Safety insurance policies are offered in macOS to limit which apps can run outdoors of the same old protecting system insurance policies. Here is how macOS Sequoia can override system insurance policies in some instances.
Apple’s macOS is among the most safe working programs on this planet. Even so, no working system is foolproof, and safety breaches are nonetheless attainable.
Previously decade, Apple has added a number of further safety features to macOS which helps enhance safety. These embody however should not restricted to:
- Developer ID
- Gatekeeper
- App Notarization
- Digital app signatures
- System Integrity Safety (SIP)
Developer ID and Gatekeeper are two app-related safety features that confirm and authorize Mac apps so as to permit or disallow them from working. Gatekeeper prevents apps from working except they’re confirmed to come back from a registered Apple developer or the Mac App Retailer.
It is also attainable for Developer ID-only apps to run when downloaded outdoors the Mac App Retailer, if they have been verified by Apple.
Gatekeeper is what causes the “Verifying” progress window to seem within the Finder the primary time you run a newly downloaded app. This window seems as Gatekeeper verifies the signed digital receipts of all of an app’s parts on its first run.
In macOS’s System Settings app, you’ll be able to choose whether or not to permit solely Gatekeeper-verified (App Retailer) apps to run. You too can permit Gatekeeper and apps from registered Apple builders through Developer ID.
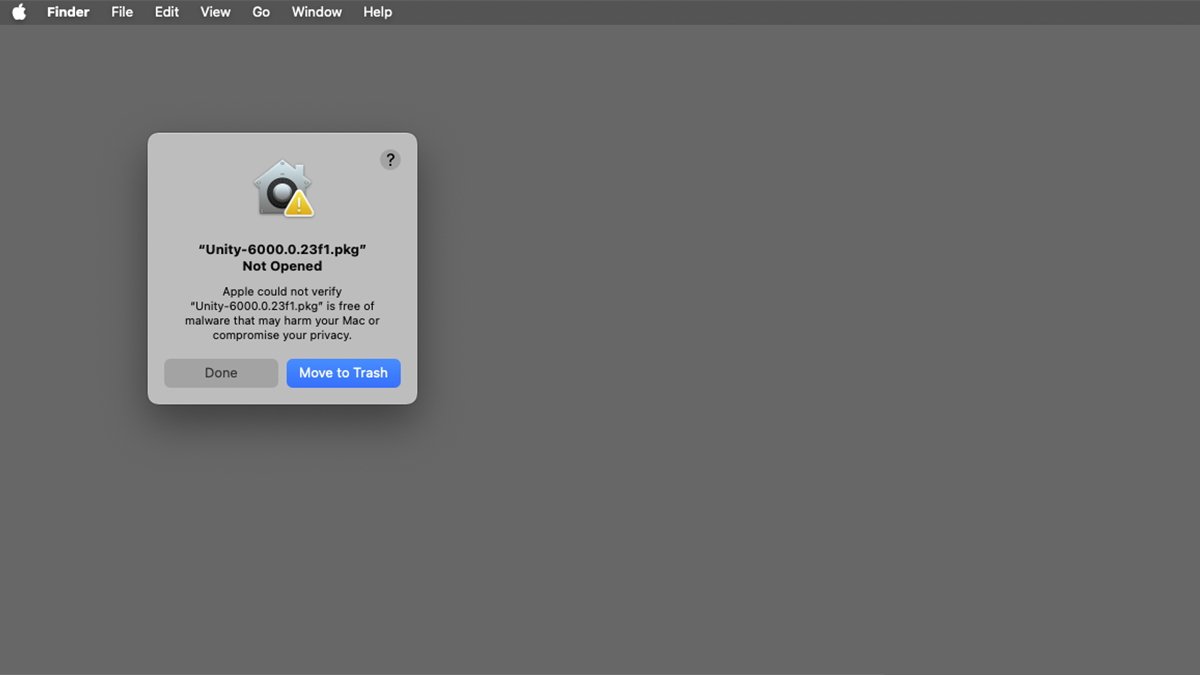
Should you attempt to run a macOS app with out both of those safety features, you will get an alert within the macOS Finder telling you the app cannot be opened. To override this warning, you will click on Carried out, then return to System Settings->Privateness & Safety and click on the Open Anyway button:
App Notarization provides safety to Mac apps and disk pictures by having Apple confirm they do not comprise malicious parts.
A digital app signature is an encrypted signing of a Mac app on the time it’s constructed by the developer, and when it’s downloaded from the Mac App Retailer. Digital signatures guarantee an app is not faux – and that its contents have not been tamped with after distribution.
System Integrity Safety (SIP) is a system-wide safety function Apple added to macOS 10.11 El Capitan in 2015. SIP protects essential working system information from being tampered with, in addition to components of macOS even from the foundation UNIX consumer, ought to it’s enabled.
SIP might be disabled and re-enabled in macOS’s Terminal app, however Apple would not suggest doing so because it opens your Mac as much as safety dangers.
Collectively, these safety parts are often called Runtime Safety in macOS.
Terminal apps
Apple gives different runtime protections for standalone binary apps, which run the Terminal app. These embody prolonged attributes (xattrs) and different system-level protections.
Some command-line Terminal apps will not be allowed to run with the default system safety insurance policies. Apple does this to guard customers from unverified malicious third-party command-line Terminal instruments.
These restrictions solely apply to some apps.
In some instances, atypical double-clickable macOS apps could must run separate command-line instruments or different software program parts.
Enabling apps to run different apps
If you need to have the ability to run an app that should run outdoors of the macOS system safety insurance policies in macOS Sequoia, head again to the System Settings->Privateness & Safety pane. You must verify every subpage for a swap to allow it.
For instance, some command-line developer instruments must run outdoors system safety insurance policies to run different instructions, course of information, or carry out different restricted actions.
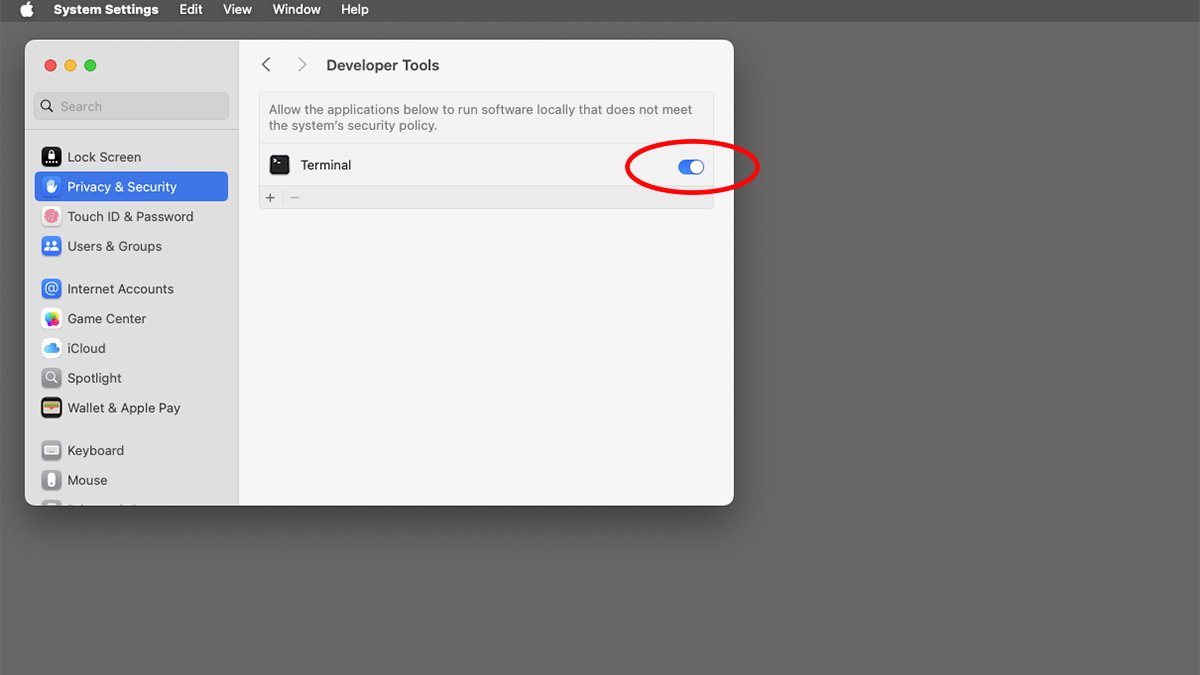
On this instance, go to System Settings->Privateness & Safety->Developer Instruments pane and you will see the next swap:
Sadly in macOS, there’s presently no option to allow this machine-wide, and there in all probability should not be since it might topic your Mac to different safety dangers.
However it’s attainable to allow this on an app-by-app foundation – if an app in query helps it. Once more, this function will not be out there to all apps so you will must verify each individually.
Usually you will not must override macOS safety insurance policies, however for some apps in sure instances, you would possibly wish to.
For an entire abstract of Gatekeeper, Developer ID, and utilizing System Settings for opening apps, see Apple’s Technote 102445, Safely open apps in your Mac.