In August 2024, ESET researchers detected cyberespionage exercise carried out by the China-aligned MirrorFace superior persistent risk (APT) group towards a Central European diplomatic institute in relation to Expo 2025, which can be held in Osaka, Japan.
Identified primarily for its cyberespionage actions towards organizations in Japan, to the perfect of our data, that is the primary time MirrorFace supposed to infiltrate a European entity. The marketing campaign, which we uncovered in Q2 and Q3 of 2024 and named Operation AkaiRyū (Japanese for RedDragon), showcases refreshed ways, methods, and procedures (TTPs) that we noticed all through 2024: the introduction of recent instruments (resembling a custom-made AsyncRAT), the resurrection of ANEL, and a posh execution chain.
On this blogpost, we current particulars of the Operation AkaiRyū assaults and findings from our investigation of the diplomatic institute case, together with information from our forensic evaluation. ESET Analysis introduced the outcomes of this evaluation on the Joint Safety Analyst Convention (JSAC) in January 2025.
Key factors of this blogpost:
- MirrorFace has refreshed its TTPs and tooling.
- MirrorFace has began utilizing ANEL, a backdoor beforehand related solely with APT10.
- MirrorFace has began deploying a closely custom-made variant of AsyncRAT, utilizing a posh execution chain to run it inside Home windows Sandbox.
- To our data, MirrorFace focused a European entity for the primary time.
- We collaborated with the affected Central European diplomatic institute and carried out a forensic investigation.
- The findings obtained throughout that investigation have supplied us with higher perception into MirrorFace’s post-compromise actions.
MirrorFace profile
MirrorFace, also referred to as Earth Kasha, is a China-aligned risk actor till now virtually solely focusing on corporations and organizations in Japan but in addition some positioned elsewhere which have relationships with Japan. As defined on this blogpost, we now think about MirrorFace to be a subgroup below the APT10 umbrella. MirrorFace has been energetic since at the very least 2019 and has been reported to focus on media, defense-related corporations, suppose tanks, diplomatic organizations, monetary establishments, tutorial establishments, and producers. In 2022, we found a MirrorFace spearphishing marketing campaign focusing on Japanese political entities.
MirrorFace focuses on espionage and exfiltration of information of curiosity; it’s the solely group recognized to make use of the LODEINFO and HiddenFace backdoors. Within the 2024 actions analyzed on this blogpost, MirrorFace began utilizing APT10’s former signature backdoor, ANEL, in its operations as nicely.
Overview
Very like earlier MirrorFace assaults, Operation AkaiRyū started with rigorously crafted spearphishing emails designed to entice recipients to open malicious attachments. Our findings recommend that regardless of this group’s foray past the borders of its traditional looking floor, the risk actor nonetheless maintains a powerful concentrate on Japan and occasions tied to the nation. Nonetheless, this isn’t the primary time MirrorFace has been reported to function outdoors of Japan: Development Micro and the Vietnamese Nationwide Cyber Safety Middle (doc in Vietnamese) reported on such circumstances in Taiwan, India, and Vietnam.
ANEL’s comeback
Throughout our evaluation of Operation AkaiRyū, we found that MirrorFace has considerably refreshed its TTPs and tooling. MirrorFace began utilizing ANEL (additionally known as UPPERCUT) – a backdoor thought of unique to APT10 – which is stunning, because it was believed that ANEL was deserted across the finish of 2018 or the beginning of 2019 and that LODEINFO succeeded it, showing later in 2019. The small distinction in model numbers between 2018 and 2024 ANELs, 5.5.0 and 5.5.4, and the truth that APT10 used to replace ANEL each few months, strongly recommend that the event of ANEL has restarted.
Using ANEL additionally supplies additional proof within the ongoing debate in regards to the potential connection between MirrorFace and APT10. The truth that MirrorFace has began utilizing ANEL, and the opposite beforehand recognized data, resembling comparable focusing on and malware code similarities, led us to make a change in our attribution: we now consider that MirrorFace is a subgroup below the APT10 umbrella. This attribution change aligns our considering with different researchers who already think about MirrorFace to be part of APT10, resembling these at Macnica (report in Japanese), Kaspersky, ITOCHU Cyber & Intelligence Inc., and Cybereason. Others, as at Development Micro, as of now nonetheless think about MirrorFace to be solely probably associated to APT10.
First use of AsyncRAT and Visible Studio Code by MirrorFace
In 2024, MirrorFace additionally deployed a closely custom-made variant of AsyncRAT, embedding this malware right into a newly noticed, intricate execution chain that runs the RAT inside Home windows Sandbox. This technique successfully obscures the malicious actions from safety controls and hamstrings efforts to detect the compromise.
In parallel to the malware, MirrorFace additionally began deploying Visible Studio Code (VS Code) to abuse its distant tunnels function. Distant tunnels allow MirrorFace to ascertain stealthy entry to the compromised machine, execute arbitrary code, and ship different instruments. MirrorFace just isn’t the one APT group abusing VS Code: Tropic Trooper and Mustang Panda have additionally been reported utilizing it of their assaults.
Moreover, MirrorFace continued to make use of its present flagship backdoor, HiddenFace, additional bolstering persistence on compromised machines. Whereas ANEL is utilized by MirrorFace because the first-line backdoor, proper after the goal has been compromised, HiddenFace is deployed within the later phases of the assault. It is usually price noting that in 2024 we didn’t observe any use of LODEINFO, one other backdoor used solely by MirrorFace.
Forensic evaluation of the compromise
We contacted the affected institute to tell them in regards to the assault and to scrub up the compromise as quickly as attainable. The institute collaborated intently with us throughout and after the assault, and moreover supplied us with the disk photos from the compromised machines. This enabled us to carry out forensic analyses on these photos and uncover additional MirrorFace exercise.
ESET Analysis supplied extra technical particulars about ANEL’s return to ESET Menace Intelligence prospects on September 4th, 2024. Development Micro printed their findings on then-recent MirrorFace actions on October 21st, 2024 in Japanese and on November 26th, 2024 in English: these overlap with Operation AkaiRyū and in addition point out the return of the ANEL backdoor. Moreover, in January 2025, the Japanese Nationwide Police Company (NPA) printed a warning about MirrorFace actions to organizations, companies, and people in Japan. Operation AkaiRyū corresponds with Marketing campaign C, as talked about within the Japanese model of NPA’s warning. Nonetheless, NPA mentions the focusing on of Japanese entities solely – people and organizations primarily associated to academia, suppose tanks, politics, and the media.
Along with Development Micro’s report and NPA’s warning, we offer an unique evaluation of MirrorFace post-compromise actions, which we had been capable of observe because of the shut cooperation of the affected group. This consists of the deployment of a closely custom-made AsyncRAT, abuse of VS Code distant tunnels, and particulars on the execution chain that runs malware inside Home windows Sandbox to keep away from detection and conceal the carried out actions.
On this blogpost, we cowl two distinct circumstances: a Central European diplomatic institute and a Japanese analysis institute. Regardless that MirrorFace’s total strategy is similar in each circumstances, there are notable variations within the preliminary entry course of; therefore we describe them each.
Technical evaluation
Between June and September 2024, we noticed MirrorFace conducting a number of spearphishing campaigns. Based mostly on our information, the attackers primarily gained preliminary entry by tricking targets into opening malicious attachments or hyperlinks, then they leveraged reliable purposes and instruments to stealthily set up their malware.
Preliminary entry
We weren’t capable of decide the preliminary assault vector for all of the circumstances noticed in 2024. Nonetheless, primarily based on the information obtainable to us, we assume that spearphishing was the one assault vector utilized by MirrorFace. The group impersonates trusted organizations or people to persuade recipients to open paperwork or click on hyperlinks. The next findings on preliminary entry align with these within the Development Micro article, though they don’t seem to be completely the identical.
Particularly, in Operation AkaiRyū, MirrorFace abused each McAfee-developed purposes and in addition one developed by JustSystems to run ANEL. Whereas Development Micro reported Home windows Administration Instrumentation (WMI) and explorer.exe because the execution proxy pair for ANEL, we unearthed one other pair: WMI and wlrmdr.exe (Home windows logon reminder). We additionally present an electronic mail dialog between a disguised MirrorFace operator and a goal.
Case 1: Japanese analysis institute
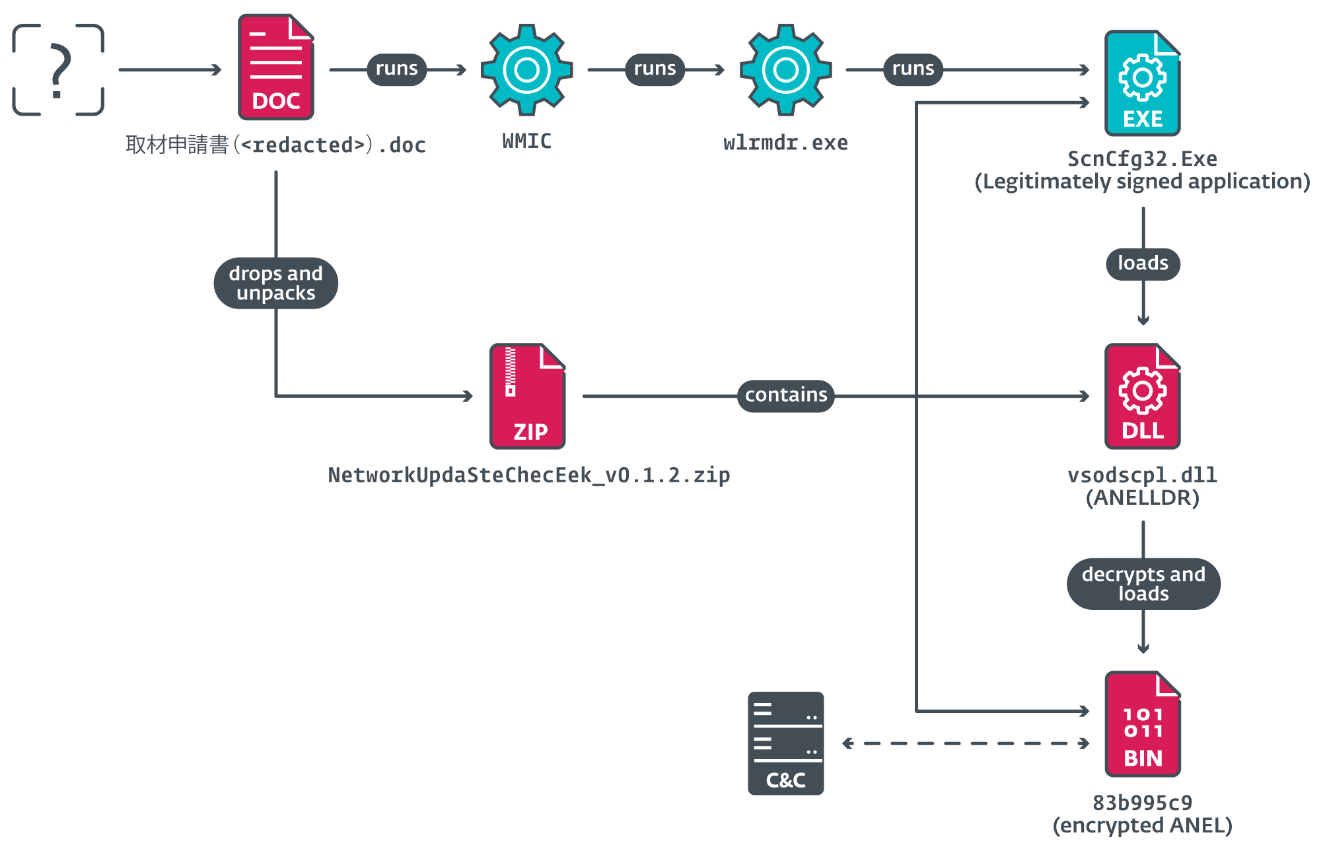
On June 20th, 2024, MirrorFace focused two staff of a Japanese analysis institute, utilizing a malicious, password-protected Phrase doc delivered in an unknown method.
The paperwork triggered VBA code on a easy mouseover occasion – the malicious code was triggered by shifting the mouse over textual content containers positioned within the doc. It then abused a signed McAfee executable to load ANEL (model 5.5.4) into reminiscence. The compromise chain is depicted in Determine 1.
Case 2: Central European diplomatic institute
On August 26th, 2024, MirrorFace focused a Central European diplomatic institute. To our data, that is the primary, and, to this point, solely time MirrorFace has focused an entity in Europe.
MirrorFace operators arrange their spearphishing assault by crafting an electronic mail message (proven in Determine 2) that references a earlier, reliable interplay between the institute and a Japanese NGO. The reliable interplay was in all probability obtained from a earlier marketing campaign. As could be seen, this spearphishing arrange message refers back to the upcoming Expo 2025 exhibition, an occasion that can be held in Japan.
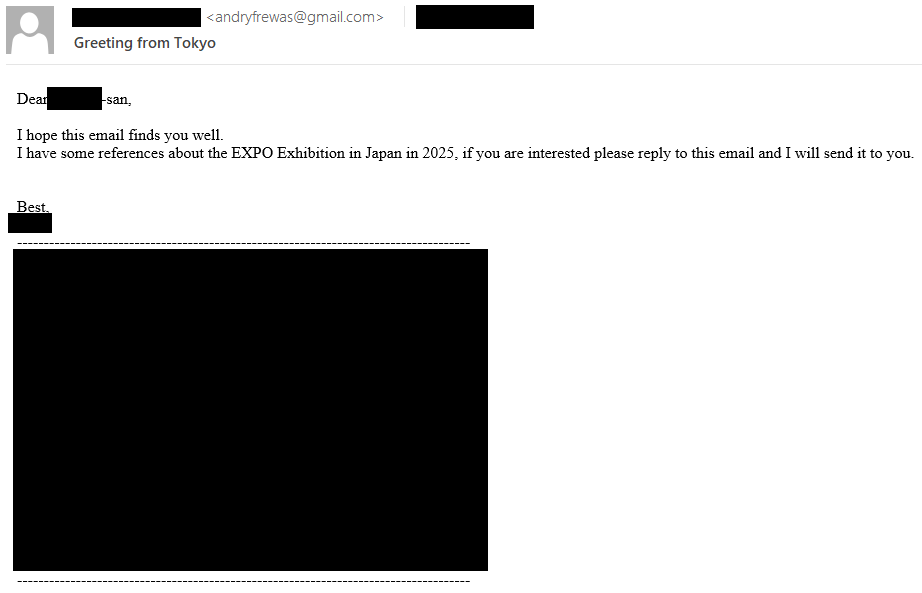
This primary electronic mail was innocent, however as soon as the goal responded, MirrorFace operators despatched an electronic mail message with a malicious OneDrive hyperlink resulting in a ZIP archive with a LNK file disguised as a Phrase doc named The EXPO Exhibition in Japan in 2025.docx.lnk. This second message is proven in Determine 3. Utilizing this strategy, MirrorFace hid the payload till the goal was engaged within the spearphishing scheme.

As soon as opened, the LNK file launches a posh compromise chain, depicted in Determine 4 and Determine 5.
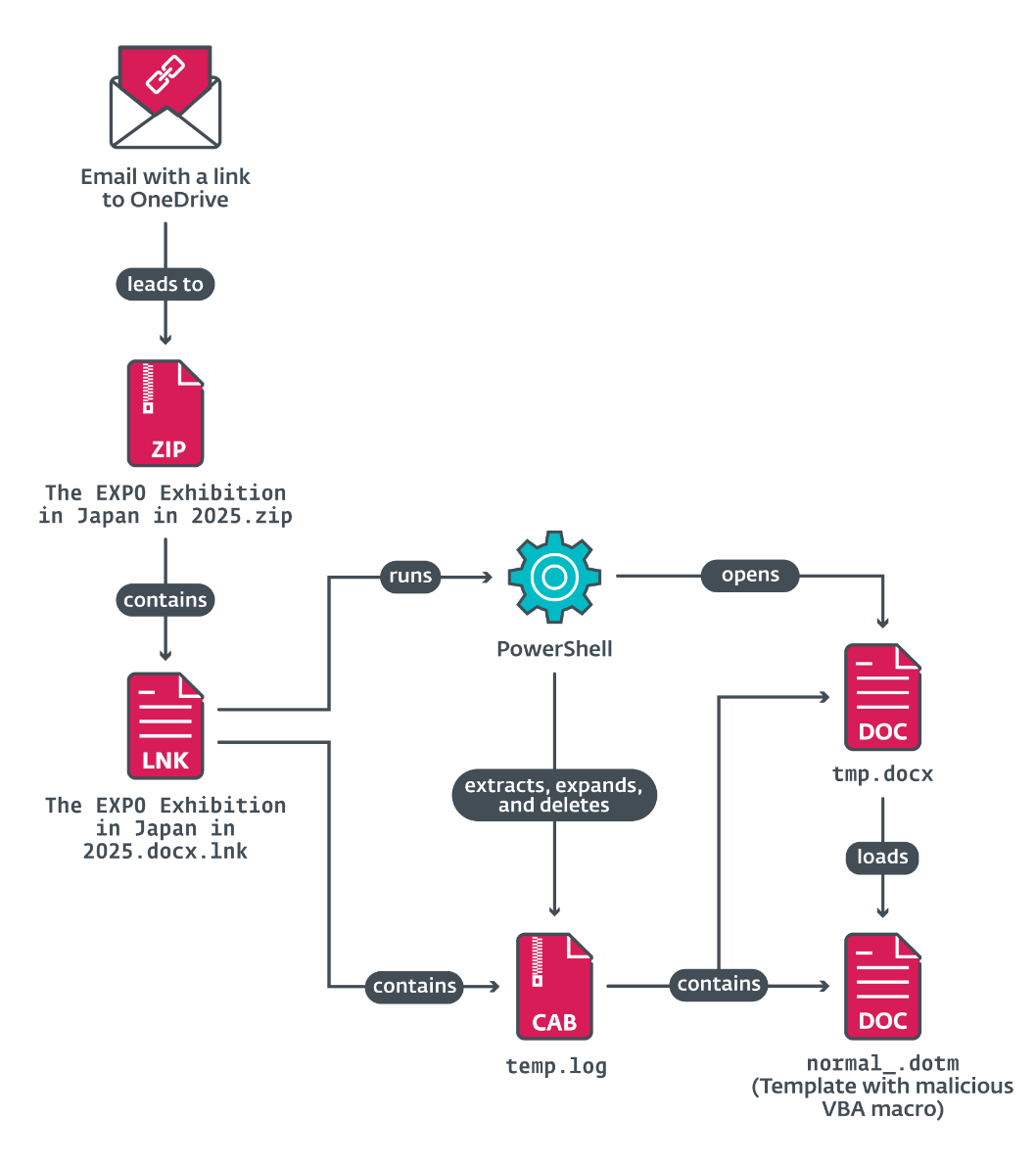
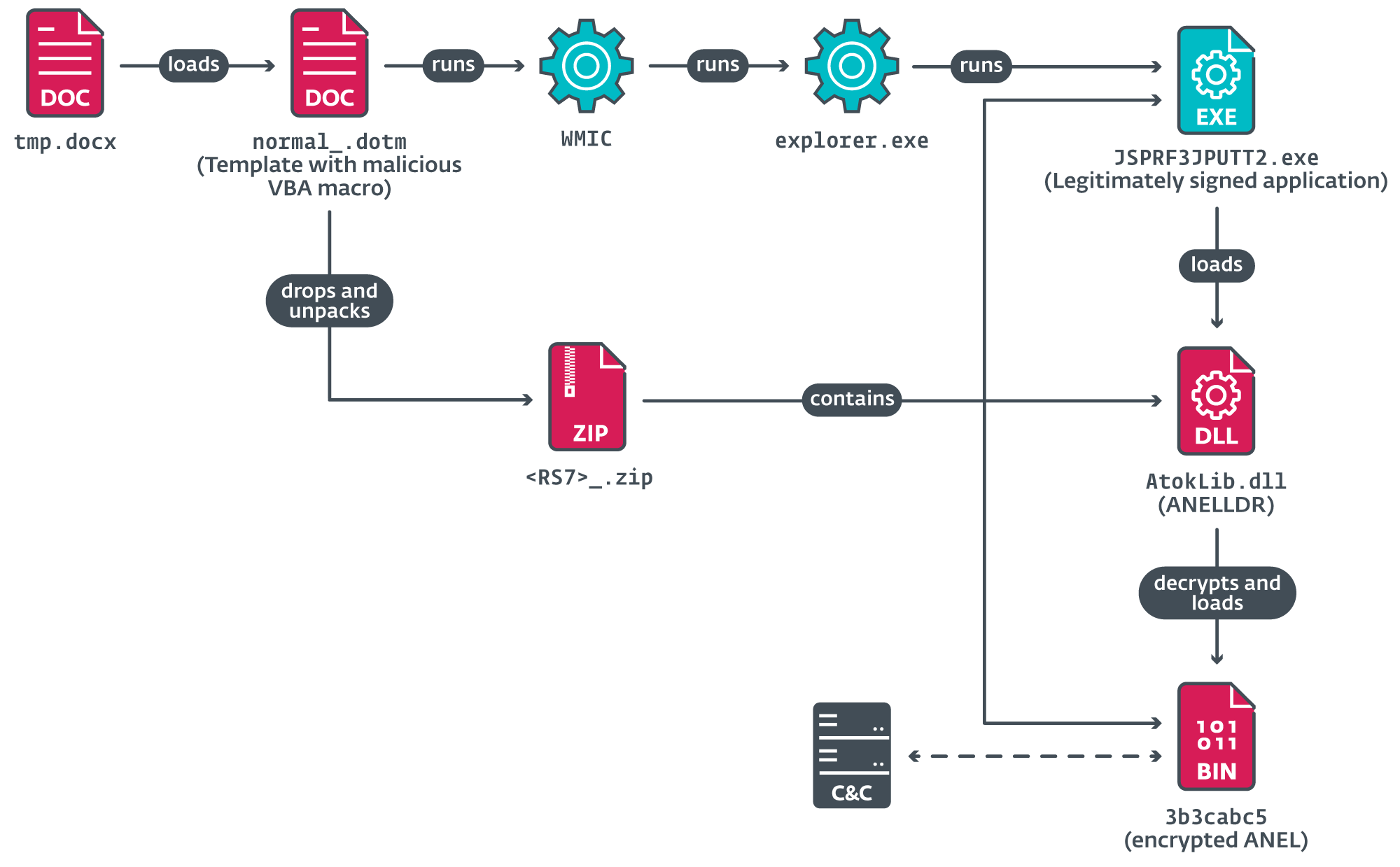
The LNK file runs cmd.exe with a set of PowerShell instructions to drop extra information, together with a malicious Phrase file, tmp.docx, which hundreds a malicious Phrase template, normal_.dotm, containing VBA code. The contents of the Phrase doc tmp.docx are depicted in Determine 6, and doubtless are supposed to behave as a decoy, whereas malicious actions are working within the background.

The VBA code extracts a legitimately signed utility from JustSystems Company to side-load and decrypt the ANEL backdoor (model 5.5.5). This gave MirrorFace a foothold to start post-compromise operations.
Toolset
In Operation AkaiRyū, MirrorFace relied not solely on its customized malware, but in addition on varied instruments and a custom-made variant of a publicly obtainable distant entry trojan (RAT).
ANEL
ANEL (also referred to as UPPERCUT) is a backdoor that was beforehand related solely with APT10. In 2024, MirrorFace began utilizing ANEL as its first-line backdoor. ANEL’s growth, till 2018, was described most not too long ago in Secureworks’ JSAC 2019 presentation. The ANEL variants noticed in 2024 had been publicly described by Development Micro.
ANEL is a backdoor, solely discovered on disk in an encrypted kind, and whose decrypted DLL kind is simply ever present in reminiscence as soon as a loader has decrypted it in preparation for execution. ANEL communicates with its C&C server over HTTP, the place the transmitted information is encrypted to guard it in case the communication is being captured. ANEL helps primary instructions for file manipulation, payload execution, and taking a screenshot.
ANELLDR
ANELLDR is a loader solely used to decrypt the ANEL backdoor and run it in reminiscence. Development Micro described ANELLDR of their article.
HiddenFace
HiddenFace is MirrorFace’s present flagship backdoor, with a heavy concentrate on modularity; we described it intimately on this JSAC 2024 presentation.
FaceXInjector
FaceXInjector is a C# injection instrument saved in an XML file, compiled and executed by the Microsoft MSBuild utility, and used to solely execute HiddenFace. We described FaceXInjector in the identical JSAC 2024 presentation devoted to HiddenFace.
AsyncRAT
AsyncRAT is a RAT publicly obtainable on GitHub. In 2024, we detected that MirrorFace began utilizing a closely custom-made AsyncRAT within the later phases of its assaults. The group ensures AsyncRAT’s persistence by registering a scheduled job that executes at machine startup; as soon as triggered, a posh chain (depicted in Determine 7) launches AsyncRAT inside Home windows Sandbox, which have to be manually enabled and requires a reboot. We had been unable to find out how MirrorFace allows this function.
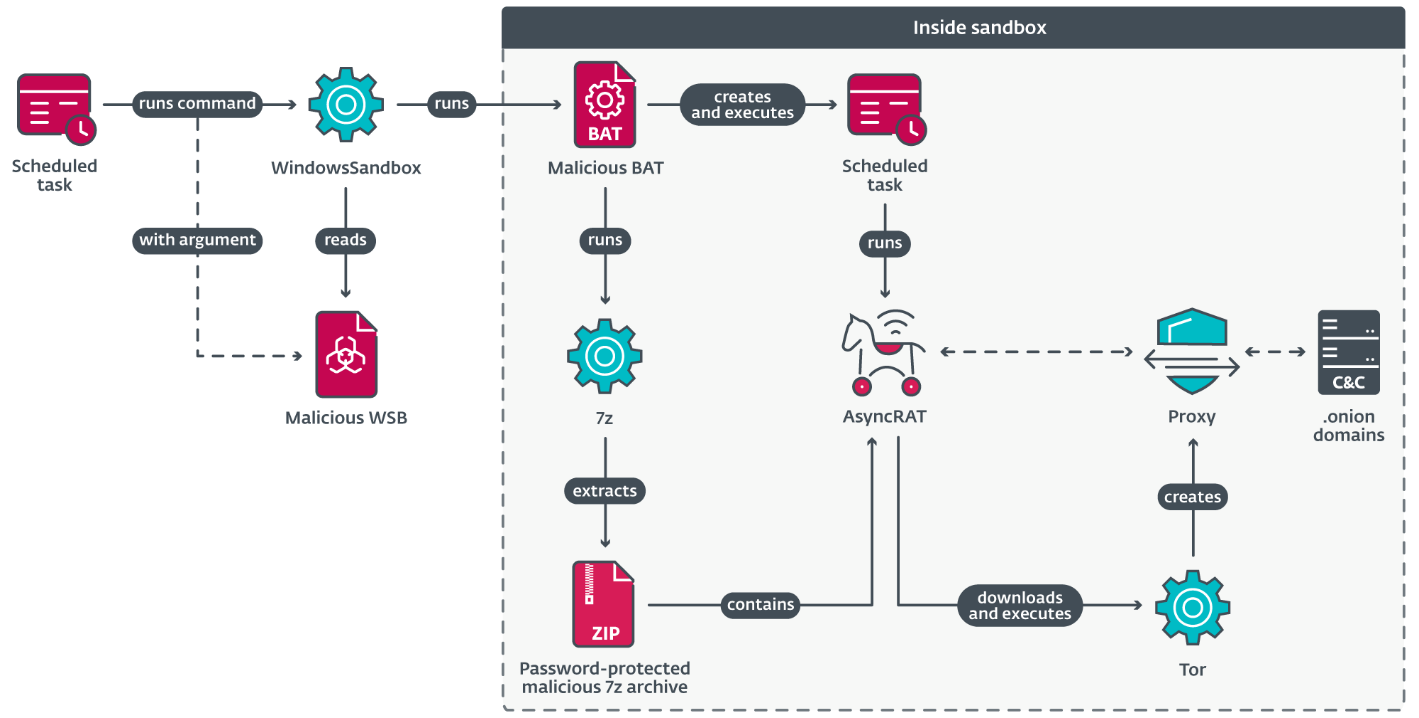
The next information are delivered to the compromised machine so as to efficiently execute AsyncRAT:
- 7z.exe – reliable 7-Zip executable.
- 7z.dll – reliable 7-Zip library.
- <random>.7z – password-protected 7z archive containing AsyncRAT, named setup.exe.
- <random>.bat – batch script that unpacks AsyncRAT and runs it.
- <random>.wsb – Home windows Sandbox configuration file to run <random>.bat.
The triggered scheduled job executes Home windows Sandbox with <random>.wsb as a parameter. This file incorporates configuration information for the sandbox; see Determine 8.
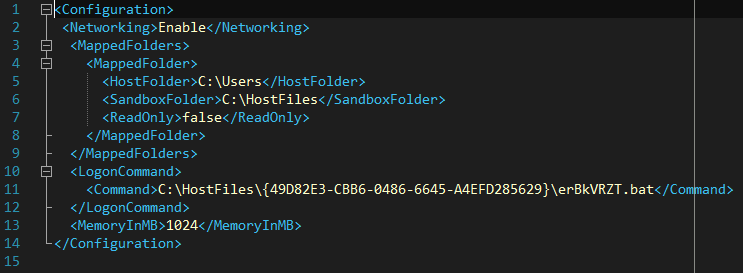
Particularly, the config file defines whether or not to allow networking and listing mapping, the devoted reminiscence measurement, and the command to execute on launch. Within the file proven in Determine 8, a batch file positioned within the sandbox folder is executed. The batch file extracts AsyncRAT from the 7z archive, then creates and launches a scheduled job that executes AsyncRAT each hour.
The AsyncRAT variant utilized by MirrorFace is closely custom-made. The next are the primary options and adjustments launched by MirrorFace:
- Pattern tagging – AsyncRAT could be compiled for a particular sufferer and MirrorFace can add a tag to the configuration to mark the pattern. If the tag just isn’t specified, the machine’s NetBIOS title is used because the tag. This tag is additional utilized in different launched options as nicely.
- Connection to a C&C server through Tor – MirrorFace’s AsyncRAT can obtain and begin a Tor consumer, and proxy its communication with a C&C server by way of the consumer. AsyncRAT selects this feature provided that the hardcoded C&C domains finish with .onion. This strategy was chosen in each samples we noticed in the course of the investigation of Case 2: Central European diplomatic institute.
- Area technology algorithm (DGA) – A substitute for utilizing Tor, this variant can use a DGA to generate a C&C area. The DGA also can generate machine-specific domains utilizing the aforementioned tag. Be aware that HiddenFace additionally makes use of a DGA with the potential for producing machine-specific domains, though the DGA utilized in HiddenFace differs from the AsyncRAT one.
- Working time – Earlier than connecting to a C&C server, AsyncRAT checks whether or not the present hour and day of the week are inside working hours and days outlined within the configuration. Be aware that MirrorFace’s AsyncRAT shares this function with HiddenFace as nicely.
Visible Studio Code distant tunnels
Visible Studio Code is a free source-code editor developed by Microsoft. Visible Studio Code’s distant growth function, distant tunnels, permits builders to run Visible Studio Code domestically and connect with a growth machine that hosts the supply code and debugging atmosphere. Menace actors can misuse this to achieve distant entry, execute code, and ship instruments to a compromised machine. MirrorFace has been doing so since 2024; nevertheless, it isn’t the one APT group that has used such distant tunnels: different China-aligned APT teams resembling Tropic Trooper and Mustang Panda have additionally used them of their assaults.
Submit-compromise actions
Our investigation into Case 2: Central European diplomatic institute uncovered a few of MirrorFace’s post-compromise actions. By way of shut collaboration with the institute, we gained higher perception into the malware and instruments deployed by MirrorFace, as seen in Desk 1.
Be aware that the malware and instruments are ordered within the desk for simpler comparability of what was deployed on every of the 2 recognized compromised machines however doesn’t replicate how they had been deployed chronologically.
Desk 1. Malware and instruments deployed by MirrorFace all through the assault
| Instruments | Notes | Machine A | Machine B |
| ANEL | APT10’s backdoor that MirrorFace makes use of as a first-line backdoor. |
● |
● |
| PuTTY | An open-source terminal emulator, serial console, and community file switch utility. | ● | ● |
| VS Code | A code editor developed by Microsoft. | ● | ● |
| HiddenFace | MirrorFace’s flagship backdoor. | ● | ● |
| Second HiddenFace variant | MirrorFace’s flagship backdoor. | ● | |
| AsyncRAT | RAT publicly obtainable on GitHub. | ● | ● |
| Hidden Begin | A instrument that can be utilized to bypass UAC, conceal Home windows consoles, and run applications within the background. | ● | |
| csvde | Authentic Microsoft instrument obtainable on Home windows servers that imports and exports information from Energetic Listing Area Companies (AD DS). | ● | |
| Rubeus | Toolset for Kerberos interplay and abuse, publicly obtainable on GitHub. | ● | |
| frp | Quick reverse proxy publicly obtainable on GitHub. | ● | |
| Unknown instrument | Disguised below the title oneuu.exe. We had been unable to get well the instrument throughout our evaluation. | ● |
The group selectively deployed post-compromise instruments in keeping with its goals and the goal’s atmosphere. Machine A belonged to a undertaking coordinator and Machine B to an IT worker. The info obtainable to us means that MirrorFace stole private information from Machine A and sought deeper community entry on Machine B, aligning the assumed goals with the staff’ roles.
Day 0 – August 27th, 2024
MirrorFace operators despatched an electronic mail with a malicious hyperlink on August 26th, 2024 to the institute’s CEO. Nonetheless, because the CEO didn’t have entry to a machine working Home windows, the CEO forwarded the e-mail to 2 different staff. Each opened the dangerous LNK file, The EXPO Exhibition in Japan in 2025.docx.lnk, the following day, compromising two institute machines and resulting in the deployment of ANEL. Thus, we think about August 27th, 2024, as Day 0 of the compromise. No extra exercise was noticed past this foothold institution.
Day 1 – August 28th, 2024
The subsequent day, MirrorFace returned and continued with its actions. The group deployed a number of instruments for entry, management, and file supply on each compromised machines. Among the many instruments deployed had been PuTTY, VS Code, and HiddenFace – MirrorFace’s present flagship backdoor. On Machine A, MirrorFace additionally tried to deploy the instrument Hidden Begin. On Machine B, the actor moreover deployed csvde and the custom-made variant of AsyncRAT.
Day 2 – August 29th, 2024
On Day 2, MirrorFace was energetic on each machines. This included deploying extra instruments. On Machine A, MirrorFace deployed a second occasion of HiddenFace. On Machine B, VS Code’s distant tunnel, HiddenFace, and AsyncRAT had been executed. Apart from these, MirrorFace additionally deployed and executed frp and Rubeus through HiddenFace. That is the final day on which we noticed any MirrorFace exercise on Machine B.
Day 3 – August 30th, 2024
MirrorFace remained energetic solely on Machine A. The institute, having began assault mitigation measures on August 29th, 2024, may need prevented additional MirrorFace exercise on Machine B. On Machine A, the group deployed AsyncRAT and tried to take care of persistence by registering a scheduled job.
Day 6 – September 2nd, 2024
Over the weekend, i.e., on August 31st and September 1st, 2024, Machine A was inactive. On Monday, September 2nd, 2024, Machine A was booted and with it MirrorFace’s exercise resumed as nicely. The primary occasion of Day 6 was that the group exported Google Chrome’s net information resembling contact data, key phrases, autofill information, and saved bank card data right into a SQLite database file. We had been unable to find out how MirrorFace exported the information, and whether or not or how the information was exfiltrated.
Conclusion
In 2024, MirrorFace refreshed its TTPs and tooling. It began utilizing ANEL – believed to have been deserted round 2018/2019 – as its first-line backdoor. Mixed with different data, we conclude that MirrorFace is a subgroup below the APT10 umbrella. Apart from ANEL, MirrorFace has additionally began utilizing different instruments resembling a closely custom-made AsyncRAT, Home windows Sandbox, and VS Code distant tunnels.
As part of Operation AkaiRyū, MirrorFace focused a Central European diplomatic institute – to the perfect of our data, that is the primary time the group has attacked an entity in Europe – utilizing the identical refreshed TTPs seen throughout its 2024 campaigns. Throughout this assault, the risk actor used the upcoming World Expo 2025 – to be held in Osaka, Japan – as a lure. This exhibits that even contemplating this new broader geographic focusing on, MirrorFace stays centered on Japan and occasions associated to it.
Our shut collaboration with the affected group supplied a uncommon, in-depth view of post-compromise actions that may have in any other case gone unseen. Nonetheless, there are nonetheless numerous lacking items of the puzzle to attract a whole image of the actions. One of many causes is MirrorFace’s improved operational safety, which has turn out to be extra thorough and hinders incident investigations by deleting the delivered instruments and information, clearing Home windows occasion logs, and working malware in Home windows Sandbox.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis affords personal APT intelligence studies and information feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
A complete checklist of indicators of compromise (IoCs) and samples could be present in our GitHub repository.
Recordsdata
| SHA-1 | Filename | Detection | Description |
| 018944FC47EE2329B23B |
3b3cabc5 | Win32/MirrorFace.A | AES-encrypted ANEL. |
| 68B72DA59467B1BB477D |
vsodscpl.dll | Win32/MirrorFace.A | ANELLDR. |
| 02D32978543B9DD1303E |
AtokLib.dll | Win32/MirrorFace.A | ANELLDR. |
| 2FB3B8099499FEE03EA7 |
CodeStartUser.bat | Win32/MirrorFace.A | Malicious batch file. |
| 9B2B9A49F52B37927E6A |
erBkVRZT.bat | Win32/MirrorFace.A | Malicious batch file. |
| AB65C08DA16A45565DBA |
useractivitybroker.xml | Win32/ FaceXInjector.A | FaceXInjector. |
| 875DC27963F8679E7D8B |
temp.log | Win32/MirrorFace.A | Malicious CAB file. |
| 694B1DD3187E876C5743 |
tmp.docx | Win32/MirrorFace.A | Decoy Phrase |
| F5BA545D4A1683675698 |
normal_.dotm | Win32/MirrorFace.A | Phrase template with |
| 233029813051D20B61D0 |
The EXPO |
Win32/MirrorFace.A | Malicious LNK file. |
| 8361F7DBF81093928DA5 |
The EXPO |
Win32/MirrorFace.A | Malicious ZIP archive. |
| 1AFDCE38AF37B9452FB4 |
NK9C4PH_.zip | Win32/MirrorFace.A | Malicious ZIP archive. |
| E3DA9467D0C89A9312EA |
N/A | MSIL/Riskware.Rubeus.A | Rubeus instrument. |
| D2C25AF9EE6E60A341B0 |
Tk4AJbXk.wsb | Win32/MirrorFace.A | Malicious Home windows |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| N/A | vu4fleh3yd4ehpfpc |
N/A | 2024‑08‑28 | MirrorFace’s AsyncRAT C&C server. |
| N/A | u4mrhg3y6jyfw2dmm |
N/A | 2024‑08‑28 | MirrorFace’s AsyncRAT C&C server. |
| 45.32.116[.]146 | N/A | The Fixed Firm, LLC | 2024‑08‑27 | ANEL C&C server. |
| 64.176.56[.]26 | N/A | The Fixed Firm, LLC | N/A | Distant server for FRP consumer. |
| 104.233.167[.]135 | N/A | PEG-TKY1 | 2024‑08‑27 | HiddenFace C&C server. |
| 152.42.202[.]137 | N/A | DigitalOcean, LLC | 2024‑08‑27 | HiddenFace C&C server. |
| 208.85.18[.]4 | N/A | The Fixed Firm, LLC | 2024‑08‑27 | ANEL C&C server. |
MITRE ATT&CK methods
This desk was constructed utilizing model 16 of the MITRE ATT&CK framework.
| Tactic | ID | Title | Description |
| Useful resource Improvement | T1587.001 | Develop Capabilities: Malware | MirrorFace has developed customized instruments resembling HiddenFace. |
| T1585.002 | Set up Accounts: Electronic mail Accounts | MirrorFace created a Gmail account and used it to ship a spearphishing electronic mail. | |
| T1585.003 | Set up Accounts: Cloud Accounts | MirrorFace created a OneDrive account to host malicious information. | |
| T1588.001 | Get hold of Capabilities: Malware | MirrorFace utilized and customised a publicly obtainable RAT, AsyncRAT, for its operations. | |
| T1588.002 | Get hold of Capabilities: Software | MirrorFace utilized Hidden Begin in its operations. | |
| Preliminary Entry | T1566.002 | Phishing: Spearphishing Hyperlink | MirrorFace despatched a spearphishing electronic mail with a malicious OneDrive hyperlink. |
| Execution | T1053.005 | Scheduled Process/Job: Scheduled Process | MirrorFace used scheduled duties to execute HiddenFace and AsyncRAT. |
| T1059.001 | Command-Line Interface: PowerShell | MirrorFace used PowerShell instructions to run Visible Studio Code’s distant tunnels. | |
| T1059.003 | Command-Line Interface: Home windows Command Shell | MirrorFace used the Home windows command shell to make sure persistence for HiddenFace. | |
| T1204.001 | Person Execution: Malicious Hyperlink | MirrorFace relied on the goal to obtain a malicious file from a shared OneDrive hyperlink. | |
| T1204.002 | Person Execution: Malicious File | MirrorFace relied on the goal to run a malicious LNK file that deploys ANEL. | |
| T1047 | Home windows Administration Instrumentation | MirrorFace used WMI as an execution proxy to run ANEL. | |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ANEL makes use of one of many startup directories for persistence. |
| T1574.001 | Hijack Execution Move: DLL Search Order Hijacking | MirrorFace side-loads ANEL by dropping a malicious library and a reliable executable (e.g., ScnCfg32.Exe) | |
| Protection Evasion | T1027.004 | Obfuscated Recordsdata or Info: Compile After Supply | FaceXInjector is compiled on each scheduled job run. |
| T1027.007 | Obfuscated Recordsdata or Info: Dynamic API Decision | HiddenFace dynamically resolves the required APIs upon its startup. | |
| T1027.011 | Obfuscated Recordsdata or Info: Fileless Storage | HiddenFace is saved in a registry key on the compromised machine. | |
| T1055 | Course of Injection | FaceXInjector is used to inject HiddenFace right into a reliable Home windows utility. | |
| T1070.004 | Indicator Elimination: File Deletion | As soon as HiddenFace is moved to the registry, the file through which it was delivered is deleted. | |
| T1070.006 | Indicator Elimination: Timestomp | HiddenFace can timestomp information in chosen directories. | |
| T1112 | Modify Registry | FaceXInjector creates a registry key into which it shops HiddenFace. | |
| T1127.001 | Trusted Developer Utilities: MSBuild | MSBuild is abused to execute FaceXInjector. | |
| T1140 | Deobfuscate/Decode Recordsdata or Info | HiddenFace reads exterior modules from an AES-encrypted file. | |
| T1622 | Debugger Evasion | HiddenFace checks whether or not it’s being debugged. | |
| T1564.001 | Cover Artifacts: Hidden Recordsdata and Directories | MirrorFace hid directories with AsyncRAT. | |
| T1564.003 | Cover Artifacts: Hidden Window | MirrorFace tried to make use of the instrument Hidden Begin, which may conceal home windows. | |
| T1564.006 | Cover Artifacts: Run Digital Occasion | MirrorFace used Home windows Sandbox to run AsyncRAT. | |
| T1070.001 | Indicator Elimination: Clear Home windows Occasion Logs | MirrorFace cleared Home windows occasion logs to destroy proof of its actions. | |
| T1036.007 | Masquerading: Double File Extension | MirrorFace used a so-called double file extension, .docx.lnk, to deceive its goal. | |
| T1218 | Signed Binary Proxy Execution | MirrorFace used wlrmdr.exe as an execution proxy to run ANEL. | |
| T1221 | Template Injection | MirrorFace used Phrase template injection to run malicious VBA code. | |
| Discovery | T1012 | Question Registry | HiddenFace queries the registry for machine-specific data such because the machine ID. |
| T1033 | System Proprietor/Person Discovery | HiddenFace determines the presently logged in person’s title and sends it to the C&C server. | |
| T1057 | Course of Discovery | HiddenFace checks presently working processes. | |
| T1082 | System Info Discovery | HiddenFace gathers varied system data and sends it to the C&C server. | |
| T1124 | System Time Discovery | HiddenFace determines the system time and sends it to the C&C server. | |
| T1087.002 | Account Discovery: Area Account | MirrorFace used the instrument csvde to export information from Energetic Listing Area Companies. | |
| Assortment | T1115 | Clipboard Information | HiddenFace collects clipboard information and sends it to the C&C server. |
| T1113 | Display Seize | ANEL can take a screenshot and ship it to the C&C server. | |
| Command and Management | T1001.001 | Information Obfuscation: Junk Information | HiddenFace provides junk information to the messages despatched to the C&C server. |
| T1568.002 | Dynamic Decision: Area Era Algorithms | HiddenFace makes use of a DGA to generate C&C server domains. | |
| T1573 | Encrypted Channel | HiddenFace communicates with its C&C server over an encrypted channel. | |
| T1071.001 | Commonplace Utility Layer Protocol: Internet Protocols | ANEL makes use of HTTP to speak with its C&C server. | |
| T1132.001 | Information Encoding: Commonplace Encoding | ANEL makes use of base64 to encode information despatched to the C&C server. | |
| Exfiltration | T1030 | Information Switch Dimension Limits | HiddenFace can, upon operator request, cut up information and ship it in chunks to the C&C server. |
| T1041 | Exfiltration Over C2 Channel | HiddenFace exfiltrates requested information to the C&C server. |


