New analysis by cybersecurity agency Mandiant supplies eyebrow-raising statistics on the exploitation of vulnerabilities by attackers, primarily based on an evaluation of 138 completely different exploited vulnerabilities that have been disclosed in 2023.
The findings, printed on Google Cloud’s weblog, reveals that distributors are more and more being focused by attackers, who’re regularly lowering the common time to take advantage of each zero-day and N-day vulnerabilities. Nonetheless, not all vulnerabilities are of equal worth to attackers, as their significance will depend on the attacker’s particular goals.
Time-to-exploit is falling considerably
Time-to-exploit is a metric that defines the common time taken to take advantage of a vulnerability earlier than or after a patch is launched. Mandiant’s analysis signifies:
- From 2018 to 2019, the TTE sat at 63 days.
- From 2020 to 2021, it fell to 44 days.
- From 2021 to 2022, the TTE dropped even additional to 32 days.
- In 2023, the TTE sat at simply 5 days.
SEE: How one can Create an Efficient Cybersecurity Consciousness Program (TechRepublic Premium)
Zero-day vs N-day
As TTE continues to shrink, attackers are more and more benefiting from each zero-day and N-day vulnerabilities.
A zero-day vulnerability is an exploit that hasn’t been patched, usually unknown to the seller or the general public. An N-day vulnerability is a recognized flaw first exploited after patches can be found. It’s subsequently potential for an attacker to take advantage of a N-day vulnerability so long as it has not been patched on the focused system.
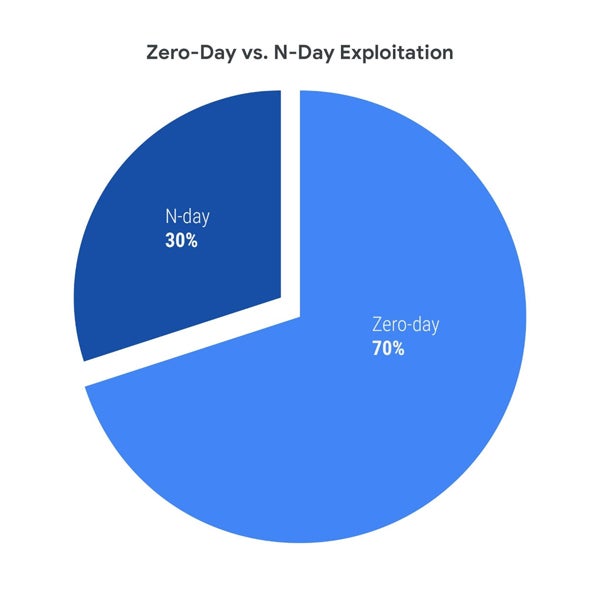
Mandiant exposes a ratio of 30:70 of N-day to zero-days in 2023, whereas the ratio was 38:62 throughout 2021-2022. Mandiant researchers Casey Charrier and Robert Weiner report that this variation is probably going as a result of elevated zero-day exploit utilization and detection fairly than a drop in N-day exploit utilization. It is usually potential that menace actors had extra profitable makes an attempt to take advantage of zero-days in 2023.
“Whereas we’ve got beforehand seen and proceed to count on a rising use of zero-days over time, 2023 noticed a fair bigger discrepancy develop between zero-day and n-day exploitation as zero-day exploitation outpaced n-day exploitation extra closely than we’ve got beforehand noticed,” the researchers wrote.
N-day vulnerabilities are principally exploited within the first month after the patch
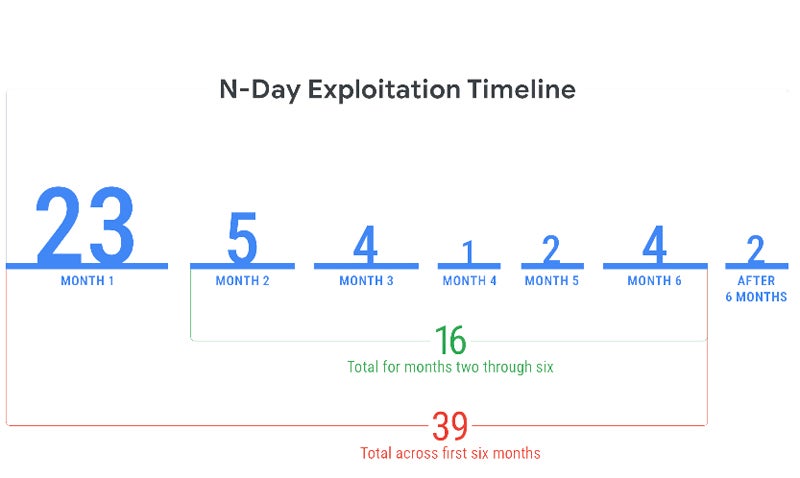
Mandiant stories that they noticed 23 N-day vulnerabilities being exploited within the first month following the discharge of their fixes, but 5% of them have been exploited inside in the future, 29% inside one week, and greater than half (56%) inside a month. In complete, 39 N-day vulnerabilities have been exploited in the course of the first six months of the discharge of their fixes.
Extra distributors focused
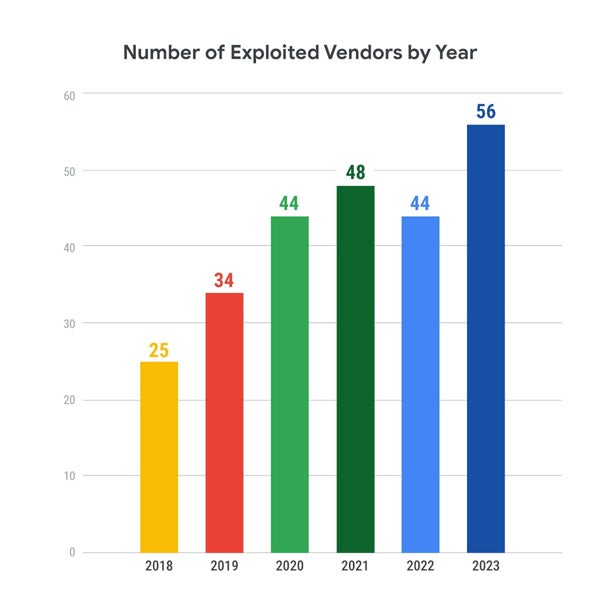
Attackers appear so as to add extra distributors to their goal record, which elevated from 25 distributors in 2018 to 56 in 2023. This makes it more difficult for defenders, who attempt to defend an even bigger assault floor yearly.
Circumstances research define the severity of exploitations
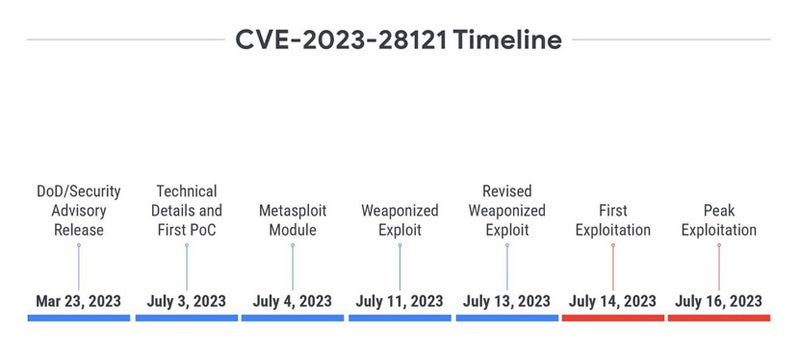
Mandiant exposes the case of the CVE-2023-28121 vulnerability within the WooCommerce Funds plugin for WordPress.
Disclosed on March 23, 2023, it didn’t obtain any proof of idea or technical particulars till greater than three months later, when a publication confirmed the best way to exploit it to create an administrator person with out prior authentication. A day later, a Metasploit module was launched.
A number of days later, one other weaponized exploit was launched. The primary exploitation started in the future after the revised weaponized exploit had been launched, with a peak of exploitation two days later, reaching 1.3 million assaults on a single day. This case highlights “an elevated motivation for a menace actor to take advantage of this vulnerability because of a purposeful, large-scale, and dependable exploit being made publicly accessible,” as acknowledged by Charrier and Weiner.
The case of CVE-2023-27997 is completely different. The vulnerability, referred to as XORtigate, impacts the Safe Sockets Layer (SSL) / Digital Non-public Community (VPN) element of Fortinet FortiOS. The vulnerability was disclosed on June 11, 2023, instantly buzzing within the media even earlier than Fortinet launched their official safety advisory, in the future later.
On the second day after the disclosure, two weblog posts have been printed containing PoCs, and one non-weaponized exploit was printed on GitHub earlier than being deleted. Whereas curiosity appeared obvious, the primary exploitation arrived solely 4 months after the disclosure.
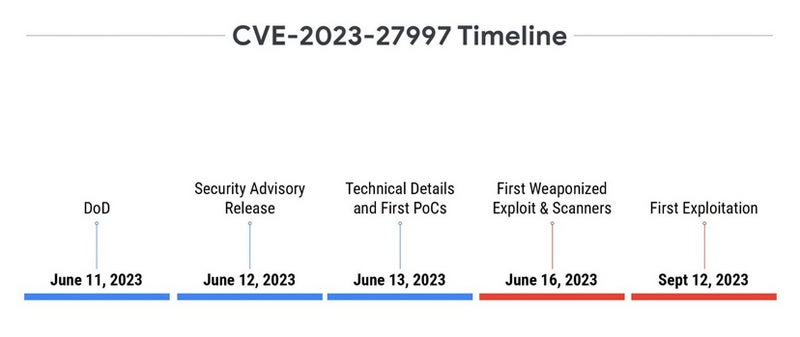
One of the crucial probably explanations for the variation in noticed timelines is the distinction in reliability and ease of exploitation between the 2 vulnerabilities. The one affecting WooCommerce Funds plugin for WordPress is simple to take advantage of, because it merely wants a particular HTTP header. The second is a heap-based buffer overflow vulnerability, which is way tougher to take advantage of. That is very true on programs which have a number of commonplace and non-standard protections, making it troublesome to set off a dependable exploitation.
A driving consideration, as uncovered by Mandiant, additionally resides within the meant utilization of the exploit.
“Directing extra power towards exploit growth of the tougher, but ‘extra invaluable’ vulnerability could be logical if it higher aligns with their goals, whereas the easier-to-exploit and ‘much less invaluable’ vulnerability might current extra worth to extra opportunistic adversaries,” the researchers wrote.
Deploying patches is not any easy activity
Greater than ever, it’s necessary to deploy patches as quickly as potential to repair vulnerabilities, relying on the danger related to the vulnerability.
Fred Raynal, chief govt officer of Quarkslab, a French offensive and defensive safety firm, advised TechRepublic that “Patching 2-3 programs is one factor. Patching 10,000 programs is just not the identical. It takes group, folks, time administration. So even when the patch is offered, a couple of days are often wanted to push a patch.”
Raynal added that some programs take longer to patch. He took the instance of cell phone vulnerability patching: “When there’s a repair in Android supply code, then Google has to use it. Then SoC makers (Qualcomm, Mediatek and so on.) need to strive it and apply it to their very own model. Then Cellphone makers (eg Samsung, Xiaomi) need to port it to their very own model. Then carriers typically customise the firmware earlier than constructing it, which can’t at all times use the most recent variations of the supply. So, right here, the propagation of a patch is … lengthy. It isn’t unusual to search out 6 month previous vulnerabilities in at present’s telephone.”
Raynal additionally insists that availability is a key consider deploying patches: “Some programs can afford to fail! Think about an oil platform or any power maker: patching okay, however what if the patch creates a failure. No extra power. So what’s the worst? An unpatch essential system or a metropolis with out power? An unpatch essential system, it’s a few potential menace. A metropolis with out power, it’s about precise points.”
Lastly, some programs will not be patched in any respect, in response to Raynal: “In some areas, patches are forbidden. As an example, many firms constructing healthcare gadgets forestall their customers from making use of patches. In the event that they do, it breaks the guarantee.”

