
Mishaal Rahman / Android Authority
TL;DR
- Android 15 blocks untrusted apps from studying delicate notifications, even when they’ve permission to learn all notifications.
- Earlier than Android 15, apps with notification entry have been capable of learn all incoming notifications, even ones with OTP codes.
- Now, although, solely sure trusted apps can learn OTP codes from notifications.
Your telephone’s notifications panel is a treasure trove of delicate information, because it contains not simply private messages but additionally safety codes despatched from on-line companies you’ve enabled two-factor authentication for. That’s why many malicious apps attempt to trick you into granting them notification entry to allow them to steal these two-factor authentication codes. Fortunately, the Android 15 replace makes it tougher for malicious apps to extract two-factor authentication codes from notifications.
Android has lengthy provided an API known as Notification Listener that lets third-party apps entry your notifications. Since notifications can comprise delicate information, apps can’t use the Notification Listener API except they get your permission. You need to manually grant the app entry to your notifications by the Settings app, and the one factor apps can do to help with that course of is to open the Settings web page the place you’ll be able to grant entry.
Mishaal Rahman / Android Authority
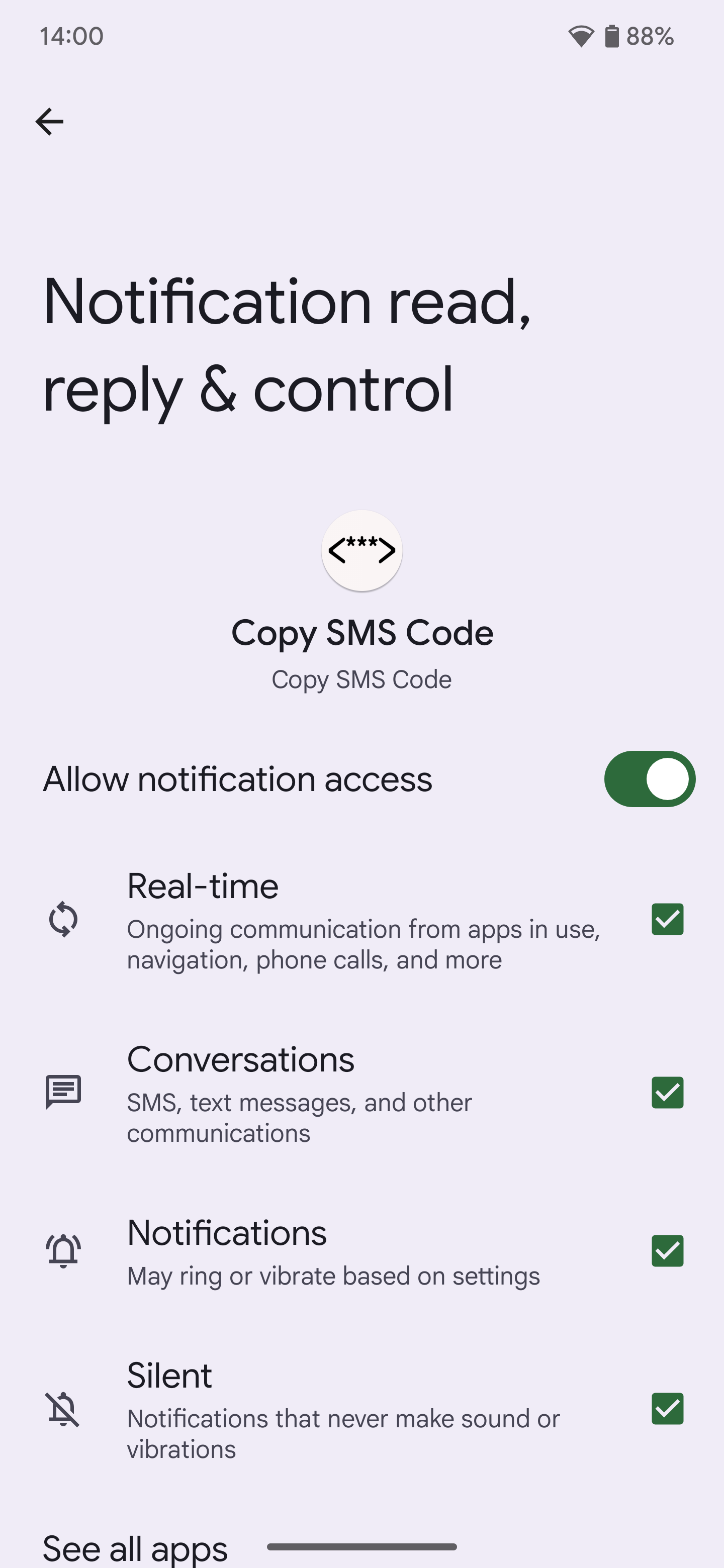
As soon as an app has been granted notification entry, it could actually learn, reply to, dismiss, or management both all your telephone’s notifications or the subset of notifications that you simply gave it entry to. It doesn’t matter if that notification contains one thing actually delicate like a two-factor authentication code — with the Notification Listener API, apps can learn them and thus extract them.
Android 15 adjustments issues by designating notifications with two-factor authentication codes as “delicate” and solely permitting “trusted” Notification Listener companies to learn them. Any “untrusted” Notification Listener service that tries to learn notifications with two-factor authentication codes will merely be given a message stating, “delicate notification content material hidden.”
Right here’s a brief video demonstrating how this modification impacts Notification Listeners on Android 14 versus Android 15. On this video, you’ll be able to see that an app that I’ve granted notification entry to on a tool operating Android 14 can learn notifications with two-factor authentication codes in them. In distinction, the identical app with the identical permission on a tool operating Android 15 can’t learn notifications with two-factor authentication codes in them.
Underneath the hood, the Android System Intelligence (ASI) app processes all notifications earlier than they’re despatched to Notification Listener companies. If ASI detects {that a} notification has a two-factor authentication code in it, it’ll inform the system to mark it “delicate” and block it from being despatched to “untrusted” Notification Listener companies. “Untrusted” Notification Listener companies belong to apps that don’t maintain the brand new RECEIVE_SENSITIVE_NOTIFICATIONS permission that Google has added in Android 15.
This permission can solely be granted to apps signed with the system certificates or to apps that maintain sure roles. Many of the roles which might be granted the RECEIVE_SENSITIVE_NOTIFICATIONS permission can solely be held by system apps, however there are some that may be held by third-party apps, too, like COMPANION_DEVICE_WATCH, COMPANION_DEVICE_GLASSES, and HOME. Respectively, these roles are given to look at companion apps, sensible glasses companion apps, and the default launcher. In different phrases, the one third-party apps that may learn notifications with two-factor authentication codes in them on Android 15 are apps that connect with your smartwatch, apps that connect with your sensible glasses, or your default residence display launcher app.
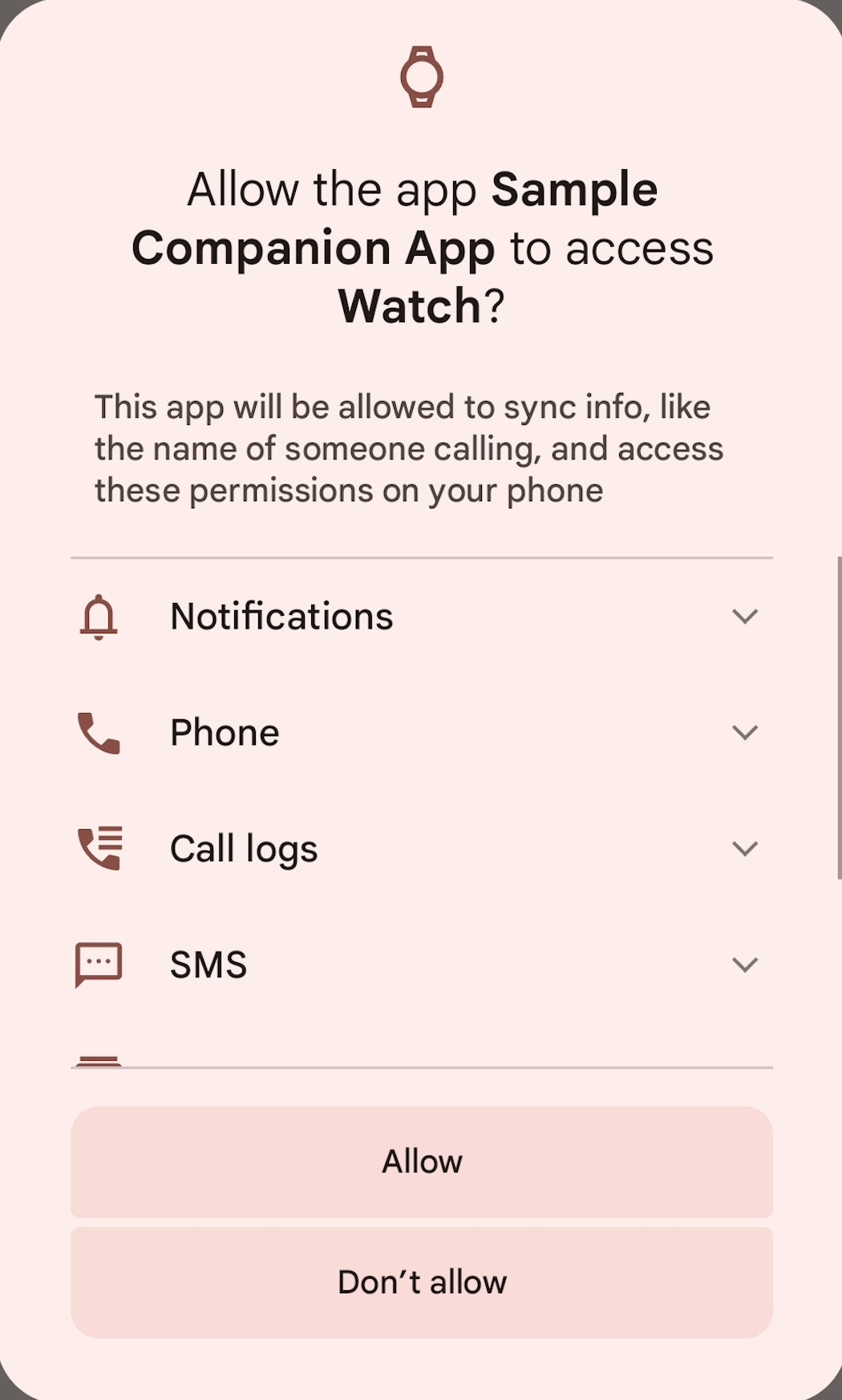
Pattern dialog for an app requesting to carry the COMPANION_DEVICE_WATCH function.
Blocking third-party apps from studying notifications with two-factor authentication codes in them will hopefully cease some hacking makes an attempt, but it surely’ll additionally break some automation and comfort instruments equivalent to “Copy SMS Code,” the free and open supply app I used to reveal these adjustments. There’s a simple workaround to revive the previous conduct, but it surely’s not one thing I like to recommend. It includes turning off “Enhanced notifications” below Settings > Notifications. This stops ASI from parsing notifications and marking ones with two-factor authentication codes as “delicate,” but it surely additionally stops it from producing prompt actions or replies. One other workaround requires establishing and utilizing ADB to manually grant the RECEIVE_SENSITIVE_NOTIFICATIONS permission utilizing the next command:
Code
adb shell cmd appops set --user 0 <PACKAGE> RECEIVE_SENSITIVE_NOTIFICATIONS enableRight here, <PACKAGE> is the bundle title for the applying you need to grant the permission to. You need to solely do that for those who’re an influence consumer and there’s some software this modification in any other case breaks, although.
It’s nice to see Android make tiny tweaks like this that enhance safety, however it could be good if Google documented this modification someplace, particularly as a result of it impacts app conduct. It might even be good if Android selectively blocked delicate notifications from showing on the lock display, which is one thing Google was testing once I first reported on this modification again in February — possibly that one will arrive in a future Android replace.

