Cybercrime
Chances are you’ll not all the time cease your private info from ending up within the web’s darkish recesses, however you may take steps to guard your self from criminals trying to exploit it
29 Oct 2024
•
,
6 min. learn

How did 44% members of the European Parliament (MEPs) and 68% of British MPs let their private particulars find yourself circulating on the darkish net? The reply is easier and probably extra alarming than you could suppose: many can have signed as much as on-line accounts utilizing their official electronic mail tackle, and entered extra personally identifiable info (PII). They are going to then have been helpless as that third-party supplier was breached by cybercriminals, who subsequently shared or offered the info to different menace actors on the darkish net.
Sadly, this isn’t one thing confined to politicians or others within the public eye and it’s not the one means one’s information can find yourself within the web’s seedy underbelly. It may occur to anybody – probably even after they do the whole lot appropriately. And steadily, it does occur. That’s why it pays to maintain a more in-depth eye in your digital footprint and the info that issues most to you.
The darkish net is flourishing
First issues first: Opposite to in style assumption, the darkish net shouldn’t be unlawful and it’s not populated solely by cybercriminals. It merely refers to elements of the web that aren’t listed by conventional search engines like google and yahoo: a spot the place customers can roam anonymously utilizing Tor Browser.
Nonetheless, it’s additionally true to say that in the present day’s cybercrime economic system has been constructed on a thriving darkish net, with most of the devoted boards and marketplaces visited by cybercriminals of their droves whereas being hidden from legislation enforcement. (That mentioned, a number of the nefarious actions have more and more been spilling onto well-known social media platforms lately.)
As an enabler for a legal economic system price trillions, the darkish internet sites permit menace actors to purchase and promote stolen information, hacking instruments, DIY guides, service-based choices and rather more – with impunity. Regardless of periodic crackdowns by legislation enforcement, these websites proceed to adapt, with new platforms rising to fill the gaps left as earlier incumbents are dismantled by the authorities.
When Proton and Constella Intelligence researchers went trying, they discovered {that a} staggering two-fifths (40%) of British, European and French parliamentarians’ electronic mail addresses had been uncovered on the darkish net. That’s almost 1,000 out of a doable 2,280 emails. Even worse, 700 of those emails had passwords related to them saved in plain textual content and uncovered on darkish internet sites. When mixed with different uncovered info together with dates of beginning, house addresses, and social media account handles, they supply a treasure trove of identification information that can be utilized in follow-on phishing assaults and identification fraud.
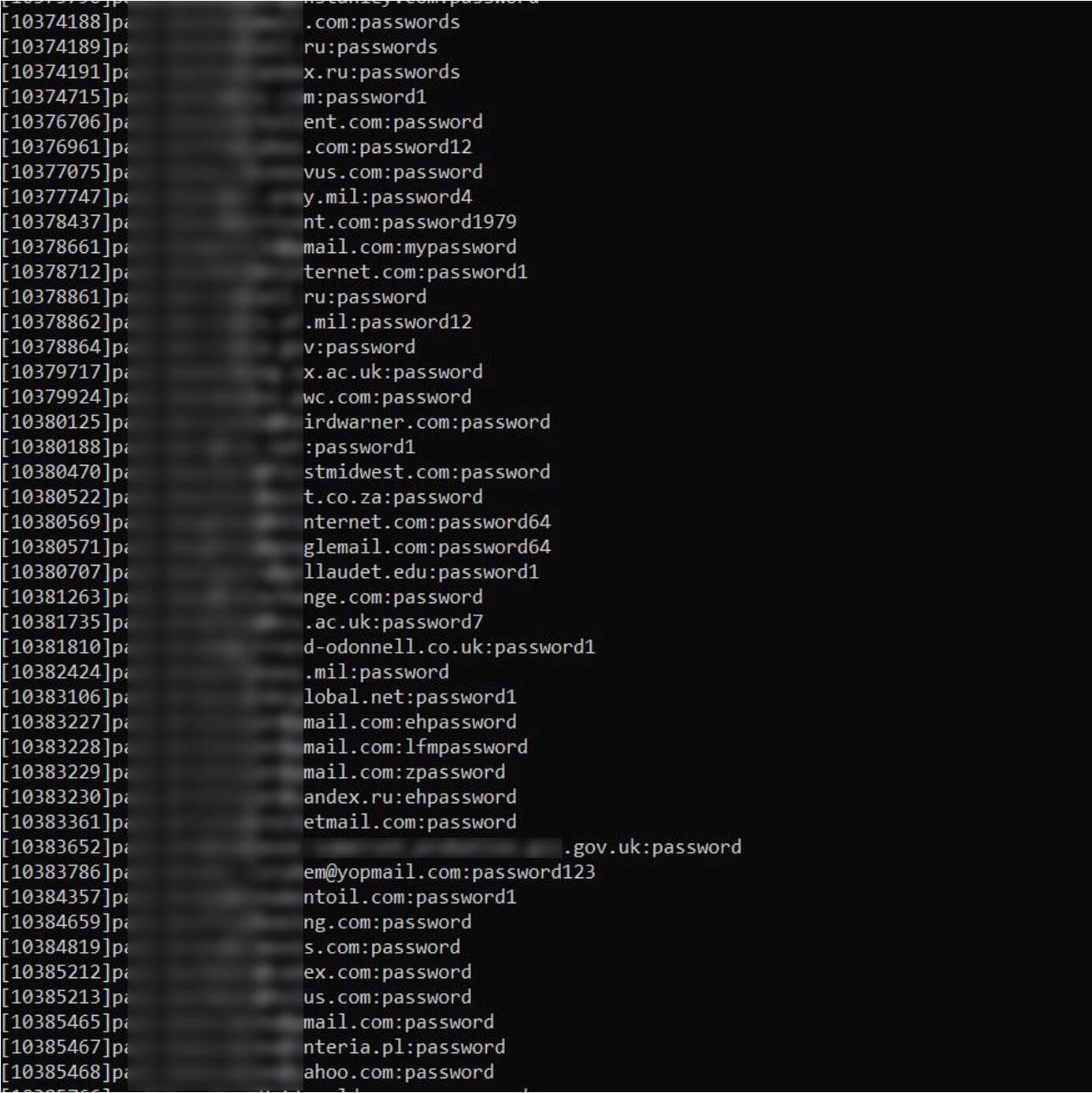
How does my information find yourself on the darkish net?
There are numerous methods your individual information may find yourself in a darkish net discussion board or website. Some could also be the results of negligence whereas many others usually are not. Take into account the next:
- Information breaches at third-party organizations: Your information is stolen from a corporation you have got completed enterprise with, and which has collected your information, previously. Within the US, 2023 was a document 12 months for information compromises of this kind: Greater than 3,200 incidents at organizations led to the compromise of knowledge belonging to over 353 million prospects.
- Phishing assaults: One among your on-line accounts (e.g., electronic mail, financial institution, social media) is compromised by way of a phishing assault. A legitimate-looking electronic mail, direct message, textual content or WhatsApp incorporates a hyperlink which can set up info-stealing malware or trick you into coming into your private and/or log-in particulars (i.e., a spoofed login web page for Microsoft 365).
- Credential stuffing: An internet account is compromised by way of a brute-force assault. (credential stuffing, dictionary assault, and so forth.) the place hackers guess your password or use beforehand breached logins throughout different websites. As soon as inside your account, they steal extra private info saved in there to promote or use.
- Data-stealing malware: Your private information is stolen by way of information-stealing malware that could possibly be hidden in legitimate-looking apps and information for obtain (comparable to pirated motion pictures/video games), phishing attachments, malicious advertisements, web sites and so forth.
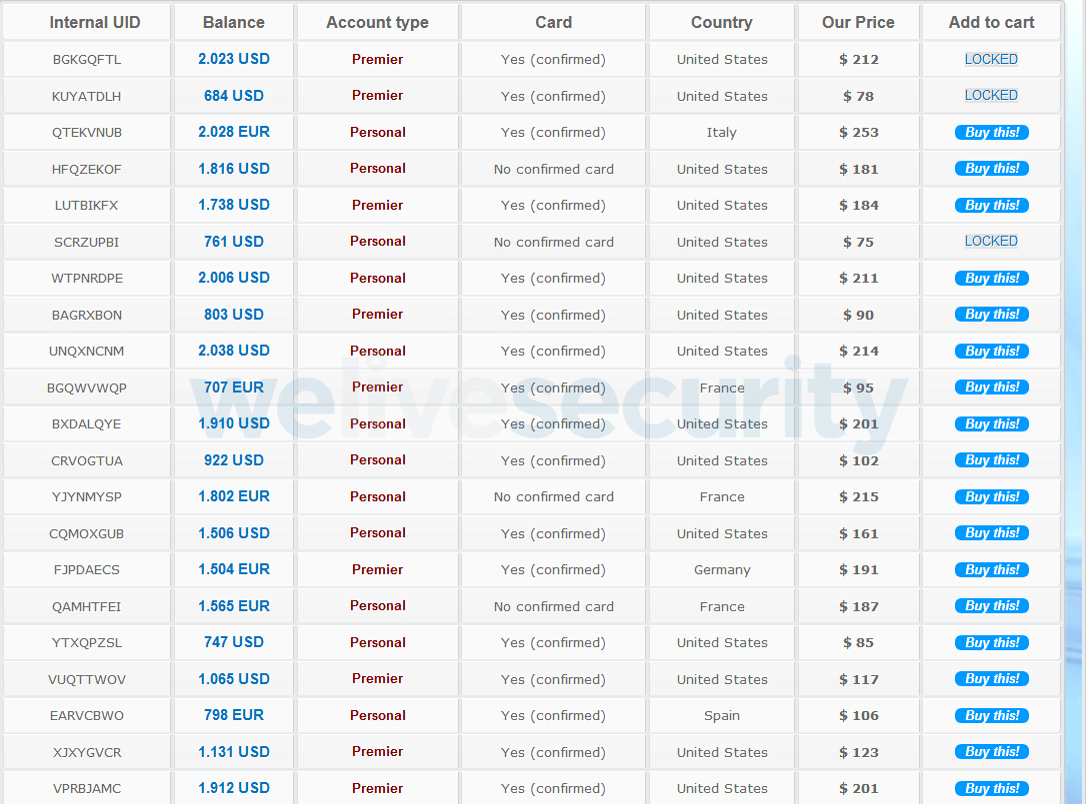
 Nonetheless the dangerous guys pay money for your information, as soon as it’s shared on a darkish net cybercrime website it may then be given away or offered to the very best bidder. Relying on the kind of information, whomever will get maintain of it can seemingly use these logins and PII to:
Nonetheless the dangerous guys pay money for your information, as soon as it’s shared on a darkish net cybercrime website it may then be given away or offered to the very best bidder. Relying on the kind of information, whomever will get maintain of it can seemingly use these logins and PII to:
- Hijack your financial institution accounts to steal extra info together with financial institution/card particulars.
- Design extra convincing phishing messages which share a number of the stolen PII in a bid to steer you handy over extra.
- Steal your electronic mail or social media accounts to spam pals and tackle ebook contacts with malicious hyperlinks.
- Commit identification fraud; e.g., taking out new traces of credit score in your identify, producing false tax returns with a purpose to obtain a refund, or illegally receiving medical providers.
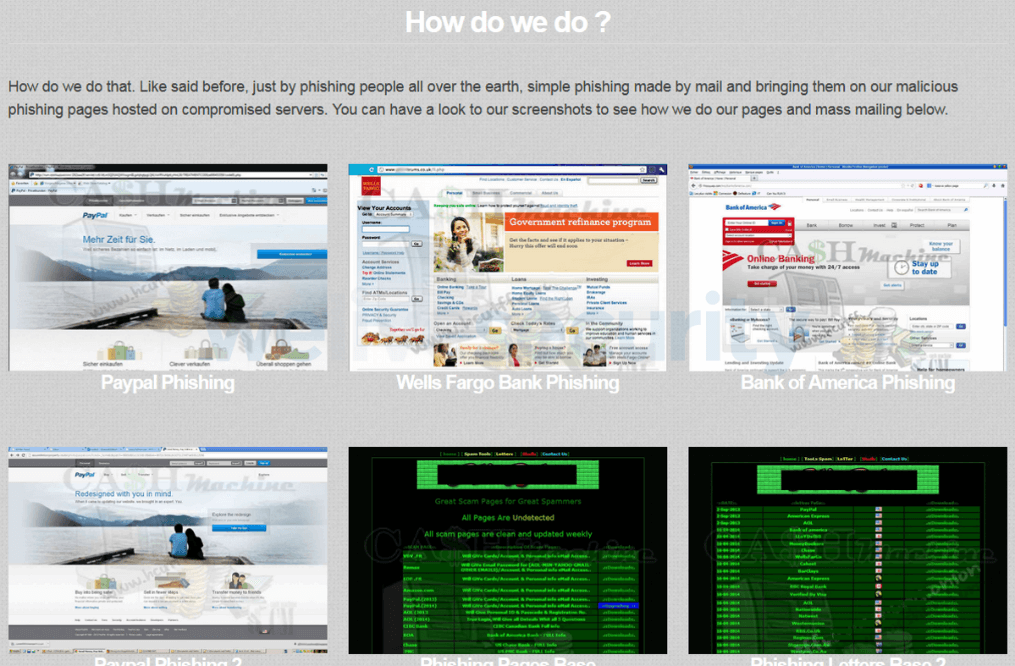
How do I verify?
When you’re signed as much as an identification safety or darkish net monitoring service, it ought to flag any PII or different information it finds on the darkish net. Tech firms, together with Google and Mozilla, may even warn you when a saved password has been present in an information breach, or might require updating to a safer, harder-to-guess model.
Importantly, darkish net monitoring is commonly additionally a part of a spread of providers offered by safety distributors, whose merchandise clearly include many different advantages and are a essential part of your private safety stack.
Alternatively, you may proactively go to a website like HaveIBeenPwned, which has compiled massive lists of breached electronic mail addresses and passwords that may be securely queried.
What do I do if my information has been stolen?
If the worst occurs and, like a British politician, you discover your information has been uncovered and is being traded on the darkish net, what occurs subsequent? Within the brief time period, think about taking emergency steps comparable to:
- Change all of your passwords, particularly the affected ones, to sturdy, distinctive credentials
- Use a password supervisor to retailer and recall your saved passwords and passphrases
- Change on two-factor authentication (2FA) on all accounts that provide it
- Notify the related authorities (legislation enforcement, social media platform, and so forth.)
- Guarantee your whole computer systems and gadgets have safety software program put in from a good vendor.
- Freeze your financial institution accounts (if related) and ask for brand spanking new playing cards. Monitor them for any uncommon purchases.
- Look out for different uncommon exercise on accounts comparable to being unable to login, modifications to safety settings, messages/updates from accounts you don’t acknowledge or logins from unusual places and unusual instances.
Staying protected within the long-term
To keep away from being hit sooner or later, think about:
- Being extra cautious of oversharing info on-line.
- Revisiting the safety/privateness settings of your social media accounts.
- Turning on ‘stealth mode’; i.e., when acceptable, use choices comparable to disposable electronic mail addresses so that you don’t all the time have to offer away your private particulars.
- By no means replying to unsolicited emails, messages or calls – particularly those who attempt to hurry you into taking motion with out pondering clearly first.
- Use sturdy and distinctive passwords on all accounts that provide it and allow a robust type of 2FA for added safety.
- Investing in a darkish net monitoring service that can warn you to newly-found private particulars within the web’s seedy underbelly and doubtlessly allow you to take motion earlier than cybercriminals can monetize the info.
It’s not a lot enjoyable having your private info and/or identification stolen. It may be a traumatic, nerve-racking expertise which can final weeks or months earlier than a decision. See what’s lurking on the market on the darkish net proper now and it could by no means get to that stage.


