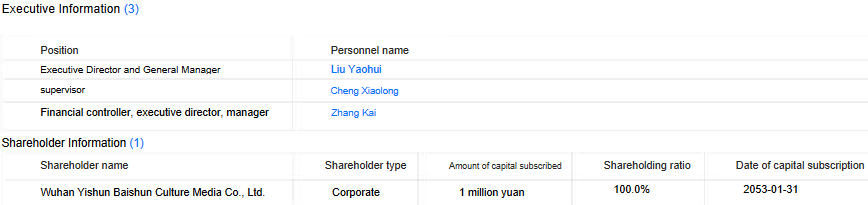
Investigating the corporate via search engines like google and yahoo didn’t yield many outcomes. In accordance with the corporate register dingtalk, we found that the corporate was created on January 6th, 2022 and offered the e-mail deal with dwadsafe@mail[.]io. The enterprise scope consists of: technology-related actions similar to growth, providers, consulting, and many others., but additionally promoting actions. As translated in Determine 6, the principal shareholder is now Wuhan Yishun Baishun Tradition Media Co., Ltd, a really small firm that appears to be specialised in promoting and advertising.
From the Mental Property tab, we discovered that in April and Could 2022 the corporate utilized for the commerce title Protect Web Café Safety Protection and the web site dwadsafe[.]com was created on February 22nd, 2022. The area now resolves to localhost (127.0.0.1) and is due to this fact inaccessible. Nonetheless, a screenshot of the web site was taken on November 10th, 2023 by a net crawler, as seen in Determine 7.
![Figure 7. Screenshot of the dwadsafe[.]com webpage made by zhizhuyinqing.com](https://web-assets.esetstatic.com/wls/2024/7-2024/hotpage/figure-7-screenshot-of-the-dwadsafe-com-webpage-made-by-zhizhuyinqing-com.png)
The HTTP physique of the URL https://www.dwadsafe[.]com/login/reg.html (SHA-1: 744FFC3D8ECE37898A0559B62CC9F814006A1218) was additionally captured by VirusTotal. The supply code accommodates the outline 网吧主动防御云平台 (machine translation: Web café energetic protection cloud platform). This web page features a license settlement that particulars the aim of the software program, albeit with contradictions. Desk 1 lists some attention-grabbing bits of that info.
Desk 1. Translation of the related elements of the license settlement
|
Authentic textual content |
Translated textual content (by way of Google Translate; emphasis ours) |
|
6、DwAdsafe作为一款主动防御系统,自身并不具有任何拦截功能,单独运行本软件不会对现有任何软件或者程序有拦截、破坏、修改等操作,也不会拦截任何病毒程序。用户只有在编写相关过滤规则后,才会开始生效;用户可以根据自己的实际需要,选择是否使用这些规则. |
6. As an energetic protection system, DwAdsafe doesn’t have any interception perform. Working this software program alone won’t intercept, destroy or modify any current software program or packages, nor will it intercept any virus packages. Solely after customers write related filtering guidelines will they take impact; customers can select whether or not to make use of these guidelines in accordance with their precise wants. |
|
7、DwAdsafe是应用户的强烈需求而开发的:目前,有部分软件和网站的广告对用户存在较大的骚扰和误导,严重影响用户的上网体验。应广大用户提出要求,本公司开发并提供网吧环境下的安全监视、监控、过滤等功能的软件——DwAdsafe。DwAdsafe中所有的过滤规则均由网友提供并共享,通过DwAdsafe发布。用户可以根据自己的实际需要,选择是否使用这些功能。 |
7. DwAdsafe was developed in response to the robust wants of customers: At current, the ads of some software program and web sites are fairly harassing and deceptive to customers, critically affecting customers’ on-line expertise. In response to requests from customers, our firm develops and supplies software program for safety monitoring, monitoring, filtering and different features in Web café environments – DwAdsafe. All filtering guidelines in DwAdsafe are offered and shared by netizens and printed via DwAdsafe. Customers can select whether or not to make use of these features in accordance with their precise wants. |
|
8、DwAdsafe是主动防御型软件,故包括但不限于拦截、监视、删除、结束等功能。使用DwAdsafe会对计算机信息系统的部分或全部有对应的控制及处理权限, |
8. DwAdsafe is an energetic protection software program, so it consists of however just isn’t restricted to interception, monitoring, deletion, termination and different features. Utilizing DwAdsafe could have corresponding management and processing authority over half or the entire laptop info system. |
In accordance with the license settlement, the software program is certainly marketed as a safety resolution for web cafés to dam advertisements. Nonetheless, regardless of the corporate’s claims that DwAdsafe doesn’t have any interception functionality, our investigation revealed that the software program does have a somewhat intrusive one and comes with pre-written, unmodifiable guidelines.
Aside from these bits of data, the corporate behind this malicious part stays a thriller.
HotPage evaluation
On this part we describe how the totally different elements are put in and work together with one another to realize their objective: injecting advertisements into the browser. Thus far, we haven’t discovered how the malware was distributed however we imagine, with low confidence, that it might need been bundled with one other software program bundle or marketed as a safety product as a result of degree of privileges wanted to put in the motive force. A number of references promoting the product had been present in some boards in 2022; an instance is seen in Determine 8.
![Figure 8. Mention of dwadsafe[.]com in a forum dedicated to Internet café maintenance Figure 8. Mention of dwadsafe[.]com in a forum dedicated to Internet café maintenance](https://web-assets.esetstatic.com/wls/2024/7-2024/hotpage/figure-8-mention-of-dwadsafe-com-in-a-forum-dedicated-to-internet-cafe-maintenance.png)
The installer drops the motive force on disk and begins a service to execute it. It decrypts its configuration file, which accommodates a listing of goal Chromium-based browsers and libraries. If such executables are discovered working or being loaded, the motive force tries to inject one of many listed libraries into the browser course of. After hooking network-based Home windows API features, the injected library checks the URL being accessed and beneath sure situations, it shows one other web page to the consumer via various means.
The installer
The installer we analyzed (SHA-1: 941F0D2D4589FB8ADF224C8969F74633267B2561) is a UPX-compressed file that was uploaded to VirusTotal on 2023-08-26. Determine 9 supplies a high-level overview of the motive force set up.
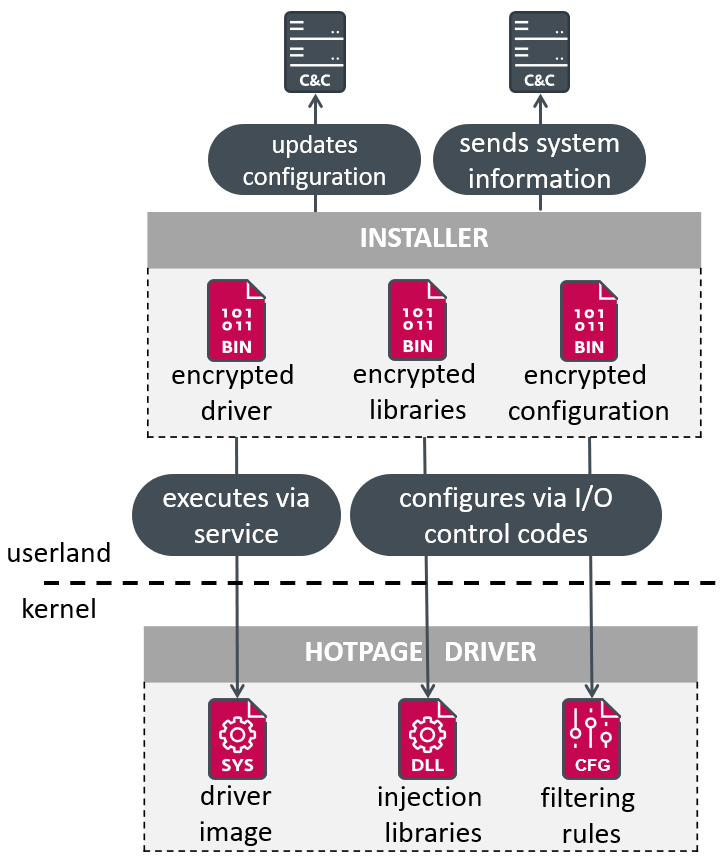
The installer accommodates the encrypted variations (single-byte XOR operation with the important thing 0xE3) of the motive force part, the libraries that might be injected into net browser processes, and three JSON-formatted configuration recordsdata:
- chromedll accommodates the names of the focused browser libraries to hook and the focused features’ sample for hooking them,
- hotPage (unused) accommodates the record of focused browsers, allowlists of command line parameters and web sites, and the homepage URL that may very well be used, and
- newtalbe accommodates filtering guidelines, an API endpoint to ship fundamental details about the compromised laptop, and one other one to handle configuration updates.
The malware begins by executing the CPUID instruction (see Hypervisor Discovery), to verify whether or not it’s working inside a virtualized setting. Then it checks if the motive force’s system filename .KNewTableBaseIo exists and if not, it decrypts the motive force and shops it in C:WindowsShieldNetWorkBusiness. Its title is a randomly generated 7-character string adopted by the .sys extension. A service is created with the file path of the saved driver, and the random string is used because the service title. Because the begin sort is about to SERVICE_DEMAND_START, the service must be explicitly began so as to load the motive force. Oddly, this adware doesn’t implement any persistence mechanisms, or no less than not on this model.
The installer proceeds to speak with and configure the motive force by way of its system filename utilizing I/O management codes within the following order:
- 0x9C4013FC – ship the 32-bit hooking library that might be injected into goal net browser processes.
- 0x9C400FFC – ship the 64-bit hooking library that might be injected into goal net browser processes.
- 0x9C40173C – ship the chromedll configuration.
The installer retrieves the registry key related to the created service and checks to see if the values IP and port are current. These values are by no means set by this code so they’re presumably created by one other part. With out going into the main points of the community protocol, the distant server ought to serve an replace of the newtalbe configuration. The communication is encrypted with RC4, utilizing a key derived from the string ID:f~WdH+Ok?KD)r*sD4mk utilizing the Home windows BCryptGenerateSymmetricKey perform. Determine 10 reveals the content material of the configuration file.
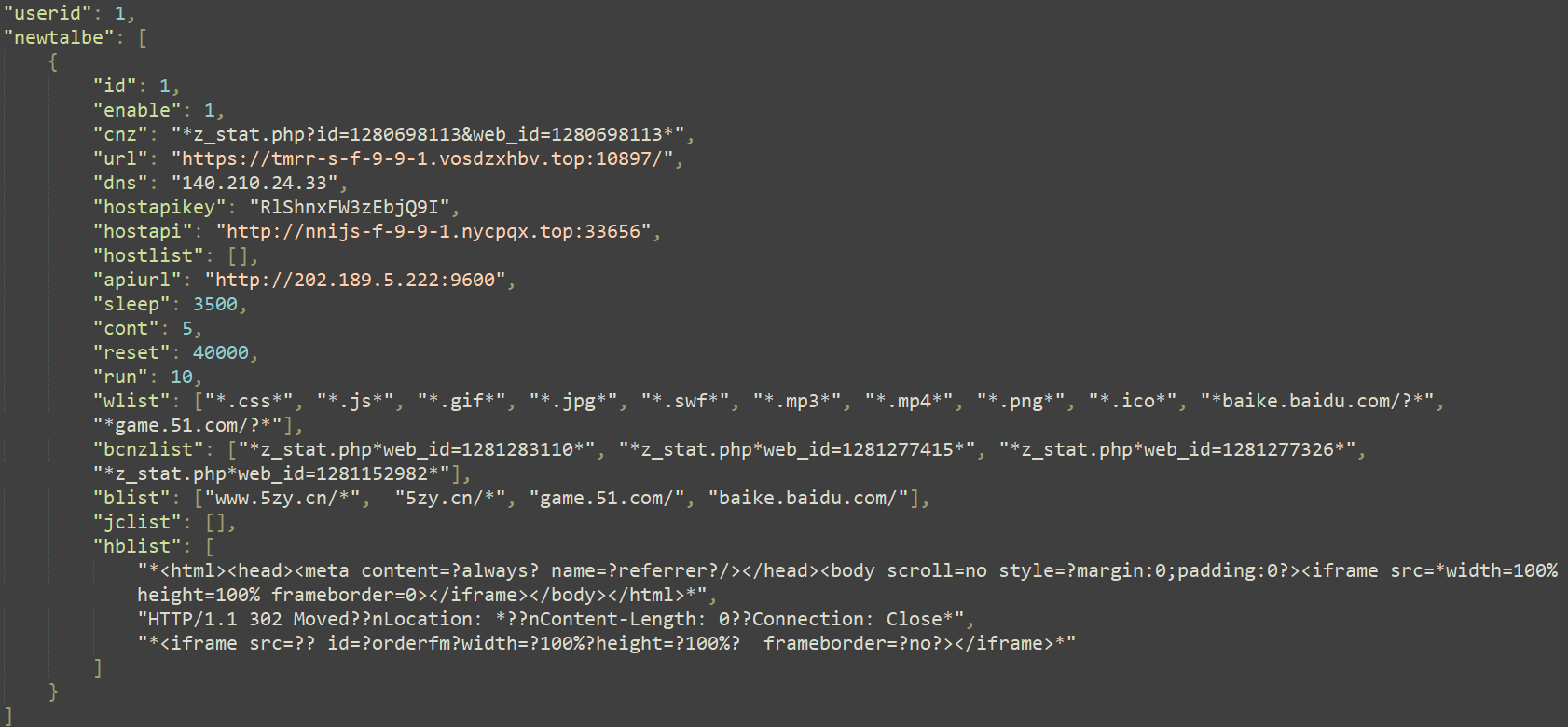
Desk 2 describes the necessary values used from this file, listed within the order that they seem within the configuration file (Determine 10).
Desk 2. newtalbe configuration description
|
Worth |
Description |
|
cnz |
URI sample matching URLs used to gather statistics when visiting the URL specified by the url worth. |
|
url and dns |
If one of many URLs listed in blist is being accessed, a brand new tab pointing to the url worth might be opened. The dns worth is IP deal with of the area. |
|
hostapikey, hostapi, |
The URL worth of hostapi is used to replace the hostlist, a dictionary comprised of game-related domains together with their corresponding IP addresses. The hostapikey is the decryption key. |
|
apiurl |
Listing of endpoints to ship details about the compromised laptop to. |
|
Wlist, |
Lists of patterns (URI, domains, file extensions, HTML code, and HTTP response headers) to match to use redirection guidelines (see the Hooking NtDeviceIoControlFile and inspecting incoming and outgoing knowledge part). |
Utilizing the hostapi URL worth of this file, an HTTP GET request is remodeled TLS with a generic Person-Agent string. The acquired knowledge is decrypted utilizing RC4 with the hostapikey worth; it accommodates a dictionary of gaming-related hostnames with their corresponding resolved deal with.
As soon as these updates are completed, the installer sends the up to date newtalbe configuration to the motive force by issuing an I/O request with the management code 0x9C400BFC.
Lastly, the malware iterates over the record of endpoints offered by the JSON component apiurl and for every certainly one of them it creates a JSON-formatted string containing details about the compromised laptop, encrypts it with RC4 utilizing the important thing Abc123!@#&XM derived by way of the Home windows API BcryptGenerateSymmetricKey, and sends the collected info to the distant server by way of an HTTP POST request. The collected info consists of the pc title, the community interface MAC deal with, the model of the working system, and the size of the display screen.
Injector driver
The motive force’s predominant objective is to inject libraries into browser purposes and alter their execution stream to alter the URL being accessed or open a web page in a brand new tab. Two threads are created to deal with requests for opening a brand new tab and injecting libraries utilizing the publicly accessible Blackbone undertaking. Moreover, course of creation and picture loading notification routines are set to watch newly created processes and executable photographs being loaded. The simplified logic of the motive force is illustrated in Determine 11.
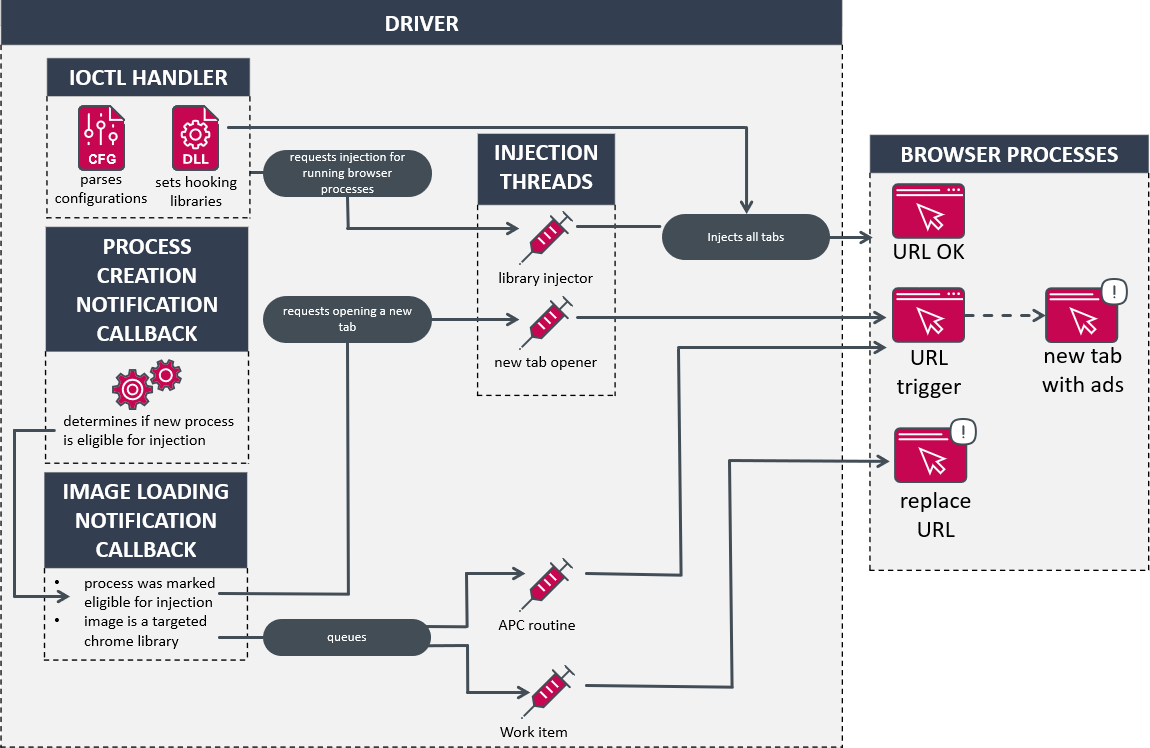
For an unknown cause, the motive force begins by deleting its picture from the disk. Afterwards it creates a tool object named .KNewTableBaseIo and units its IRP_MJ_DEVICE_CONTROL routine to deal with the assorted I/O requests listed in Desk 3. The management codes (IOCTL) used for configuration or setting the injected libraries can solely be known as as soon as; due to this fact the settings can’t be up to date. These particular management codes are protected by checking that the caller’s file path matches the common expression *ShieldNetWorkEnterpriseDwBusiness_*.
Desk 3. Listing of accessible IOCTLs and their description
|
IOCTL |
Motion |
|
0x9C400BFC |
Parses the newtalbe configuration handed as an argument. |
|
0x9C400FFC |
Units the 64-bit library to be injected. |
|
0x9C4013FC |
Units the 32-bit library to be injected. |
|
0x9C40173C |
Parses the chromedll configuration handed as an argument. |
|
0x9C401EC4 |
Receives a listing of browser tabs (processes) to kill. |
|
0x9C4027A8 |
Returns the hotPage configuration. |
|
0x9C4027AC |
Returns the scale of the hotPage configuration. |
|
0x9C4027E8 |
Returns the newtalbe configuration. |
|
0x9C4027EC |
Returns the scale of the newtalbe configuration. |
|
0x9C4027FC |
Parses the hotPage configuration handed as an argument. |
When dealing with the management codes 0x9C400BFC and 0x9C40173C, the motive force iterates over the loaded modules of all of the working processes. If one of many focused modules listed within the chromedll configuration is discovered, a request to inject a library into that course of is queued.
Lastly, the motive force ends its initialization by creating two threads and setting the notification routines talked about above.
You will need to observe that the hotPage configuration is rarely set. Any mentions of this file are solely made to explain how it will be used in accordance with the motive force’s management stream. Primarily the hotPage configuration is used to redirect the consumer to a particular web page (or homepage) stuffed with advertisements when a focused browser is launched.
The model of the software program we analyzed relied solely on the chromedll and newtalbe configurations to realize its advert injection.
Library injection thread
This thread checks the queued injection requests, and for every of them, it attaches itself to the focused course of by way of KeStackAttachProcess, allocates chunks of reminiscence, and copies its shellcode. Utilizing the Blackbone library perform ZwCreateThreadEx, the motive force calls the shellcode, which implements its personal PE loader and calls the entry level of the injected library.
New tab thread
The second thread makes use of the identical logic; nonetheless, the injected shellcode is totally different. It calls the Home windows API perform CreateProcessW with the command line parameter being the method title of the focused course of concatenated with the URL that needs to be opened. The latter is fabricated from the URL adopted by the sum of the idindex and the userid variables from the hotPage configuration. As an illustration, the configuration proven in Determine 12 would create the string https://www.hao774[.]com/?90386-00001. Since Chromium-based browsers create a brand new course of for every new tab, making a course of from the browser course of will successfully create a brand new tab.
Determine 12 reveals the content material of the hotPage configuration file.
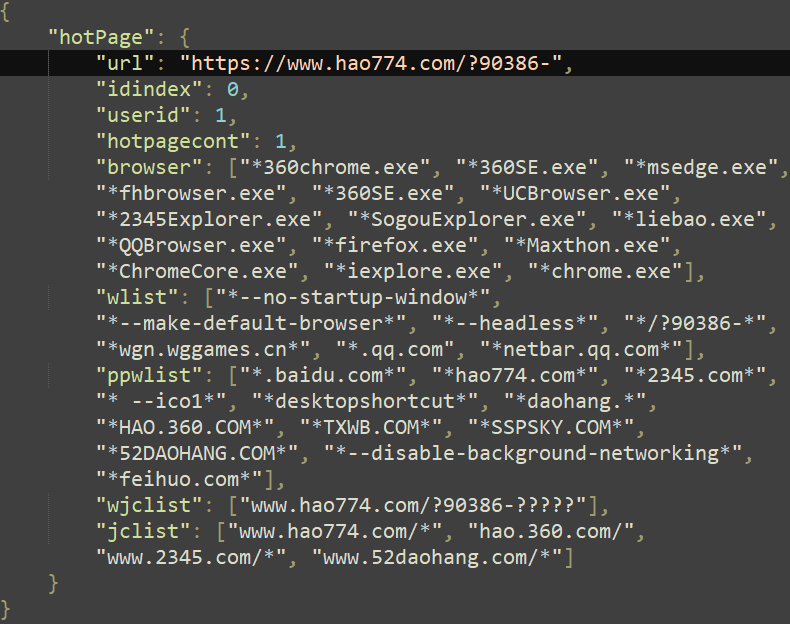
This configuration file accommodates the record of focused net browsers and command line parameters that decide whether or not the method needs to be injected. The domains are both associated to gaming advertisements or web café upkeep.
Course of creation notification routine
Primarily, this routine makes certain the homepage of the brand new net browser occasion is redirected to a particular URL current within the hotPage configuration. This part describes how the motive force implements this characteristic even when it’s not used, since this model of the installer by no means sends this configuration to the motive force.
Relying on the next situations, the online browser course of might be marked as eligible for opening the URL within the hotPage configuration:
- that is the primary occasion of the browser and never a brand new tab being opened,
- the method’s file path matches one of many common expressions within the browser record within the hotPage configuration,
- the command line of the method doesn’t match any common expression within the wlist record of the hotPage configuration, and
- if the method’s command line consists of its personal file path, it should not match any common expressions within the ppwlist record of the hotPage configuration.
As detailed within the subsequent part, when the browser course of begins loading the primary executable photographs, a request to open a brand new tab is queued. Determine 13 and Determine 14, respectively, present the distinction between the authentic net listing 2345[.]com and the ad-riddled web page exhibited to the consumer.
![Figure 13. Legitimate main page of the web directory 2345[.]com Figure 13. Legitimate main page of the web directory 2345[.]com](https://web-assets.esetstatic.com/wls/2024/7-2024/hotpage/figure-13-legitimate-main-page-of-the-web-directory-2345-com.png)
![Figure 14. Ad-riddled page mimicking the homepage of 2345[.]com Figure 14. Ad-riddled page mimicking the homepage of 2345[.]com](https://web-assets.esetstatic.com/wls/2024/7-2024/hotpage/figure-14-ad-riddled-page-mimicking-the-homepage-of-2345-com.png)
Picture loading notification routine
This routine basically handles two forms of situations. If the picture being loaded is within the chromedll record, an APC routine is queued that may load one of many hooking libraries by way of its personal PE loader.
In any other case, if the method was marked eligible for opening a brand new web page, the malware achieves this both by opening it in a brand new tab or within the present one. If the method filename matches one of many common expressions within the browser1 record of the hotPage configuration, a request to open a brand new tab is queued and might be dealt with by the suitable thread (observe that the browser1 record component was not current within the configuration file we retrieved). Within the different case, the web page might be opened within the tab being created by queuing a piece merchandise (by way of IoQueueWorkItemEx) that may modify the command line of the method being created. The latter attaches itself to the method, finds the export deal with of GetCommandLineA and GetCommandlineW contained in the kernelbase.dll library, and modifies the Unicode string saved in BaseAnsiCommandLine. The command line is changed with the method’s executable file path concatenated with the URL within the hotPage configuration. Determine 15 reveals a side-by-side comparability of the code chargeable for discovering the command line buffer and the disassembly of the GetCommandLineA perform.
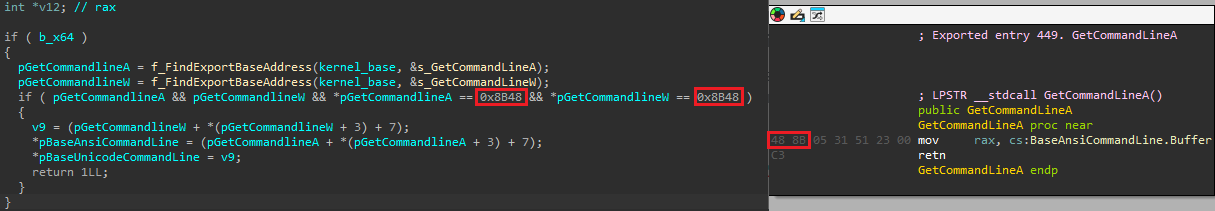
Injected library
The very first thing that the injected library does is to retrieve the hotPage and newtalbe configurations by querying the motive force. If the injected browser filename is 360Chrome, it deletes the registry key HKCUSoftware360chromeHomepage and patches the Preferences file (positioned beneath the browser’s default listing 360chromechromeUser DataDefaultPreferences) to make the homepage level to the URL worth of the hotPage configuration.
Utilizing the Microsoft Detours hooking library, the pattern hooks SetProcessMitigationPolicy to make it return 1 so as to stop safety insurance policies from being utilized to the method, thereby permitting code injection. Then getaddrinfo is hooked to pressure the browser to resolve sure hostnames to particular IP addresses to make sure the redirection is made to the appropriate server in case the domains don’t exist anymore.
Hooking SSL_read and SSL_write
The malware hooks the SSL_read and SSL_write features to permit the manipulation of the browser’s decrypted TLS site visitors; it does so by looking for particular patterns contained in the loaded modules, since these features will not be exported. As an illustration, the chromewrite dictionary contained in the chromedll configuration accommodates two forms of patterns, sslcode and oldchrome, as seen in Determine 16. They’re, respectively, used for locating newer and older variations of the DoPayloadWrite perform. We examined and confirmed that the patterns match the Microsoft Edge library msedge.dll model 122.0.2365.80.
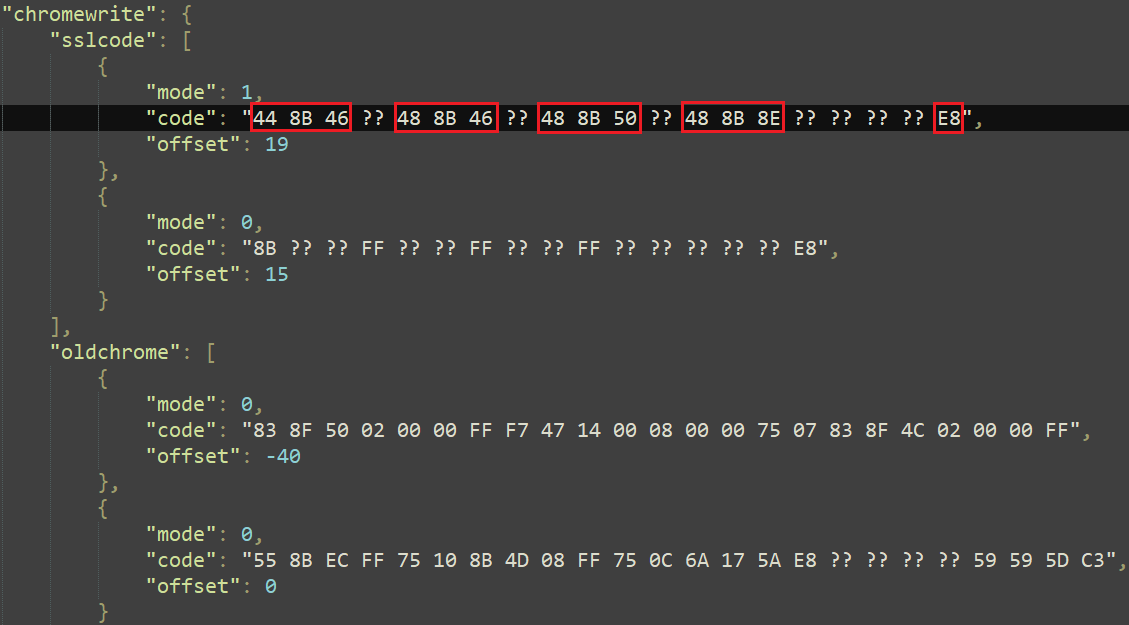
The mode worth is used to find out the model of the sample, both 32-bit or 64-bit; the code worth is the precise byte sample, and the offset is the gap from the beginning of the sample to the pointer to the SSL_write perform (see Determine 17).
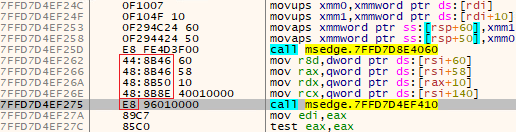
As soon as SSL_write and SSL_read are discovered, they’re hooked utilizing the Detours library. For the previous, the malware inspects the info after which calls the unique perform, which encrypts and sends it. As for the latter, the injected library does the other so as to manipulate decrypted knowledge. For each features, the info is inspected by the code that respectively handles the AFD_SEND and AFD_RECV management codes within the perform hooking NtDeviceIoControlFile.
Hooking NtDeviceIoControlFile and inspecting incoming and outgoing knowledge
The malicious library hooks the NtDeviceIoControlFile perform to deal with particular IOCTL codes as seen in Determine 18.
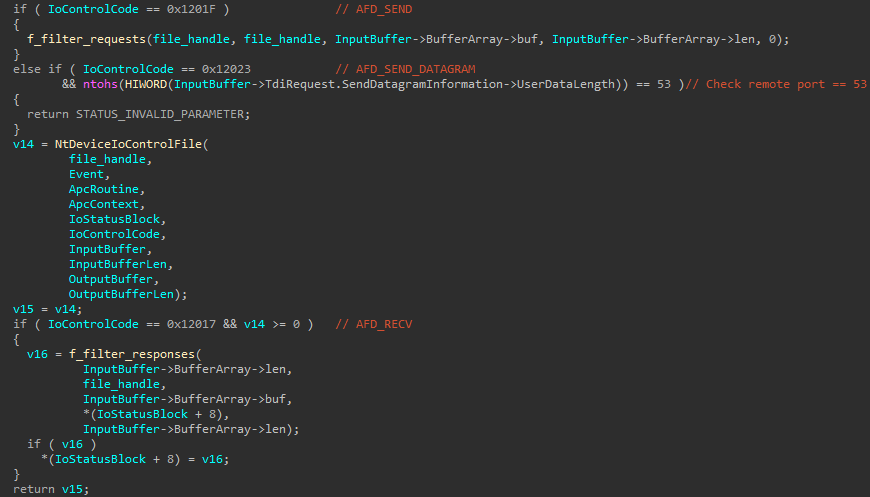
For the management code 0x12023 (AFD_SEND_DATAGRAM used when sending UDP packets), the malware cancels any DNS requests by returning STATUS_INVALID_PARAMETER if the distant port quantity is 53. This ensures that the online browser solely makes use of the hosts offered by the newtalbe configuration.
The routine that handles the management code 0x1201F (AFD_SEND) begins by extracting the URL and the Referrer header from the request. Primarily based on the URL matching sure values within the newtalbe and hotPage configurations, the malware performs assorted actions, as described in Desk 4. In some instances, the request is shipped however the response is modified within the routine dealing with the AFD_RECV management code by totally different redirection strategies defined afterwards.
Desk 4. Listing of actions carried out beneath sure situations when sending HTTP requests
|
Configuration |
Matching worth |
Motion |
|
newtalbe |
cnz |
Sends information in regards to the compromised laptop to the apiurl (just like the top of the installer). |
|
hotPage |
whomepage |
Will increase inside homepage hit counter. |
|
hotPage |
wjclist |
Sends the info with none modifications. |
|
newtalbe |
url or wlist |
Sends the info with none modifications. |
|
newtalbe |
blist |
Sends the info however modifies the response utilizing redirection methodology 0. The response is opened in a brand new browser tab. |
|
newtalbe |
jclist |
Sends the info however modifies the response utilizing redirection methodology 1. |
|
newtalbe |
bcnzlist |
Sends the info however modifies the response utilizing redirection methodology 2. |
|
hotPage |
jclist |
Sends the info however modifies the response utilizing redirection methodology 3. |
For management code 0x12017 (AFD_RECV), the malware first retrieves the info acquired by the shopper and checks if the response was marked eligible for redirection. There are 4 forms of redirections as described in Desk 5. The xxx string within the modified response is modified for the URL within the newtalbe configuration.
Desk 5. Redirection strategies
|
Redirection methodology |
Modified response |
Description |
|
0 |
HTTP/1.1 302 Moved Briefly Server: nginx Content material-Kind: textual content/html Connection: shut Location: xxx |
Redirect the consumer to a different web page utilizing the HTTP code 302; an inside redirection counter is incremented. |
|
1 |
<html><head><meta charset=”utf-8″><meta content material=”at all times” title=”referrer”></head><physique scroll=no fashion=”margin:0;padding:0″><iframe src=”https://www.welivesecurity.com/en/eset-research/hotpage-story-signed-vulnerable-ad-injecting-driver/xxx” width=100% peak=100% frameborder=0></iframe></physique></html> |
Change the content material of the present web page with an iframe pointing to a brand new URL. |
|
2 |
location.substitute(“https://www.welivesecurity.com/en/eset-research/hotpage-story-signed-vulnerable-ad-injecting-driver/xxx”) |
Redirect the present web page utilizing the substitute methodology of the Location interface. |
|
3 |
HTTP/1.1 302 Moved Briefly Server: nginx Content material-Kind: textual content/html Connection: shut Location: xxx |
Identical as redirection 0 however the redirection counter just isn’t incremented. |
Determine 19 illustrates redirection methodology 0 being utilized after navigating to a URL matching one of many blist URL patterns of the newtalbe configuration (www.5zy[.]cn). One other tab is opened and factors to the url laid out in the identical configuration.
Safety points and privilege escalation
When initializing its system object, the motive force doesn’t specify any entry management lists (ACLs) to limit who can talk with it; due to this fact, anybody can ship I/O requests to it. As talked about beforehand, some I/O management codes require the requesting course of to be in a path matching the regex:
*ShieldNetWorkEnterpriseDwBusiness_*
That is clearly not ample to verify whether or not the speaking course of is likely one of the HotPage elements and may simply be bypassed by creating the required directories beneath a user-writable folder.
We got here up with two situations that may permit a consumer with the HotPage driver working on their system to run code because the NT AUTHORITYSystem account. We created a proof-of-concept (PoC) script in Python to realize each situations.
State of affairs #1: Privilege escalation by way of arbitrary DLL injection in arbitrary processes
On this first situation, we assume that the motive force was loaded however that the chromedll configuration and the libraries to inject it weren’t set. In that case, it’s doable to create and set our personal library to inject. We created a small library that may merely log the PID of the injected course of, whether or not it’s working with administrator privileges, and the injected course of’s file path.
As seen within the screenshot of the log file in Determine 20, a variety of processes had been injected with our library together with processes with administrator privileges.
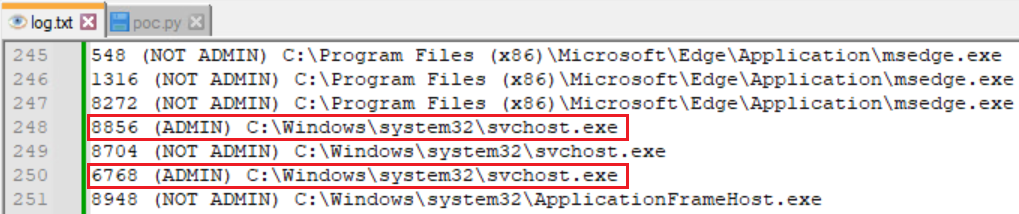
It needs to be famous, nonetheless, that protected processes can’t be injected utilizing this system.
State of affairs #2: Privilege escalation by way of altering the command line of newly created processes
Within the first situation, we relied on the truth that each the injected libraries and the chromedll configuration weren’t set, however, as seen within the installer evaluation, they’re each set as quickly as the motive force is initially loaded. Nonetheless, the hotPage configuration by no means will get set. Primarily based on the management stream evaluation, we devised a option to leverage the motive force’s course of creation and picture loading notification routines’ logic to execute the identical executable once more however with a distinct command line.
Beneath sure situations, as defined within the Course of creation notification routine and Picture loading notification routine sections, the motive force can open a brand new tab pointing to the URL current within the hotPage configuration. That is achieved both by changing the command line of the newly created browser course of or by duplicating the browser course of and altering its command line to the URL within the hotPage configuration. If we specify which course of may be duplicated and the brand new command line, we are able to obtain privilege escalation by concentrating on a course of with SYSTEM privileges, as an example.
Conclusion
The evaluation of this somewhat generic-looking piece of malware has confirmed, as soon as once more, that adware builders are nonetheless prepared to go the additional mile to realize their targets. Not solely that, these have developed a kernel part with a big set of methods to control processes, however in addition they went via the necessities imposed by Microsoft to acquire a code-signing certificates for his or her driver part.
The HotPage driver reminds us that abusing Prolonged Verification certificates remains to be a factor. As a variety of safety fashions are in some unspecified time in the future primarily based on belief; risk actors are inclined to play alongside the road between authentic and shady. Whether or not such software program is marketed as a safety resolution or just bundled with different software program, the capabilities granted because of this belief expose customers to safety dangers.
As annoying as adware may be, the vulnerabilities launched by this malware go away the system open to much more harmful threats. An attacker with a non-privileged account may leverage the weak driver to acquire SYSTEM privileges or inject libraries into distant processes to trigger additional injury, all whereas utilizing a authentic and signed driver.
ESET applied sciences detect this risk – which Microsoft faraway from the Home windows Server Catalog on Could 1st, 2024 – as Win64/HotPage.A and Win64/HotPage.B.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis affords personal APT intelligence studies and knowledge feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
A complete record of IoCs and samples may be present in our GitHub repository.
Information
|
SHA-1 |
Filename |
Detection |
Description |
|
0D1D298A3EBCA4ECE0BA |
N/A |
Win64/HotPage.B |
HotPage driver. |
|
DDD82422D418FC8E8748 |
N/A |
Win32/HotPage.B |
32-bit HotPage hooking library. |
|
D5D646B052E8B2572399 |
N/A |
Win64/HotPage.A |
64-bit HotPage hooking library. |
|
941F0D2D4589FB8ADF22 |
Hotpage.exe |
Win32/HotPage.A |
HotPage installer. |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
61.147.93[.]49 |
nnijs-f-9-9-1.nycpqx[.]prime |
CHINATELECOM JiangSu YangZhou IDC. |
2023-10-06 |
Server used to acquire a listing of game-related domains with their corresponding IP addresses. |
|
140.210.24[.]33 |
tmrr-s-f-9-9-1.vosdzxhbv[.]prime |
CHINATELECOM JiangSu YangZhou IDC. |
2023-10-06 |
Compromised customers are redirected to this net server that hosts ad-riddled pages. |
|
202.189.5[.]222 |
N/A |
Shandong eshinton Community Know-how Co., Ltd. |
2023-10-06 |
Former DwAdsafe area used to gather details about installations. |
MITRE ATT&CK methods
This desk was constructed utilizing model 15 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Identify |
Description |
|
Useful resource Improvement |
Receive Capabilities: Code Signing Certificates |
DwAdsafe’s driver is signed with a legitimate code-signing certificates. |
|
|
Execution |
Person Execution: Malicious File |
The installer part is an executable software. |
|
|
System Companies: Service Execution |
DwAdsafe’s driver is loaded by making a service. |
||
|
Persistence |
Hijack Execution Circulate: KernelCallbackTable |
DwAdsafe’s driver installs kernel callbacks to watch loaded photographs and course of creation. |
|
|
Protection Evasion |
Course of Injection: Asynchronous Process Name |
DwAdsafe’s driver can use APC as an injection methodology. |
|
|
Subvert Belief Controls: Code Signing |
DwAdsafe’s driver is signed with a legitimate code-signing certificates. |
||
|
Deobfuscate/Decode Information or Info |
The embedded configuration recordsdata are encrypted. |
||
|
Course of Injection: Dynamic-link Library Injection |
DwAdsafe can hijack net browser processes’ management stream by injecting DLLs. |
||
|
Obfuscated Information or Info: Embedded Payloads |
DwAdsafe’s driver and hooking libraries are embedded contained in the installer. |
||
|
Indicator Elimination: File Deletion |
DwAdsafe’s driver deletes itself from disk. |
||
|
Obfuscated Information or Info: Software program Packing |
DwAdsafe’s installer is full of UPX. |
||
|
Discovery |
System Proprietor/Person Discovery |
DwAdsafe’s installer and the hooking libraries acquire the sufferer’s username. |
|
|
Assortment |
Browser Session Hijacking |
DwAdsafe’s hooking libraries can intercept and tamper with community site visitors inside net browser processes. |
|
|
Command and Management |
Utility Layer Protocol: Net Protocols |
The HTTP protocol is used to ship collected details about the consumer and laptop to the C&C. |
|
|
Encrypted Channel: Symmetric Cryptography |
The RC4 encryption algorithm is used for encrypting communication with the C&C. |
||
|
Influence |
Knowledge Manipulation: Transmitted Knowledge Manipulation |
DwAdsafe’s hooking libraries can intercept and tamper with community site visitors inside net browser processes. |


