An information-focused method to tackling phishing and enterprise fraud guarantees important reductions within the quantity of phishing and phone-based fraud that firms — and their clients — face, however worries stay over whether or not fraudsters will adapt.
The Monetary Companies Data Sharing and Evaluation Heart (FS-ISAC) unveiled its Phishing Prevention Framework on Nov. 19, a program consisting of greatest practices in knowledge assortment, protection, and buyer communications that has already decreased the quantity of phishing incidents — as measured by abuse complaints — in a pilot program with three banks. The framework reduce the incidence of abuse complaints for these monetary providers companies in half and guarantees important advantages for any enterprise focused by cybercriminals, in the event that they implement sure greatest practices — similar to safety training and intelligence assortment — included within the framework.
Whereas FS-ISAC has launched the framework for the monetary providers sector — the place phishing is a pernicious drawback — the strategies are broadly relevant, says Linda Betz, govt vice chairman of worldwide group engagement on the group.
“Whereas the framework is tailor-made for monetary establishments because of the delicate nature of their operations, the methods can profit companies throughout industries,” she says. “As an example, cataloging communication channels and deploying anti-phishing applied sciences are broadly relevant and scalable options for any group coping with delicate buyer interactions or excessive volumes of transactional knowledge.”
The monetary providers sector shouldn’t be the one business suffering from phishing. In 2023, US customers and companies reported almost 300,000 phishing-related crimes to the FBI, based on its annual Web Crime Report. Phishing and pretexting — which differ in that the attacker surreptitiously joins an e mail thread — account for 31% and 40%, respectively, of all social engineering assaults, based on Verizon’s “2024 Knowledge Breach Investigations Report” (DBIR). Safety consciousness workouts have discovered that it takes lower than 60 seconds for the primary victims of a phishing marketing campaign to click on a hyperlink and enter their data.
Deal with Sources, Not Transactions
As a part of its Phishing Prevention Framework, the FS-ISAC recommends that organizations create a data-focused course of for dealing with abuse complaints and deal with maximizing the insights that may be realized from phishing campaigns. Firms ought to create a fraud and phishing consumption pipeline that data crucial data and an abuse field infrastructure that enables safety and fraud groups to disseminate intelligence to different enterprise teams, the report states.
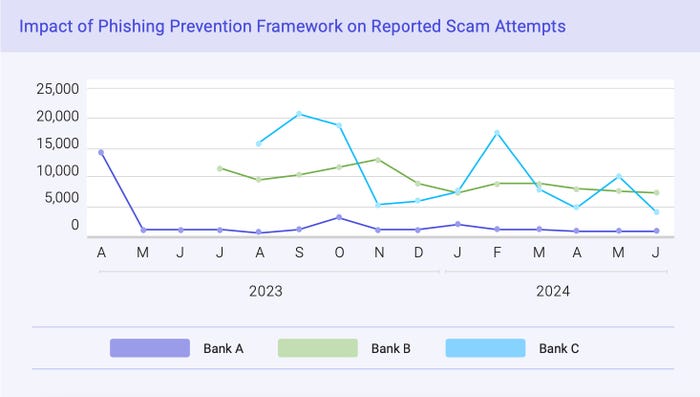
Three banks that piloted the Phishing Prevention Framework all noticed decreases in phishing abuse, however Financial institution A noticed essentially the most dramatic adjustments. Supply: FS-ISAC’s “Cease the Scams: A Phishing Prevention Framework for Monetary Companies” report
The important thing subject is that fraud reporting typically focuses on stopping the unhealthy transaction and spends little time on understanding how the exercise originated, FS-ISAC’s Betz says.
“Structuring the abuse field to glean that data from the shopper helps the monetary establishment know the place to focus to handle the basis trigger and take actions to scale back the danger and stop future makes an attempt, then share the actionable intelligence throughout the group and the sector,” she says. “[Companies] ought to implement structured fraud reporting methods to seize actionable knowledge, coordinate throughout related departments, and take part in industrywide risk intelligence platforms to assist your entire sector perceive the present techniques being utilized by fraudsters.”
The framework additionally requires cataloging all the methods a enterprise communicates with clients and companions, a doubtlessly time-consuming course of. Whereas automation may help, collaborating internally throughout teams and with third events is essential, says Betz.
“Leveraging a succinct knowledge assortment survey together with the kind, origin, and outcomes of the fraudulent exercise may help set up any developments within the phishing makes an attempt and higher determine any weak areas inside networks,” she says.
Protecting Up With Attackers
Whereas all of the steps included within the framework are frequent sense approaches to anti-phishing, implementing all of them will take time, says Betz. For that motive, the FS-ISAC has listed the actions together with a step quantity to prioritize defensive efforts.
Whether or not establishing the processes and applied sciences known as for by the Phishing Prevention Framework will result in fewer profitable phishing campaigns or simply power attackers to evolve stays to be seen, says Matthew Harris, senior product supervisor for fraud at OpSec Safety, a model safety and anti-fraud agency.
“One factor I’ve realized about coping with fraudsters is that they will pivot immediately, and the issue is that they will pivot far quicker than some other firm can pivot,” he says. “In the event that they understand that there is a means that they will get higher ROI, they will do it.”
Scammers are already shifting towards phishing assaults that more and more use voice calls. Telephone-based phishing began as a minor subject in 2021 and now accounts for almost 1 / 4 (23%) of all phishing assaults, based on knowledge collected by OpSec Safety. Telephone-based phishing consists of SMS phishing — “smishing” — and phishing emails that embrace a fraudulent telephone quantity.
As a result of there are fewer integrity checks on telephone calls, cyberattackers will possible more and more use the telecommunications channel of their scams, says OpSec’s Harris.
“As e mail safety … has gotten increasingly more superior, it turns into increasingly more tough [for a scammer] to speak a conventional e mail to an individual,” he says. “By pivoting away from e mail and towards a telephone quantity, … there is a good probability an individual goes to select up that telephone [giving them] entry to the sufferer straight.”
For that motive, the ultimate step of the FS-ISAC’s framework consists of collaborating with telecommunications companies to scale back the assault floor space by way of telephone methods. Many suppliers have applied sciences or providers, similar to “Do Not Originate,” on numbers which might be inbound solely, giving enterprise clients extra controls, says FS-ISAC’s Betz.
“Partnerships with telecommunications suppliers are more and more collaborative, as these firms acknowledge the mutual advantages of decreasing spam and phishing assaults,” she says.

