At Sophos, your safety is our high precedence. We now have invested in making Sophos Firewall essentially the most safe firewall in the marketplace – and we repeatedly work to make it essentially the most troublesome goal for hackers.
To boost your safety posture, we strongly encourage you to repeatedly overview and implement these finest practices throughout all of your community infrastructure, whether or not from Sophos or some other vendor.
Learn on for full directions or obtain the Sophos Firewall hardening finest practices.
Hold firmware updated
Each Sophos Firewall OS replace consists of vital safety enhancements – together with our newest launch, Sophos Firewall v21.
Make sure you maintain your firmware updated below Backup & Firmware > Firmware. Test no less than as soon as a month for firmware updates in Sophos Central or the on-box console. You may simply schedule updates in Sophos Central to be utilized throughout a interval of minimal disruption.
On-line guides:
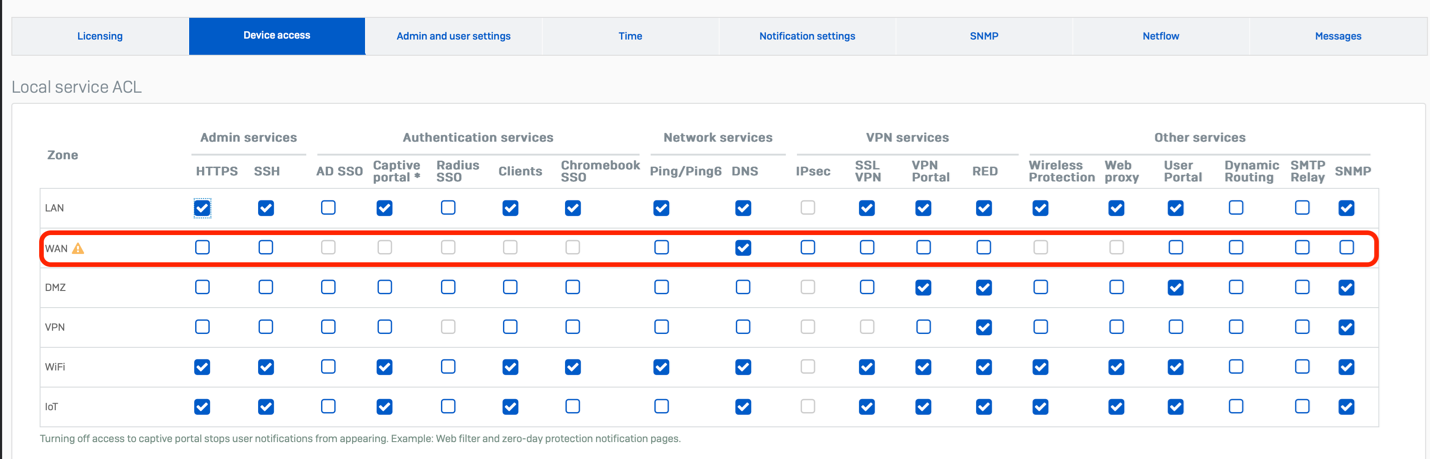
Restrict machine service entry
It’s critically vital that you simply disable non-essential providers on the WAN interface. Specifically, HTTPS and SSH admin providers.
To handle your firewall remotely, Sophos Central affords a way more safe resolution than enabling WAN admin entry. Alternatively, use ZTNA for distant administration of your community units.
Test your native providers entry management below Administration > Gadget Entry and guarantee no objects are checked for the WAN Zone except completely needed:
On-line guides:
Use sturdy passwords, multi-factor authentication, and role-based entry
Allow multi-factor authentication or one-time password (OTP) and implement sturdy passwords, which can shield your firewall from unauthorized entry – both from stolen credentials or brute pressure hacking makes an attempt.
Guarantee your sign-in safety settings are set to dam repeated unsuccessful makes an attempt and implement sturdy passwords and CAPTCHA. Additionally use role-based entry controls to restrict publicity.
On-line guides:
Decrease entry to inside methods
Any machine uncovered to the WAN by way of a NAT rule is a possible danger. Ideally, no machine needs to be uncovered to the web by way of NAT or inbound connections, together with IoT units.
Audit and overview all of your NAT and firewall guidelines repeatedly to make sure there aren’t any WAN to LAN or distant entry enabled. Use ZTNA (and even VPN) for distant administration and entry to inside methods – DO NOT expose these methods, particularly Distant Desktop entry to the Web.
For IoT units, shut down any units that don’t provide a cloud proxy service and require direct entry by way of NAT – these units are ideally suited targets for attackers.
On-line guides:
Allow applicable safety
Defend your community from exploits by making use of TLS and IPS inspection to incoming untrusted visitors by way of related firewall guidelines. Tune your TLS and IPS inspection and make the most of trusted software FastPath offloading to get the perfect safety and efficiency on your explicit surroundings. Make sure you don’t have any broad firewall guidelines that enable ANY to ANY connections.
Additionally shield your community from each DoS and DDoS assaults by setting and enabling safety below Intrusion Prevention > DoS & spoof safety. Allow spoof prevention and apply flags for all DoS assault varieties.
Block visitors from areas you don’t do enterprise with by organising a firewall rule to dam visitors originating from undesirable nations or areas.
Guarantee Sophos X-Ops menace feeds are enabled to log and drop below Energetic Risk Safety.
On-line guides:
Allow alerts and notifications
Sophos Firewall will be configured to alert directors of system-generated occasions. Directors ought to overview the record of occasions and verify that system and safety occasions are monitored to make sure that points and occasions will be acted upon promptly.
Notifications are despatched by way of both an electronic mail and/or to SNMP traps. To configure Notifications, navigate to Configure > System providers and choose the Notifications record tab.
On-line guides:
Extra data
Be sure you try how Sophos Firewall is Safe By Design and seek the advice of the intensive on-line documentation and how-to movies to benefit from your Sophos Firewall.

