Cybercriminals are promoting a whole lot of 1000’s of credential units stolen with the assistance of a cracked model of Acunetix, a robust industrial internet app vulnerability scanner, new analysis finds. The cracked software program is being resold as a cloud-based assault instrument by no less than two totally different companies, considered one of which KrebsOnSecurity traced to an info know-how agency primarily based in Turkey.

Araneida Scanner.
Cyber menace analysts at Silent Push stated they not too long ago acquired reviews from a companion group that recognized an aggressive scanning effort towards their web site utilizing an Web tackle beforehand related to a marketing campaign by FIN7, a infamous Russia-based hacking group.
However on nearer inspection they found the tackle contained an HTML title of “Araneida Buyer Panel,” and located they may search on that textual content string to seek out dozens of distinctive addresses internet hosting the identical service.
It quickly grew to become obvious that Araneida was being resold as a cloud-based service utilizing a cracked model of Acunetix, permitting paying prospects to conduct offensive reconnaissance on potential goal web sites, scrape consumer knowledge, and discover vulnerabilities for exploitation.
Silent Push additionally realized Araneida bundles its service with a strong proxy providing, in order that buyer scans seem to come back from Web addresses which are randomly chosen from a big pool of accessible site visitors relays.
The makers of Acunetix, Texas-based utility safety vendor Invicti Safety, confirmed Silent Push’s findings, saying somebody had found out methods to crack the free trial model of the software program in order that it runs with out a legitimate license key.
“We now have been enjoying cat and mouse for some time with these guys,” stated Matt Sciberras, chief info safety officer at Invicti.
Silent Push stated Araneida is being marketed by an eponymous consumer on a number of cybercrime boards. The service’s Telegram channel boasts almost 500 subscribers and explains methods to use the instrument for malicious functions.
In a “Enjoyable Details” listing posted to the channel in late September, Araneida stated their service was used to take over greater than 30,000 web sites in simply six months, and that one buyer used it to purchase a Porsche with the fee card knowledge (“dumps”) they bought.
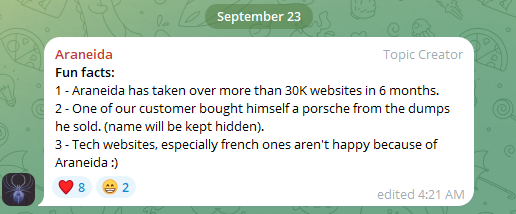
Araneida Scanner’s Telegram channel bragging about how prospects are utilizing the service for cybercrime.
“They’re always bragging with their neighborhood concerning the crimes which are being dedicated, the way it’s making criminals cash,” stated Zach Edwards, a senior menace researcher at Silent Push. “They’re additionally promoting bulk knowledge and dumps which seem to have been acquired with this instrument or as a result of vulnerabilities discovered with the instrument.”
Silent Push additionally discovered a cracked model of Acunetix was powering no less than 20 cases of the same cloud-based vulnerability testing service catering to Mandarin audio system, however they have been unable to seek out any apparently associated gross sales threads about them on the darkish internet.
Rumors of a cracked model of Acunetix being utilized by attackers surfaced in June 2023 on Twitter/X, when researchers first posited a connection between noticed scanning exercise and Araneida.
In response to an August 2023 report (PDF) from the U.S. Division of Well being and Human Providers (HHS), Acunetix (presumably a cracked model) is amongst a number of instruments utilized by APT 41, a prolific Chinese language state-sponsored hacking group.
THE TURKISH CONNECTION
Silent Push notes that the web site the place Araneida is being bought — araneida[.]co — first got here on-line in February 2023. However a evaluate of this Araneida nickname on the cybercrime boards exhibits they’ve been energetic within the prison hacking scene since no less than 2018.
A search within the menace intelligence platform Intel 471 exhibits a consumer by the title Araneida promoted the scanner on two cybercrime boards since 2022, together with Breached and Nulled. In 2022, Araneida advised fellow Breached members they might be reached on Discord on the username “Ornie#9811.”
In response to Intel 471, this similar Discord account was marketed in 2019 by an individual on the cybercrime discussion board Cracked who used the monikers “ORN” and “ori0n.” The consumer “ori0n” talked about in a number of posts that they might be reached on Telegram on the username “@sirorny.”
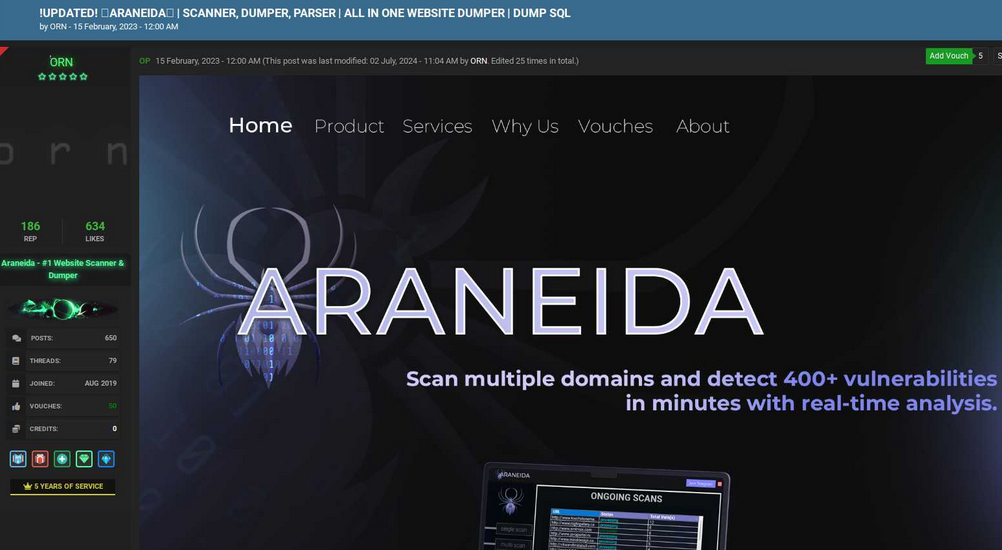
Orn promoting Araneida Scanner in Feb. 2023 on the discussion board Cracked. Picture: Ke-la.com.
The Sirorny Telegram id additionally was referenced as a degree of contact for a present consumer on the cybercrime discussion board Nulled who’s promoting web site growth companies, and who references araneida[.]co as considered one of their initiatives. That consumer, “Exorn,” has posts courting again to August 2018.
In early 2020, Exorn promoted a web site known as “orndorks[.]com,” which they described as a service for automating the scanning for web-based vulnerabilities. A passive DNS lookup on this area at DomainTools.com exhibits that its e-mail data pointed to the tackle ori0nbusiness@protonmail.com.
Constella Intelligence, an organization that tracks info uncovered in knowledge breaches, finds this e-mail tackle was used to register an account at Breachforums in July 2024 beneath the nickname “Ornie.” Constella additionally finds the identical e-mail registered on the web site netguard[.]codes in 2021 utilizing the password “ceza2003” [full disclosure: Constella is currently an advertiser on KrebsOnSecurity].
A search on the password ceza2003 in Constella finds roughly a dozen e-mail addresses that used it in an uncovered knowledge breach, most of them that includes some variation on the title “altugsara,” together with altugsara321@gmail.com. Constella additional finds altugsara321@gmail.com was used to create an account on the cybercrime neighborhood RaidForums beneath the username “ori0n,” from an Web tackle in Istanbul.
In response to DomainTools, altugsara321@gmail.com was utilized in 2020 to register the area title altugsara[.]com. Archive.org’s historical past for that area exhibits that in 2021 it featured a web site for a then 18-year-old Altuğ Şara from Ankara, Turkey.
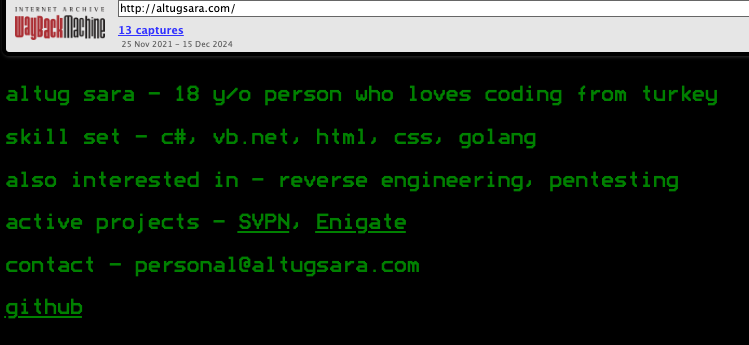
Archive.org’s recollection of what altugsara dot com appeared like in 2021.
LinkedIn finds this similar altugsara[.]com area listed within the “contact data” part of a profile for an Altug Sara from Ankara, who says he has labored the previous two years as a senior software program developer for a Turkish IT agency known as Bilitro Yazilim.
Neither Altug Sara nor Bilitro Yazilim responded to requests for remark.
Invicti’s web site states that it has places of work in Ankara, however the firm’s CEO stated none of their workers acknowledged both title.
“We do have a small group in Ankara, however so far as I do know we now have no connection to the person aside from the very fact that also they are in Ankara,” Invicti CEO Neil Roseman advised KrebsOnSecurity.
Researchers at Silent Push say regardless of Araneida utilizing a seemingly countless provide of proxies to masks the true location of its customers, it’s a pretty “noisy” scanner that can kick off a big quantity of requests to numerous API endpoints, and make requests to random URLs related to totally different content material administration techniques.
What’s extra, the cracked model of Acunetix being resold to cybercriminals invokes legacy Acunetix SSL certificates on energetic management panels, which Silent Push says offers a strong pivot for locating a few of this infrastructure, significantly from the Chinese language menace actors.
Additional studying: Silent Push’s analysis on Araneida Scanner.

