Every year, a number of safety answer suppliers – together with Sophos – join MITRE’s ATT&CK Evaluations: Enterprise, a full-scale cyber assault emulation overlaying a number of eventualities primarily based on real-world risk actors and their ways, instruments, and procedures.
The analysis is designed to supply a sensible (and clear – the outcomes are publicly obtainable) appraisal of safety options’ performances, primarily based on end-to-end assault chains which embrace preliminary entry, persistence, lateral motion, and impression. Emulations sometimes embrace a multi-device ‘buyer’ setting, full with endpoints, servers, domain-joined units, and Lively Listing-managed customers.
2024 marked the fourth 12 months of Sophos taking part, and to have fun we needed to supply some perception into what this 12 months’s evaluation entailed, and to point out how true to life it truly is. Particularly, we’ll dive into the realism of the tooling, nuances within the testing methodology, and Sophos’ safety and detection capabilities. Whereas we are able to’t cowl the whole lot (every situation has 20-40 steps!), we’ll focus on a range, highlighting the depth and accuracy of the emulations.
For the 2024 analysis, MITRE chosen two risk classes, Ransomware and the Democratic Folks’s Republic of Korea (DPRK). The previous, as has been the case for a very long time, is among the largest cyber safety threats within the trade, and continues to evolve (for instance, the rise in distant encryption). The latter can be very related, given the proliferation of state-sponsored espionage assaults related to the area.
MITRE constructed three eventualities round these classes: an assault by a DPRK-affiliated risk actor targeted on MacOS (following risk actors focusing on MacOS in a number of campaigns, a development that seems set to proceed), and assaults by associates of two ransomware teams (Cl0p and LockBit).
DPRK
The DPRK situation was easy however lifelike, primarily based on the movement of the JumpCloud provide chain compromise: an attacker compromises a tool, establishes a persistent agent, and steals credentials. Risk actors affiliated with the DPRK are identified to interrupt their assaults into discrete levels and keep backdoors for launching future assaults.
Preliminary entry
Whereas the analysis presumes a provide chain assault, the situation itself concerned a person downloading and executing a malicious Ruby script (our evaluation confirmed a person execution path of Ruby). In a real-world provide chain assault, pre-installed software program would probably routinely execute the script. Nonetheless, that is nonetheless a believable and significant method – DPRK-affiliated attackers will use social engineering to persuade customers to run a script, as latest incidents present.
Simply as within the JumpCloud assault, MITRE’s Ruby script (referred to as begin.rb, thematically much like the identify of the true script: init.rb) downloads and executes a first-stage C2 agent (a Mach-O binary), masquerading as a docker-related element. It’s price noting that reverse-engineering real JumpCloud samples is just not attainable; to our data, the real-world samples will not be publicly obtainable. As with all MITRE ATT&CK Evaluations, the malware used was custom-built for the evaluation.
Persistence
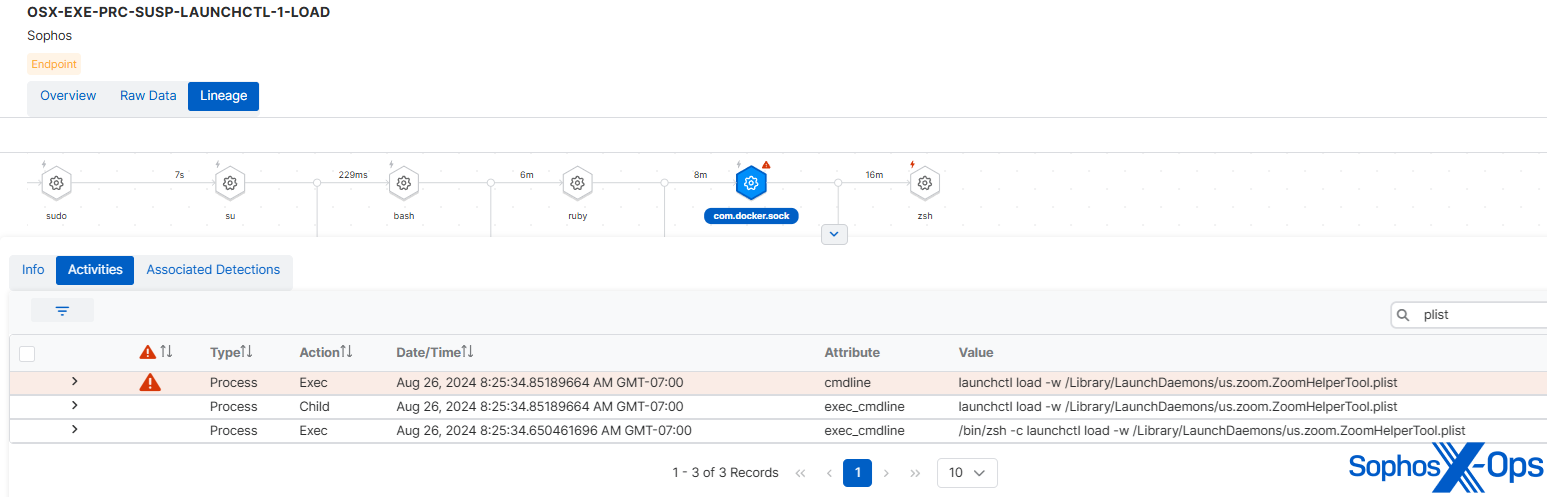
The primary-stage C2 agent then downloaded a second-stage backdoor (often called ‘STRATOFEAR’ within the real-world JumpCloud assault), which established persistence in a lot the identical approach as the real article, by way of LaunchDaemons (/Library/LaunchDaemons/us.zoom.ZoomHelperTool.plist).
Determine 1: Establishing persistence by way of ZoomHelperTool.plist
As with the Ruby script within the Preliminary Entry section, MITRE designed the backdoor to intently emulate the true factor. The backdoor was dropped in the identical location (/Library/Fonts), and had a really related identify (the true model was named ArialUnicode.ttf.md5, whereas the analysis model was pingfang.ttf.md5; each ‘Arial’ and ‘pingfang’ are names of real fonts).
As in the true JumpCloud assault, the ‘risk actor’ was stealthy and evasive, eradicating the first-stage implant information from the system in a short time. Within the emulation, they achieved this with an rm -f <FILE> command, as our execution path evaluation confirmed. We don’t know if this was the precise methodology utilized by the JumpCloud risk actor (it’s noisier than a direct API methodology, since a course of execution is extra prone to be logged), however, as famous beforehand, we are able to’t verify this for the reason that real-world samples will not be obtainable.
Like the real STRATOFEAR, the MITRE backdoor used encrypted configuration information, with a shell-out openssl enc -d command and a hardcoded password. Once more, utilizing a direct API-based methodology can be stealthier, however we don’t know if the JumpCloud risk actor took that method.
A fast observe on check security: For its C2 infrastructure, MITRE makes use of domains that work throughout the confines of the check setting, however will not be publicly resolvable by way of DNS. Nonetheless, they do resolve to public IP addresses. Because of this the community site visitors seems like real C2 exercise, however the domains will not be reachable outdoors the check setting.
Affect
As within the JumpCloud assault, the risk actor’s purpose is to gather information, together with system info, credentials, and delicate info held within the Keychain. MITRE’s STRATOFEAR backdoor was devoted to the unique, in that it downloaded and executed extra modules from the C2 server to hold out the theft. Just like the modules downloaded by the true STRATOFEAR, these have been written to a .tmp file within the /tmp listing, every named with a string of six random alphanumeric characters.
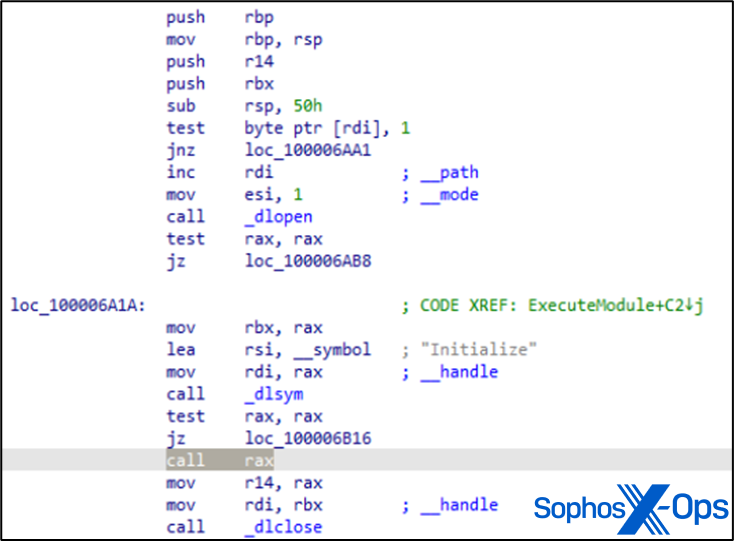
Within the analysis, MITRE’s STRATOFEAR downloaded /personal/tmp/rhkA2f.tmp, a module with the power to learn MacOS keychain information.
Determine 2: The ExecuteModule perform in MITRE’s STRATOFEAR pattern, utilizing dlopen/dlsym to name an ‘Initialize’ perform
This situation ended with the backdoor gathering the info; the analysis didn’t contain any precise exfiltration. Whereas some would possibly name this out as a difficulty with the methodology – credentials are sometimes solely helpful if exfiltrated – we’d argue that it’s a minor one. For those who, as an incident responder, can observe credential theft, you’ll pay attention to the potential impression and the related malicious exercise.
Cl0p
The second situation concerned an emulation of an assault by the Cl0p ransomware group (also referred to as TA505), a prolific risk actor. Right here, the movement of the assault intently mimicked – for essentially the most half – that of a 2019 incident, involving a downloader, a persistent RAT, subtle course of injection, and abuse of a trusted course of – finally resulting in a ransomware payload.
Preliminary entry
Whereas many of the situation was devoted to the 2019 real-world marketing campaign, the preliminary entry stage was barely completely different. As in 2019, the risk actor used a DLL to put in a persistent RAT. However whereas the real-world assault concerned malicious Workplace paperwork containing an embedded DLL, which was loaded dynamically into the Workplace course of, the MITRE situation concerned a person interactively operating cmd.exe and executing the DLL by way of rundll32.exe.
This DLL was already current on the host, having been downloaded by way of a curl command from a separate interactive cmd.exe (this step was not included within the situation) following preliminary entry over RDP. It’s price noting that this methodology of preliminary entry is quite common amongst ransomware teams and different threats actors, significantly when buying stolen credentials/entry by way of preliminary entry brokers (IABs). In a single very outstanding case, nevertheless, Cl0p additionally abused a zero-day vulnerability within the MOVEit file switch software (CVE-2023-34362).
Whereas it’s very believable that an attacker would acquire direct distant entry to the compromised host, the situation might maybe have included the ingress of the DLL tooling for a extra full emulation.
Persistence
As within the 2019 marketing campaign, the MITRE ‘risk actor’ loaded the persistent RAT SDBbot by compromising the trusted winlogon.exe course of, utilizing Picture File Execution Choices (IFEO) injection with a ‘VerifierDLL’ key.
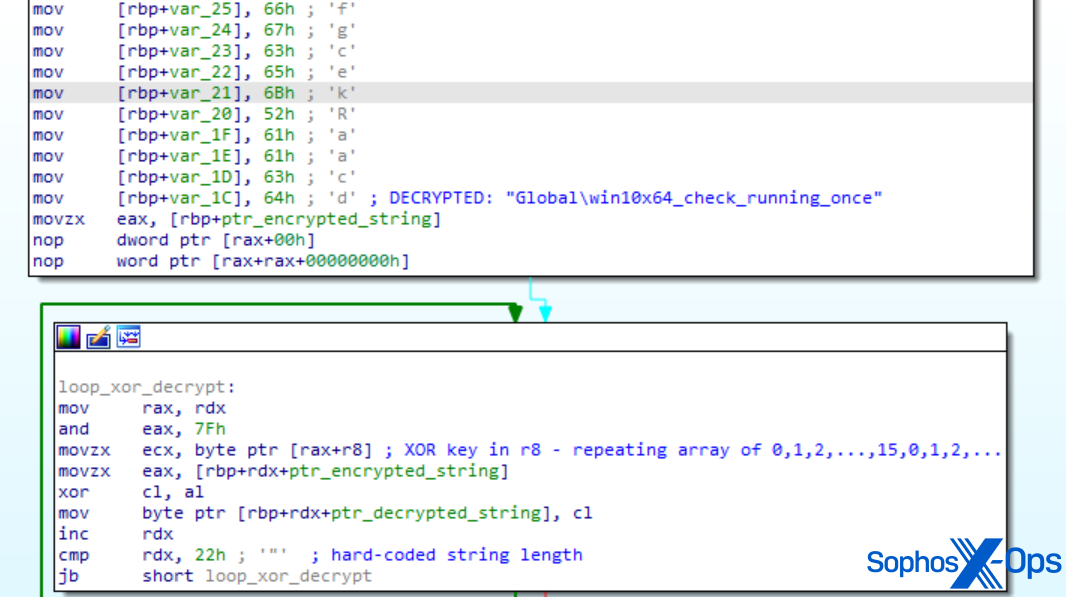
SDBbot makes use of encrypted strings and a mutex to protect its start-up. As with the DPRK situation, the MITRE pattern used a similar-but-different identify for the mutex (‘windows_7_windows_10_check_running_once_mutex’ within the real-world assault, ‘win10x64_check_running_once’ for the analysis).
Determine 3: Disassembly of MITRE’s SDBbot pattern. Notice the mutex identify and the decryption perform
In MITRE’s implementation of SDBbot, the important thing materials is a repeat of the identical 16 incrementing bytes from 0 to fifteen. This isn’t as safe as a genuinely random 128-byte string – however it’s enough to obfuscate the strings used to reference API names and information fields past trivial static evaluation strategies. MITRE used this methodology of string obfuscation all through the Cl0p situation, in addition to within the LockBit situation mentioned under.
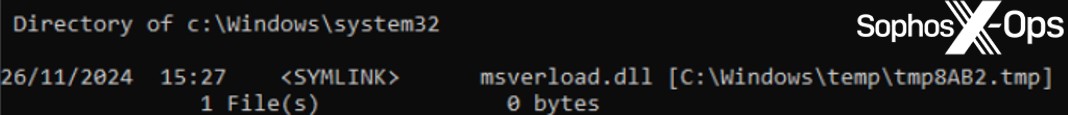
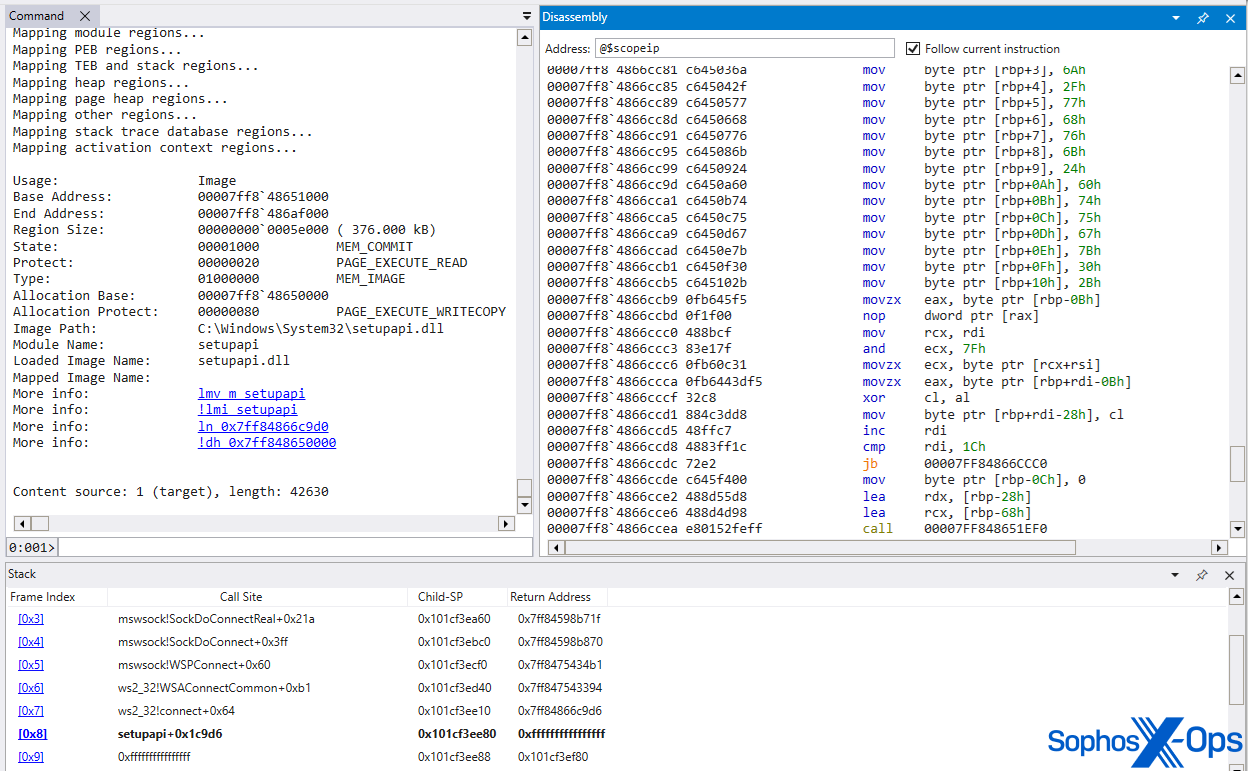
MITRE’s pattern was loaded by way of a reflective loader, overwriting picture reminiscence in setupapi.dll. For the reason that RAT exists in commonplace ‘picture’ reminiscence, it’s more durable to detect than if it have been in dynamically-allocated heap reminiscence. This can be a subtle injection methodology, designed to evade fashionable defenses. MITRE’s method introduced one other problem when it got here to detecting the exercise of the installer (the rundll32 course of) dropping the SDBbot loader element. The installer dropped the loader to a %TEMP% location, however created a symbolic hyperlink to that path within the SYSTEM folder, and the IFEO registry key was set as much as level to the SYSTEM folder path – thereby creating an extra layer of abstraction between the dropper and the persistent RAT.
Determine 4: The symbolic hyperlink for the msverload.dll loader
Using the ‘VerifierDLLs’ methodology added additional complexity to the execution movement, because the loader (msverload.dll) was loaded into the winlogon.exe course of house previous to the method’s entry level. It then used VirtualAlloc to inject and execute embedded shellcode, and VirtualProtect to make the in any other case RX picture reminiscence of setupapi.dll writeable, earlier than overwriting its contents with the SDBbot RAT. The reminiscence permissions have been later reset to RX, with the intention to make the code appear to be ‘common’ picture reminiscence – as a DLL would seem when loaded immediately from disk.
Determine X: MITRE’s SDBbot is loaded, and overwrites the module of the in any other case professional setupapi.dll IMAGE reminiscence, with reminiscence protections reset to PAGE_EXECUTE_READ
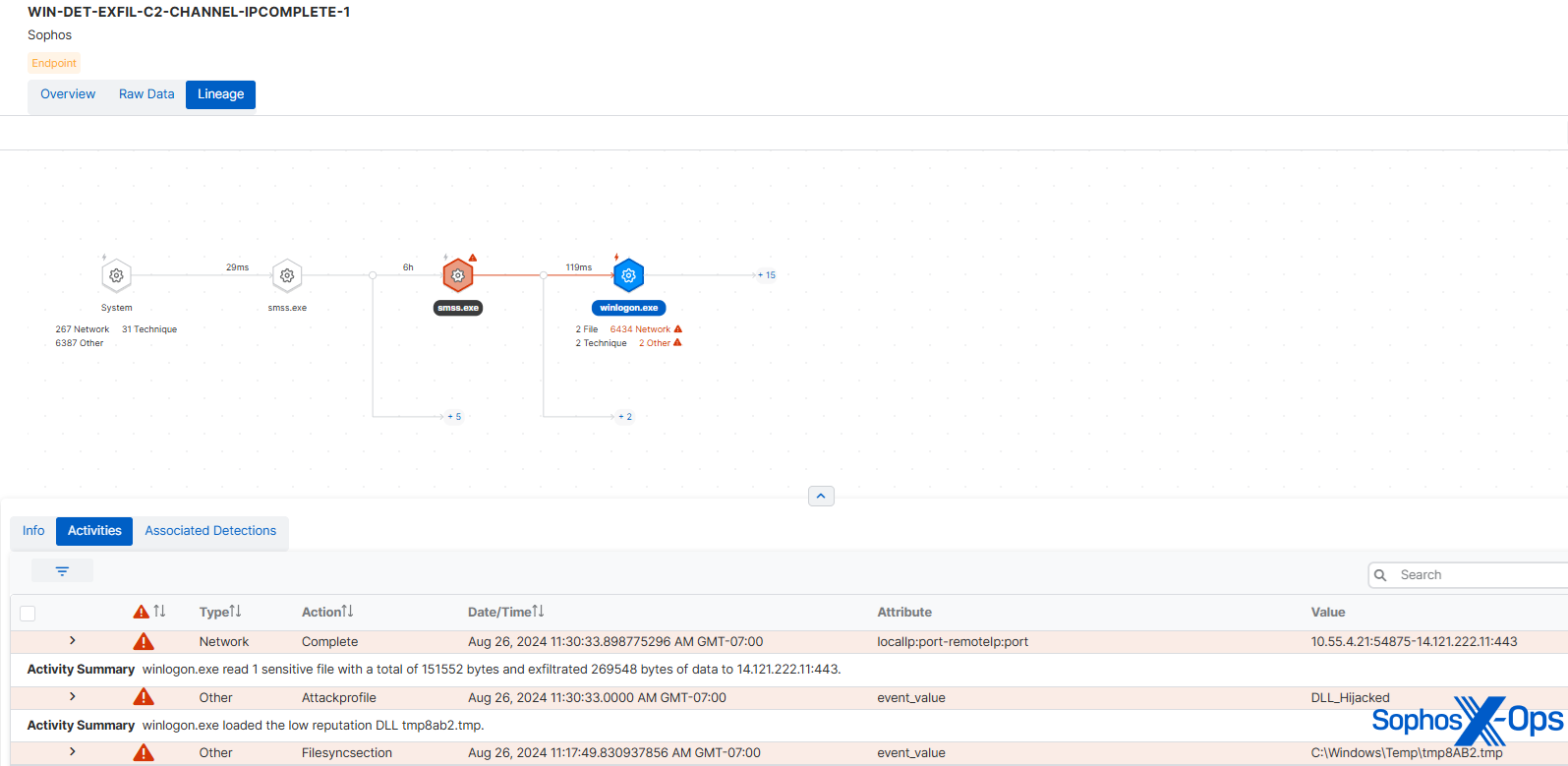
Our detection technique right here concerned a number of facets: it’s suspicious to have C2 exercise originating from a winlogon course of, and C2 exercise in itself is a standard reminiscence scan set off (as we mentioned in a weblog on this subject in 2023). Reminiscence scans additionally detected a shellcode sample. The suspicious C2 occasion enabled Sophos Detection to seize the info exfiltration conduct, and we famous that the exfiltration methodology – utilizing SDBbot and sending information over the C2 channel – was adopted by Cl0p in 2020.
Determine 6: Detecting exfiltration in the course of the Cl0p situation
Affect
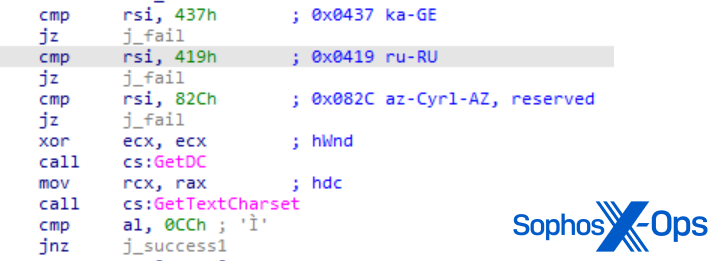
MITRE’s implementation of the Cl0p ransomware pattern (sysmonitor.exe, downloaded by way of SBDbot) was modelled very intently on a real-world pattern from 2019. Identical to the true factor, MITRE’s pattern used GetKeyboardLayout to examine for layouts utilized in Russia, Georgia, and Azerbaijan (to keep away from focusing on any methods utilizing them). It additionally employed an similar comparability for the GetDC/GetTextCharset APIs, used to attain the identical goal.
Determine 7: MITRE’s Cl0p pattern calling GetDC and GetTextCharset to examine for contaminated hosts in Russia, Georgia, or Azerbaijan
We additionally famous different near-exact matches in conduct and methodology, significantly when it got here to how the ransomware handled shadow volumes and trying to kill varied providers on compromised hosts.
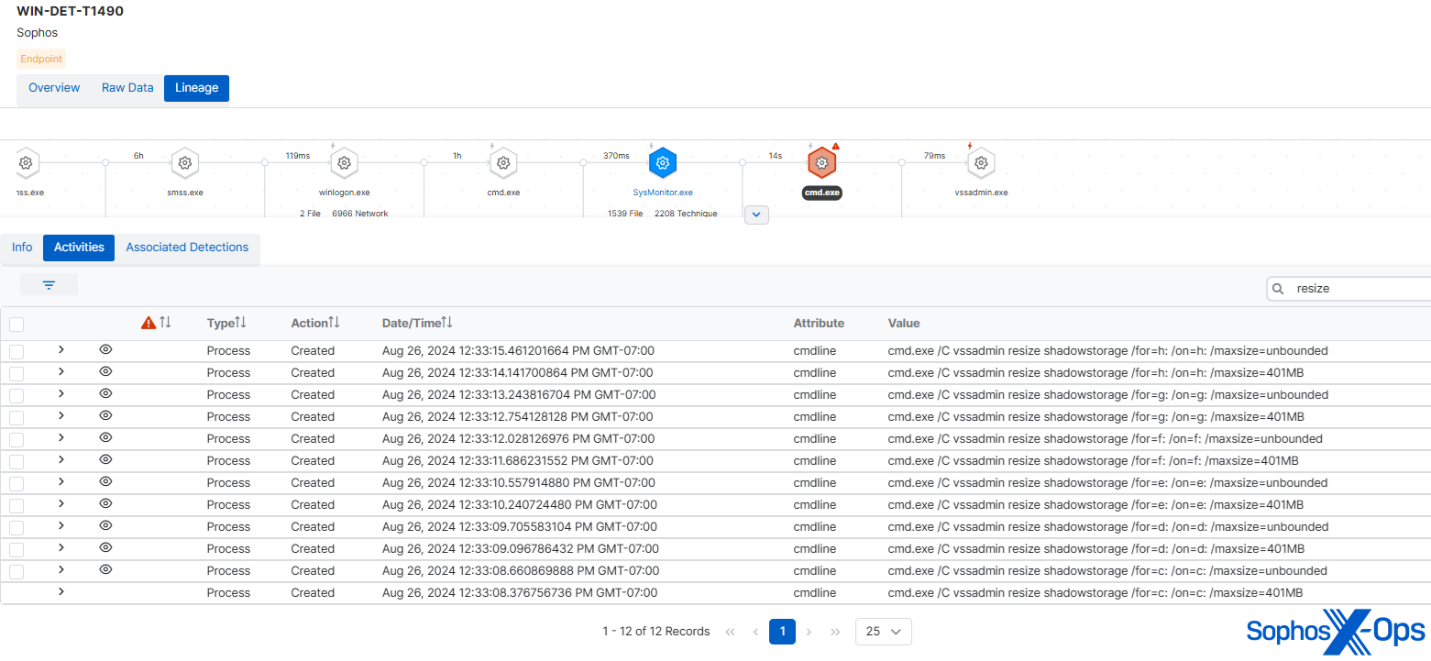
Many ransomware households will try to delete shadow volumes, to stop their targets from restoring information, after which resize the shadow storage, in order that no additional shadow volumes could be created. Nonetheless, the 2019 Cl0p ransomware carried out the latter step in a selected approach, biking by means of a hardcoded checklist of drives (from C to H). MITRE’s pattern emulated this conduct precisely.
Determine 8: MITRE’s implementation of Cl0p biking by means of varied drives to resize the shadow storage
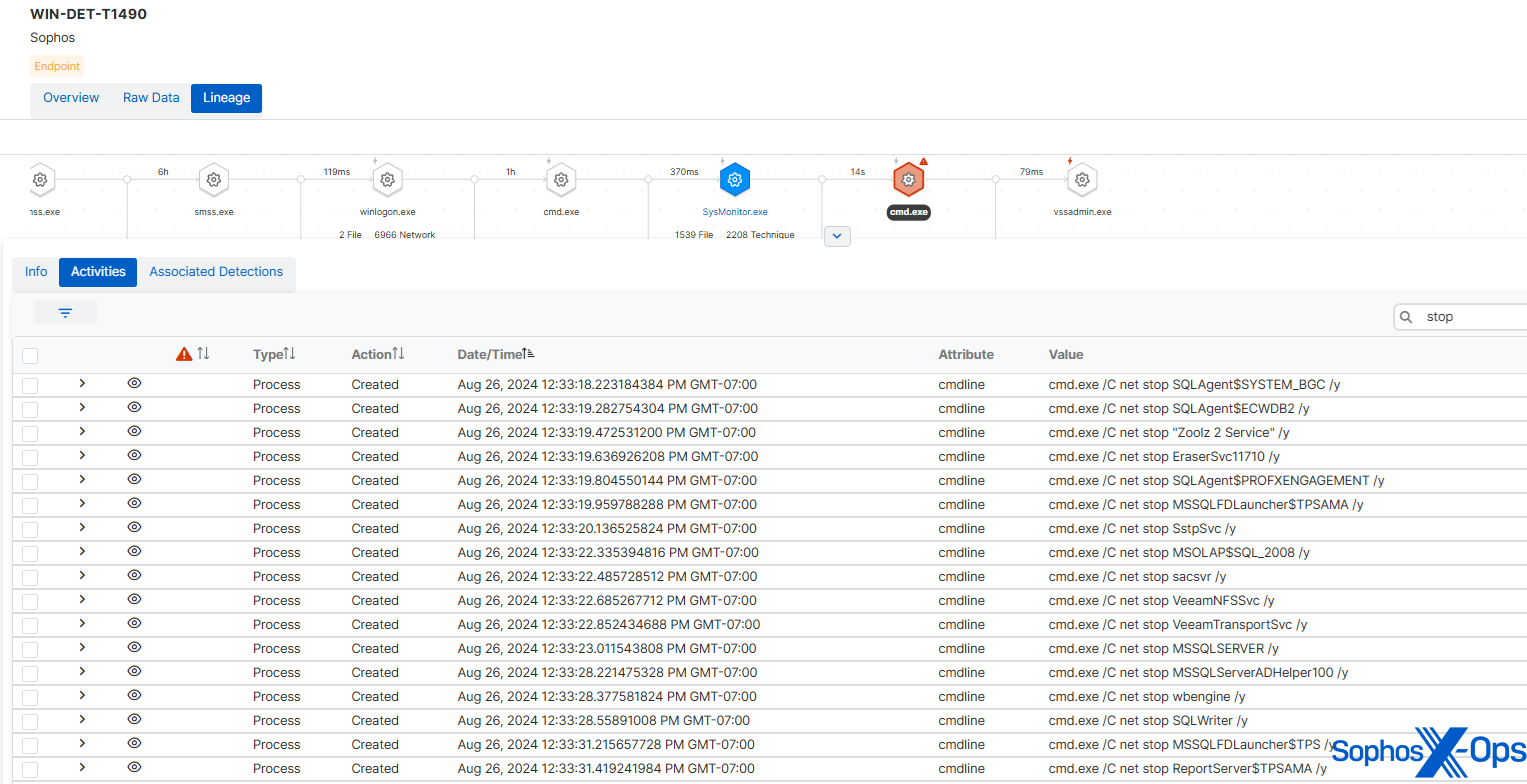
Furthermore, like many ransomware variants, Cl0p ransomware iterates by means of a listing of assorted providers – together with safety providers and providers that will include key information to be encrypted – and makes an attempt to terminate them by way of internet cease.
MITRE’s pattern employed the identical checklist utilized by the real Cl0p ransomware, in the identical order – albeit it excluded safety providers, presumably to stop any disruption to the check.
Determine 9: Sophos detection, displaying the internet cease instructions utilized in MITRE’s Cl0p pattern
For its file encryption, the MITRE malware used AES, appending a particular marker (“Cl1pCl0p!?”) to the info throughout the encrypted information. This was an analogous method to the true malware, which used a marker of “Clop^ ”. Nonetheless, whereas the 2019 samples used the advapi32.dll CryptAcquireContextW API for cryptographic algorithm help, the MITRE model employed the open-source CryptoPP library – a extra fashionable method utilized by many ransomware households right this moment.
LockBit
LockBit, like Cl0p, is a prolific ransomware group, albeit one considerably disrupted by legislation enforcement companies in February 2024. Nonetheless, as a result of a LockBit builder leaked in 2022, risk actors proceed to deploy its ransomware. MITRE’s LockBit situation included TTPs identified to be utilized by some LockBit associates (as with the Cl0p situation, it’s price noting that whereas the conduct of ransomware binaries will typically be constant throughout assaults, since these are developed and distributed centrally, associates might have extra flexibility of their approaches, and so their playbooks – and subsequent TTPs and IOCs – might differ). These TTPS included the preliminary entry methodology, using ThunderShell and PsExec, and varied evasion methods.
Preliminary entry
The MITRE ‘risk actor’ started their assault by authenticating over an externally-facing TightVNC service (a professional distant administration software), utilizing credentials that had beforehand been compromised. Ransomware-as-a-Service (RaaS) associates generally get hold of preliminary entry on this approach, utilizing previously-compromised providers and credentials which might be bought on cybercrime boards by IABS, as famous earlier with the Cl0p situation.
As soon as the attacker gained entry, they executed varied discovery instructions, which aligned with instructions that we regularly observe early on in a RaaS assault, together with:
nltest /dclist:<area>
cmdkey /checklist
internet group “Area Admins” /area
internet group “Enterprise Admins” /area
internet localgroup Directors /area
powershell /c "get-wmiobject Win32_Service |where-object { $_.PathName -notmatch "C:Home windows" -and $_.State -eq "Operating"} | select-object identify, displayname, state, pathname
These instructions are virtually similar to these noticed throughout a 2022 LockBit assault.
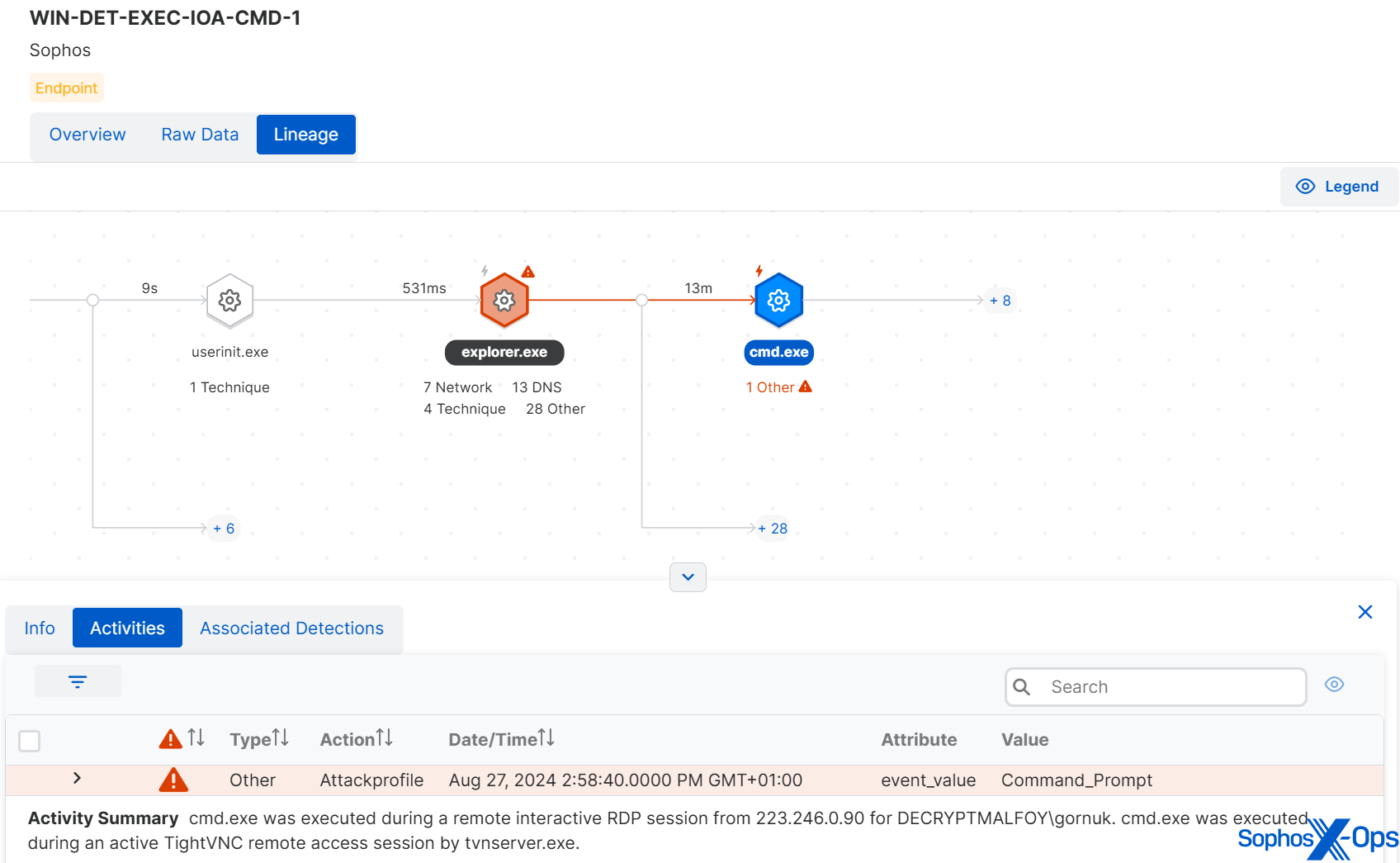
The execution of cmd.exe throughout a distant interactive session was a key indicator of assault right here, as was a TightVNC connection and distant interactive logon from a suspicious IP handle.
Determine 10: Investigating suspicious exercise in the course of the preliminary entry stage
Persistence
To take care of a foothold within the setting, the risk actor then deployed a PowerShell distant entry shell often called ThunderShell. As CISA notes, this can be a software identified for use by LockBit associates, enabling them to take care of persistence if the preliminary entry methodology is misplaced. Right here, we have been in a position to monitor recurring community connections to establish ‘beaconing’ conduct, and flag processes and connections deemed suspicious.
The MITRE ‘attacker’ established additional persistence by means of the winlogon computerized logon registry key. This motion did deviate barely from what we’d anticipate in a real-world situation; in our expertise, risk actors sometimes enumerate these keys to probably establish plaintext credentials.
Affect
MITRE opted to emulate the bespoke LockBit exfiltration software StealBit, which RaaS associates use to carry out double extortion (a way utilized by many different ransomware teams) – permitting them to exfiltrate delicate information to a distant server earlier than it’s encrypted.
MITRE’s model of StealBit (named connhost.exe), similar to the true factor, used a PEB “BeingDebugged” flag to examine for hooked up debuggers, and in addition carried out dynamic API decision utilizing LoadLibraryExA and GetProcAddress – with resolved DLLs saved as XOR-obfuscated filenames. This can be a very related method to the true StealBit malware.
After exfiltration, the MITRE ‘risk actor’ deployed an emulated model of the principle LockBit executable to encrypt information and self-replicate throughout the setting.
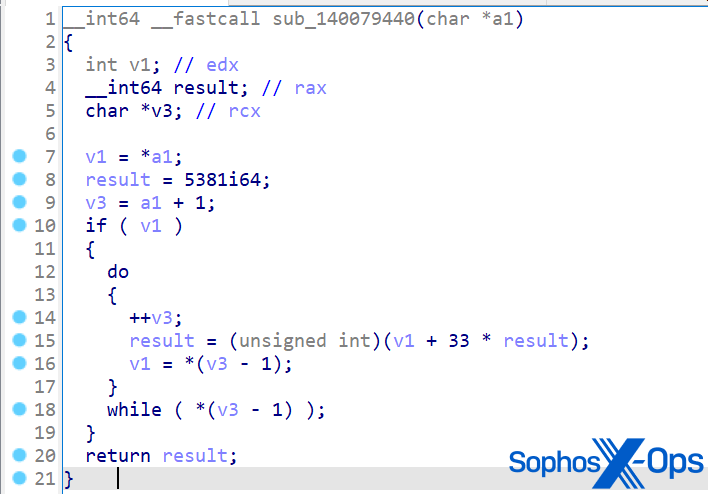
As with the real-world model, MITRE’s LockBit pattern used a number of evasive methods, together with dynamic API decision utilizing an in-memory API hashing algorithm (to maintain API names hidden from static evaluation), and anti-debugging by way of NtSetInformationThread. We documented each of those strategies in our evaluation of LockBit 3.0 in 2022, though it’s price noting that MITRE’s implementation used DJB2 hashing. This differs from the unique LockBit method (a {custom} implementation utilizing a ROR-based hashing methodology with a seed key), however the finish outcome is identical, whereas additionally stopping the introduction of a identified IOC which we and different distributors might have beforehand detected.
Determine 11: MITRE’s model of LockBit used an implementation of the DJB2 hashing algorithm. This was a posh implementation, and we famous that MITRE appeared to have gone to nice lengths to copy the performance of the real LockBit binary
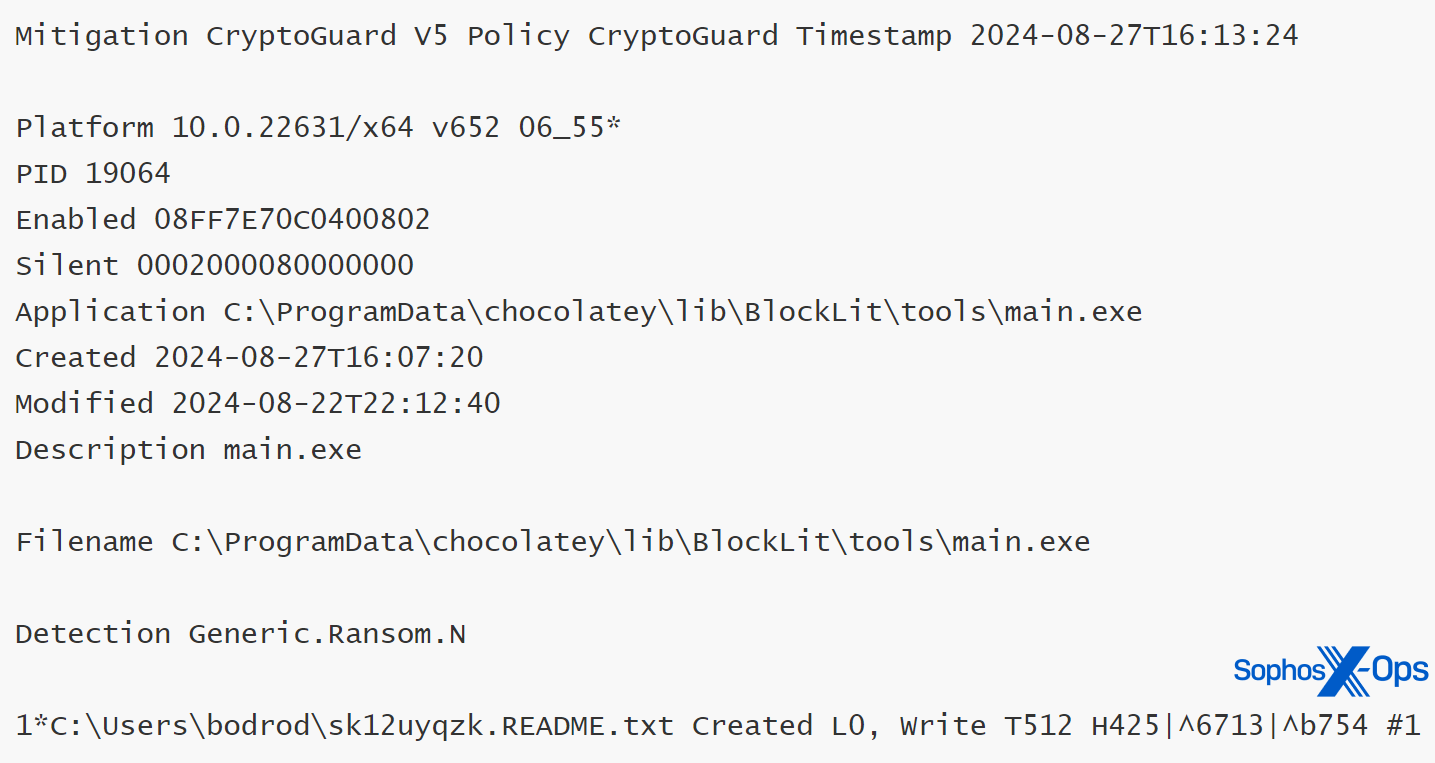
Sophos detected this exercise utilizing CryptoGuard, though we should always observe that as this specific check was operating in monitor-only mode, CryptoGuard didn’t roll again the encryption. In one other, separate check, targeted on protections, encryption exercise resulted within the encrypted information being rolled again to their unique state, even throughout distant encryption emulations.
Determine 12: CryptoGuard thumbprint info displaying the detection of ransomware exercise and the creation of a ransom observe
2024 marked the fourth 12 months that Sophos has participated in MITRE’s ATT&CK Evaluations: Enterprise. As in earlier years, the concentrate on end-to-end assault chains and realism has made the analysis a particularly worthwhile train in assessing our capabilities and people of different distributors. We additionally welcome MITRE’s emphasis on transparency.
Like all form of emulation, a lot of the worth of those evaluations comes from how correct and lifelike their eventualities are. Whereas we did observe that MITRE’s exams deviated from real-world assaults in a couple of, minor situations – typically as a result of unavoidable constraints – the general resemblance to identified campaigns and risk actors was very robust.
Clear, lifelike evaluations, wherein a number of distributors take part, profit not solely distributors themselves, but additionally prospects, and, because of this, wider society. We sit up for persevering with to take part in these evaluations sooner or later, and to reporting our ideas and findings wherever attainable.