9to5Mac Safety Chew is completely delivered to you by Mosyle, the one Apple Unified Platform. Making Apple gadgets work-ready and enterprise-safe is all we do. Our distinctive built-in strategy to administration and safety combines state-of-the-art Apple-specific safety options for totally automated Hardening & Compliance, Subsequent Era EDR, AI-powered Zero Belief, and unique Privilege Administration with essentially the most highly effective and fashionable Apple MDM available on the market. The result’s a very automated Apple Unified Platform at the moment trusted by over 45,000 organizations to make hundreds of thousands of Apple gadgets work-ready with no effort and at an inexpensive price. Request your EXTENDED TRIAL in the present day and perceive why Mosyle is every little thing it is advisable work with Apple.
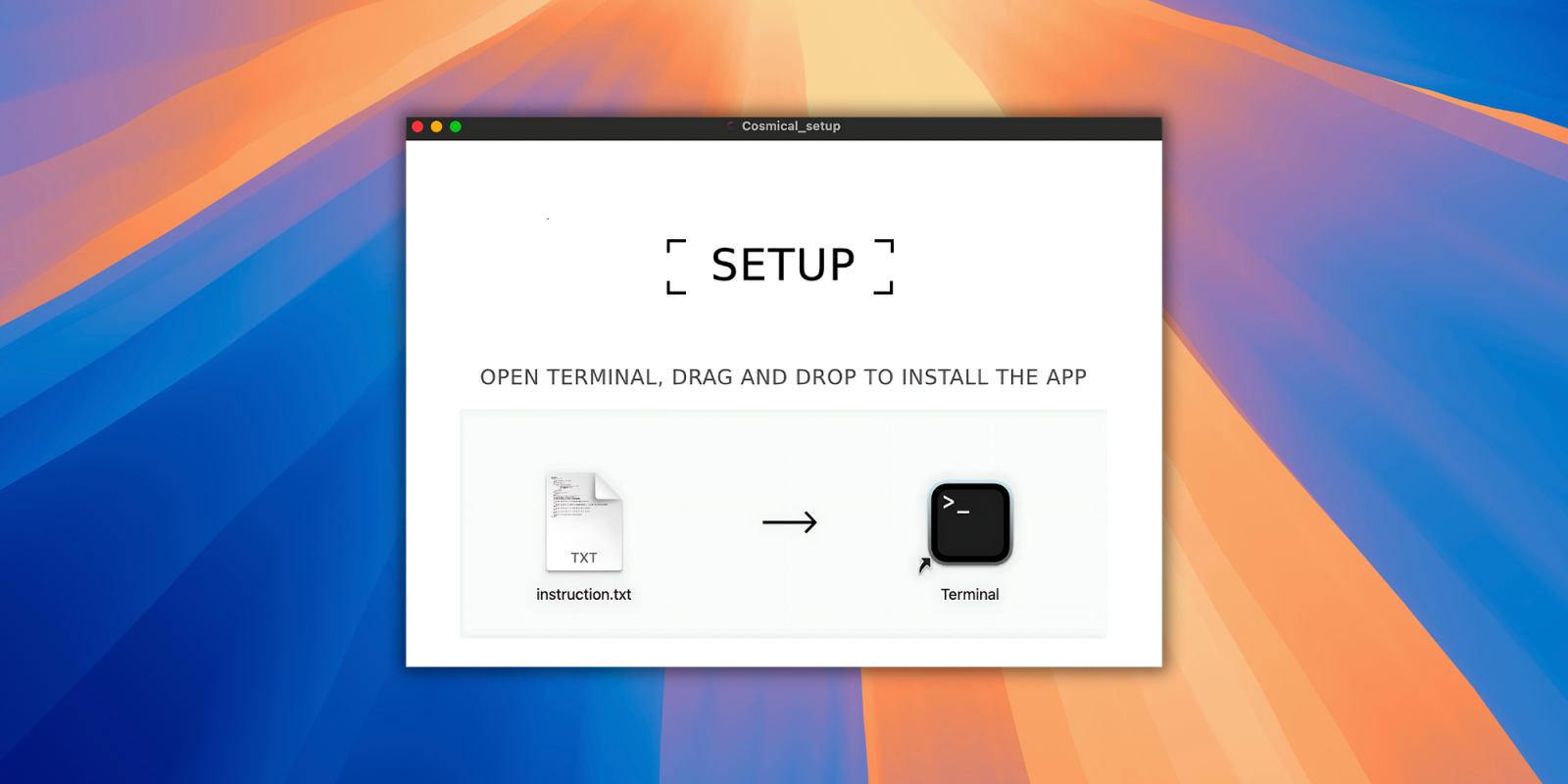
In presumably a primary for the reason that launch of macOS Sequoia, cybersecurity researchers have recognized a brand new assault vector that sidesteps the same old “right-click open” in favor of one thing fairly uncommon. In a latest discovering shared on social media, this new methodology includes tricking customers into dragging and dropping malicious code (through a .txt file) immediately into the Terminal.

With the discharge of macOS Sequoia, Apple took a proactive step to assist hold Joe Shmoes from executing malware on their Macs. Customers on Sequoia can not control-click to override Gatekeeper and open software program that isn’t signed or notarized by Apple with out having to enter Settings, then Safety & Privateness, to “evaluate safety info” earlier than with the ability to run the software program. The extra steps try to tell the person of what they’re mounting to disk and, ideally, give them pause.
After all, this throws a wrench within the baddies’ (cybercriminals’) operations, which thrive on deceiving customers to right-click and hit “Open” to make use of no matter reputable utility they suppose they put in. I’m speculating that the extra customers who proceed to undertake Sequoia, the less executions happen on machines, and thus, the much less cash they make from draining crypto wallets on Macs and so forth.
Now, we’re seeing one of many first situations of cybercriminals evolving their techniques to bypass macOS Sequioa’s newest Gatekeeper change. This explicit pattern of the brand new infostealer goes beneath the title Cosmical_setup and is being tracked as Amos-affiliated.
Right here’s the way it works:
- The attacker delivers a disk picture file (DMG) to the sufferer.
- The sufferer is instructed to open the Terminal utility and, as a substitute of right-clicking to put in, they’re requested to tug and drop a “.txt” file immediately into the Terminal window.
- The seemingly innocent “.txt” file is, in actual fact, a malicious Bash script. As soon as dropped into the Terminal, it triggers the execution of osascript, which then runs AppleScript instructions.
This strategy is extra trivial for individuals like my grandparents to do over a easy right-click. We’ll have to attend and see if the baddies will keep on with this or if it’s only a one-off malware product take a look at. All-in-all I exploit my grandparents for scale on most issues malware, and this doesn’t go. Properly completed, Apple.
FTC: We use revenue incomes auto affiliate hyperlinks. Extra.

