ESET Analysis
ESET researchers detected a number of, widespread phishing campaigns focusing on SMBs in Poland throughout Could 2024, distributing numerous malware households
30 Jul 2024
•
,
8 min. learn

Just some months again, ESET Analysis revealed a blogpost about huge phishing campaigns throughout Central and Jap Europe carried out through the second half of 2023. In these campaigns Rescoms malware (also called Remcos), protected by AceCryptor, was delivered to potential victims with the objectives of credential theft and potential acquire of preliminary entry to firm networks.
Phishing campaigns focusing on the area didn’t cease in 2024. On this blogpost we current what current phishing campaigns appeared like and the way the selection of supply mechanism shifted away from AceCryptor to ModiLoader.
Key factors of this blogpost:
- ESET detected 9 notable ModiLoader phishing campaigns throughout Could 2024 in Poland, Romania, and Italy.
- These campaigns focused small and medium-sized companies.
- Seven of the campaigns focused Poland, the place ESET merchandise protected over 21,000 customers.
- Attackers deployed three malware households through ModiLoader: Rescoms, Agent Tesla, and Formbook.
- Attackers used beforehand compromised e-mail accounts and firm servers, not solely to unfold malicious emails but additionally to host malware and accumulate stolen knowledge.
Overview
Despite the fact that the phishing campaigns have been ongoing all through the primary half of 2024, this blogpost focuses simply on Could 2024, as this was an eventful month. Throughout this era, ESET merchandise protected over 26,000 customers, over 21,000 (80%) of whom have been in Poland. Along with Poland, the place over 80% of potential victims have been positioned, Italy and Romania have been additionally focused by the phishing campaigns. In whole we registered 9 phishing campaigns, seven of which focused Poland all through Could, as will be seen in Determine 1.
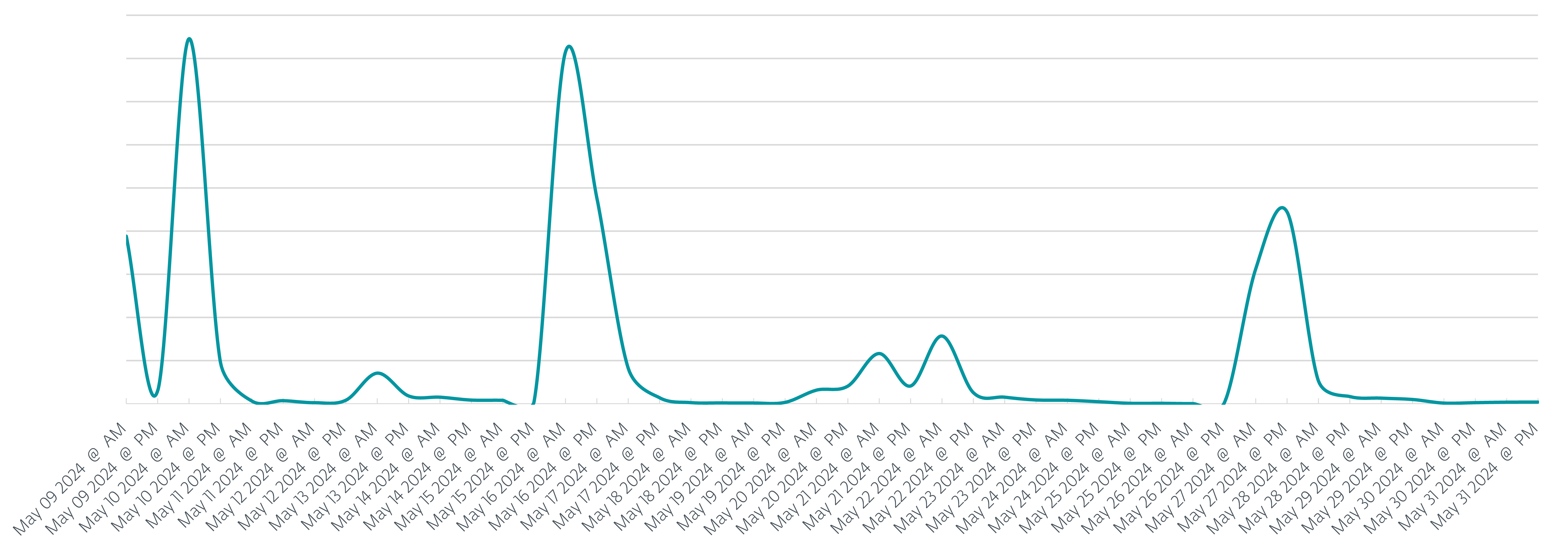
As compared with the campaigns that occurred through the finish of 2023, we see a shift away from utilizing AceCryptor as a software of alternative to guard and efficiently ship the malware. As a substitute, in all 9 campaigns, attackers used ModiLoader (aka DBatLoader) as the popular supply software of alternative. The ultimate payload to be delivered and launched on the compromised machines various; we’ve detected campaigns delivering:
- Formbook – info stealing malware found in 2016,
- Agent Tesla – a distant entry trojan and knowledge stealer, and
- Rescoms RAT – distant management and surveillance software program, capable of steal delicate info.
Campaigns
Typically, all campaigns adopted an analogous state of affairs. The focused firm obtained an e-mail message with a enterprise supply that may very well be so simple as “Please present your finest value supply for the connected order no. 2405073”, as will be seen in Determine 2.

In different campaigns, e-mail messages have been extra verbose, such because the phishing e-mail in Determine 3, which will be translated as follows:
Hello,
We want to buy your product for our consumer.
Please discover the connected inquiry for step one of this buy.
The connected sheet comprises goal costs for many merchandise. I highlighted 10 parts to concentrate on pricing – the remainder of the gadgets are optionally available to cost (we are going to apply comparable value stage based mostly on different costs).
Please get again to me earlier than 28/05/2024
Should you want extra time, please let me understand how a lot you’ll need.
When you’ve got any questions, please additionally let me know.

As within the phishing campaigns of H2 2023, attackers impersonated current firms and their staff because the strategy of alternative to extend marketing campaign success price. On this manner, even when the potential sufferer appeared for the standard crimson flags (other than potential translation errors), they have been simply not there, and the e-mail appeared as authentic because it may have.
Contained in the attachments
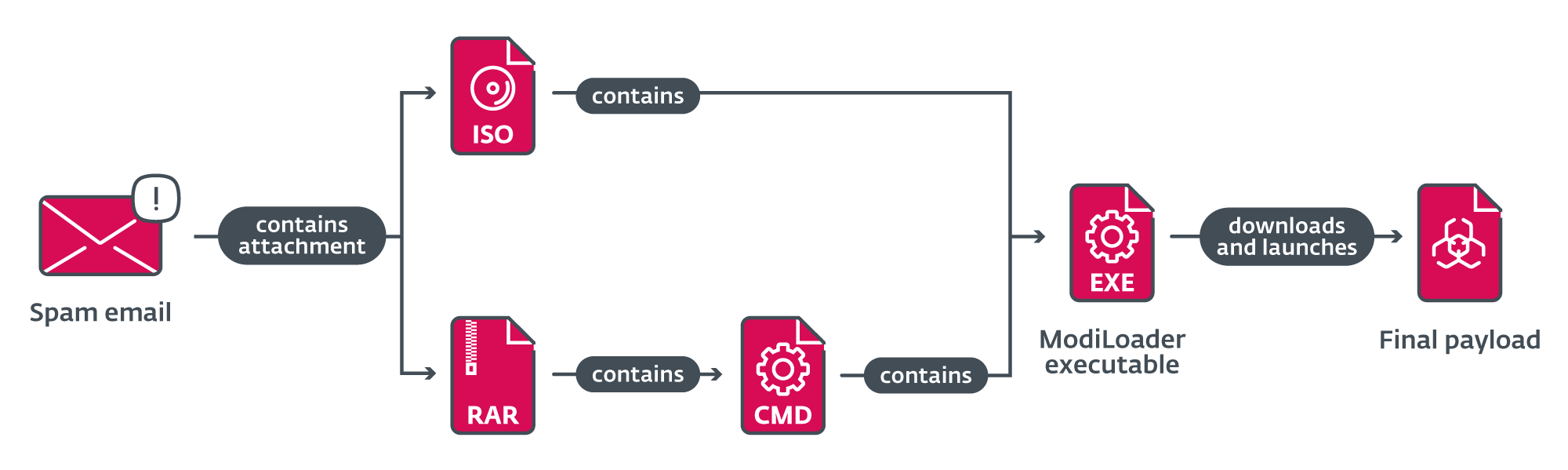
Emails from all campaigns contained a malicious attachment that the potential sufferer was incentivized to open, based mostly on the textual content of the e-mail. These attachments had names like RFQ8219000045320004.tar (as in Request for Citation) or ZAMÓWIENIE_NR.2405073.IMG (translation: ORDER_NO) and the file itself was both an ISO file or archive.
In campaigns the place an ISO file was despatched as an attachment, the content material was the ModiLoader executable (named equally or the identical because the ISO file itself) that will be launched if a sufferer tried to open the executable.
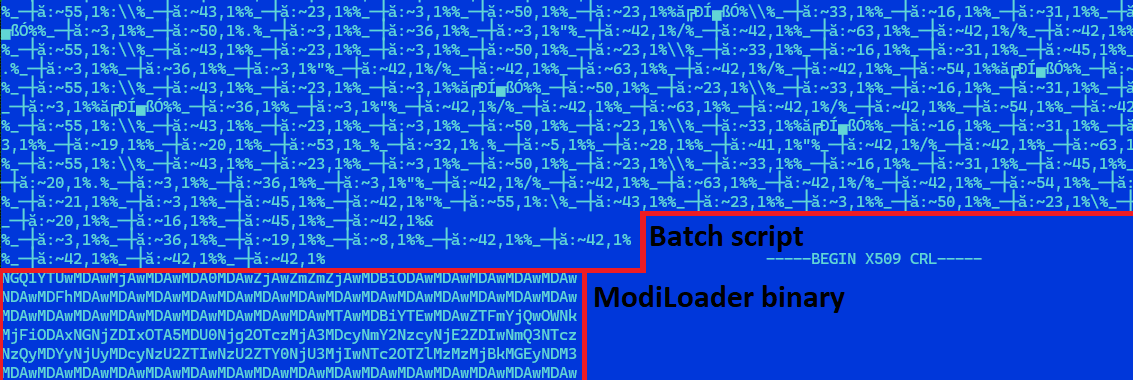
Within the different case, when a RAR archive was despatched as an attachment, the content material was a closely obfuscated batch script, with the identical identify because the archive and with the .cmd file extension. This file additionally contained a base64-encoded ModiLoader executable, disguised as a PEM-encoded certificates revocation listing. The script is chargeable for decoding and launching the embedded ModiLoader (Determine 4).
When ModiLoader is launched
ModiLoader is a Delphi downloader with a easy process – to obtain and launch malware. In two of the campaigns, ModiLoader samples have been configured to obtain the next-stage malware from a compromised server belonging to a Hungarian firm. In the remainder of the campaigns ModiLoader downloaded the following stage from Microsoft’s OneDrive cloud storage. We noticed 4 accounts the place second-stage malware was hosted. The entire chain of compromise from receiving the malicious e-mail till launching the ultimate payload is summarized in Determine 5.
Knowledge exfiltration
Three totally different malware households have been used as a remaining payload: Agent Tesla, Rescoms, and Formbook. All these households are able to info stealing and thus permit attackers not solely to increase their datasets of stolen info, but additionally to arrange the bottom for his or her subsequent campaigns. Despite the fact that the exfiltration mechanisms differ between malware households and campaigns, it’s value mentioning two examples of those mechanisms.
In a single marketing campaign, info was exfiltrated through SMTP to an handle utilizing a site much like that of a German firm. Notice that typosquatting was a preferred method used within the Rescoms campaigns from the tip of final 12 months. These older campaigns used typosquatted domains for sending phishing emails. One of many new campaigns used a typosquatted area for exfiltrating knowledge. When somebody tried to go to net pages of this typosquatted area, they’d be instantly redirected to the net web page of the authentic (impersonated) firm.
In one other marketing campaign, we noticed knowledge being exfiltrated to an internet server of a visitor home positioned in Romania (a rustic focused now and previously by such campaigns). On this case, the net server appears authentic (so no typosquatting) and we consider that the lodging’s server had been compromised throughout earlier campaigns and abused for malicious actions.
Conclusion
Phishing campaigns focusing on small and medium-sized companies in Central and Jap Europe are nonetheless going sturdy within the first half of 2024. Moreover, attackers reap the benefits of beforehand profitable assaults and actively use compromised accounts or machines to additional unfold malware or accumulate stolen info. In Could alone, ESET detected 9 ModiLoader phishing campaigns, and much more exterior this time-frame. Not like the second half of 2023, when Rescoms packed by AceCryptor was the popular malware of alternative of the attackers, they didn’t hesitate to alter the malware they use to be extra profitable. As we offered, there are a number of different malware households like ModiLoader or Agent Tesla within the arsenal of those attackers, prepared for use.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis presents personal APT intelligence stories and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
A complete listing of indicators of compromise (IoCs) will be present in our GitHub repository.
Recordsdata
|
SHA-1 |
Filename |
Detection |
Description |
|
E7065EF6D0CF45443DEF |
doc023561361500.img |
Win32/TrojanDownloader. |
Malicious attachment from phishing marketing campaign carried out in Poland throughout Could 2024. |
|
31672B52259B4D514E68 |
doc023561361500__ |
Win32/TrojanDownloader. |
ModiLoader executable from phishing marketing campaign carried out in Poland throughout Could 2024. |
|
B71070F9ADB17C942CB6 |
N/A |
MSIL/Spy.Agent.CVT |
Agent Tesla executable from phishing marketing campaign carried out in Poland throughout Could 2024. |
|
D7561594C7478C4FE37C |
ZAMÓWIENIE_NR.2405073. |
Win32/TrojanDownloader. |
Malicious attachment from phishing marketing campaign carried out in Poland throughout Could 2024. |
|
47AF4CFC9B250AC4AE8C |
ZAMÓWIENIE_NR.2405073. |
Win32/TrojanDownloader. |
ModiLoader executable from phishing marketing campaign carried out in Poland throughout Could 2024. |
|
2963AF32AB4D497CB41F |
N/A |
Win32/Formbook.AA |
Formbook executable from phishing marketing campaign carried out in Poland throughout Could 2024. |
|
5DAB001A2025AA91D278 |
RFQ8219000045320004. |
Win32/TrojanDownloader. |
Malicious attachment from phishing marketing campaign carried out in Poland throughout Could 2024. |
|
D88B10E4FD487BFCCA6A |
RFQ8219000045320004. |
Win32/TrojanDownloader. |
Malicious batch script from phishing marketing campaign carried out in Poland throughout Could 2024. |
|
F0295F2E46CEBFFAF789 |
N/A |
Win32/TrojanDownloader. |
ModiLoader executable from phishing marketing campaign carried out in Poland throughout Could 2024. |
|
3C0A0EC8FE9EB3E5DAB2 |
N/A |
Win32/Rescoms.B |
Rescoms executable from phishing marketing campaign carried out in Poland throughout Could 2024. |
|
9B5AF677E565FFD4B15D |
DOCUMENT_BT24PDF.IMG |
Win32/TrojanDownloader. |
Malicious attachment from phishing marketing campaign carried out in Romania throughout Could 2024. |
|
738CFBE52CFF57098818 |
DOCUMENT_BT24PDF.exe |
Win32/TrojanDownloader. |
ModiLoader executable from phishing marketing campaign carried out in Romania throughout Could 2024. |
|
843CE8848BCEEEF16D07 |
N/A |
Win32/Formbook.AA |
Formbook executable from phishing marketing campaign carried out in Romania throughout Could 2024. |
MITRE ATT&CK methods
This desk was constructed utilizing model 15 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Title |
Description |
|
Reconnaissance |
Collect Sufferer Id Data: Electronic mail Addresses |
Electronic mail addresses and speak to info (both purchased or gathered from publicly out there sources) have been utilized in phishing campaigns to focus on firms throughout a number of international locations. |
|
|
Useful resource Growth |
Compromise Accounts: Electronic mail Accounts |
Attackers used compromised e-mail accounts to ship malicious emails in phishing campaigns to extend their phishing e-mail’s credibility. |
|
|
Acquire Capabilities: Malware |
Attackers purchased licenses and used a number of malware households for phishing campaigns. |
||
|
Purchase Infrastructure: Internet Companies |
Attackers used Microsoft OneDrive to host malware. |
||
|
Compromise Infrastructure: Server |
Attackers used beforehand compromised servers to host malware and retailer stolen info. |
||
|
Preliminary Entry |
Phishing |
Attackers used phishing messages with malicious attachments to compromise computer systems and steal info from firms in a number of European international locations. |
|
|
Phishing: Spearphishing Attachment |
Attackers used spearphishing messages to compromise computer systems and steal info from firms in a number of European international locations. |
||
|
Execution |
Consumer Execution: Malicious File |
Attackers relied on customers opening archives containing malware and launching a ModiLoader executable. |
|
|
Credential Entry |
Credentials from Password Shops: Credentials from Internet Browsers |
Attackers tried to steal credential info from browsers and e-mail shoppers. |



