A safety researcher has found that the web sites of over 100 automobile dealerships have been compromised in a supply-chain assault that tried to contaminate the PCs of web guests.
As researcher Randy McEoin explains in a weblog submit, cybercriminals contaminated the programs of LES Automotive, an organization which gives a video companies to assist automobile dealerships market autos on-line.
In consequence, webpages that have been alleged to show a video of an attractive automobile may as an alternative redirect dealerships’ on-line guests to a third-party webpage which – in a method referred to as a “ClickFix” assault – offered a CAPTCHA asking if they might show that they have been “not a robotic.”
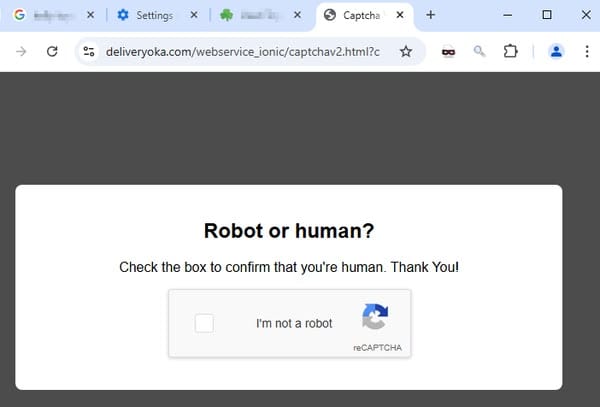
In itself, a CAPTCHA is just not an uncommon sight on the web. However all is just not because it appears, as a result of the consumer is then offered with a really particular technique for proving that they’re human and never a bot.
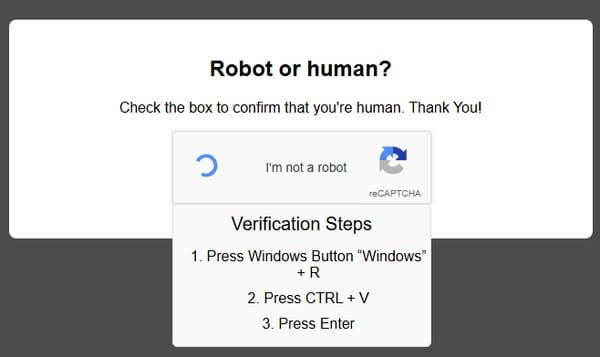
Verification Steps 1. Press Home windows Button “Home windows” + R 2. Press CTRL + V 3. Press Enter
That is very totally different from being requested to determine the visitors lights or a hearth hydrant in {a photograph}!
The directions by the bogus “verification” request provoke a Home windows Run command, pasting no matter malicious code the webpage has put into the pc’s clipboard.
And that is what’s considerably ingenious, as a result of the malicious hackers have cleverly waltzed across the safety of conventional safety instruments. It is you, the consumer, manually getting into a malicious command in your PC. It isn’t an exterior piece of harmful software program or script on an internet site that is doing it.
For some months it has grow to be more and more widespread for cybercriminals to make use of the disguise of a faux CAPTCHA verification to trick customers into unknowingly working PowerShell instructions that enable safety to be breached.
Within the specific case of the automobile dealerships, it seems that the purpose of the attackers is to socially-engineer harmless customers into an an infection by the malware referred to as SectopRAT.
If a PC is unlucky sufficient to grow to be contaminated by SectopRAT, malicious hackers can steal delicate information from the contaminated laptop comparable to their cryptocurrency pockets credentials.
In October final yr, the US Authorities suggested customers and organisations to be vigilant because it detailed the menace, and gave examples of internet sites that impersonated Google Chrome, Fb, reCAPTCHA, and others utilizing the ClickFix social engineering tactic.
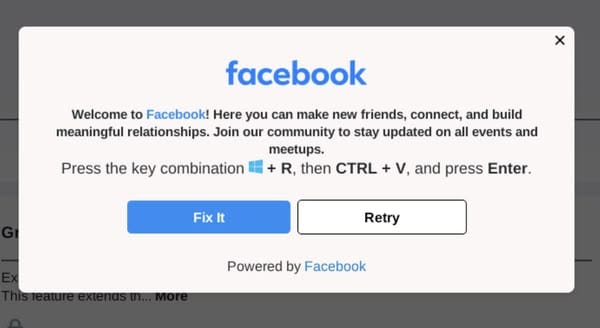
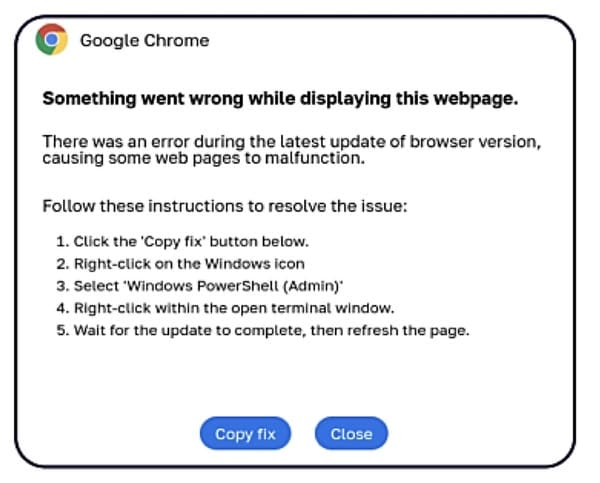
Day-after-day hundreds of persons are falling for ClickFix scams, and serving to their computer systems grow to be contaminated because of this. One sort of malware which has been distributed on this style is Lumma Stealer, a malicious program that targets net browsers, cryptocurrency wallets, two-factor authentication extensions and instantaneous messaging companies comparable to Telegram to extract worthwhile delicate information.
Do not make life straightforward for the hackers. Be extraordinarily cautious if a CAPTCHA asks you to carry out a peculiar motion – comparable to an odd key sequence – to show that you’re human. You would be unwittingly infecting your laptop with malware.

