North Korea-linked menace teams are more and more utilizing living-off-the-land (LotL) strategies and trusted providers to evade detection, with a latest Kimsuky marketing campaign showcasing the usage of PowerShell scripts and storing knowledge in Dropbox folders, together with improved operational safety.
Within the marketing campaign, dubbed “DEEP#DRIVE” by safety agency Securonix, the menace group used pretend work logs, insurance coverage paperwork, and crypto-related recordsdata to persuade customers to obtain and run a zipped shortcut file that gathers system configuration data after which executes PowerShell and .NET scripts. The assault instruments add the system knowledge to Dropbox folders after which obtain extra instructions and capabilities for additional compromise.
Whereas the attackers confirmed some curiosity in fast monetary wins — similar to focusing on cryptocurrency customers — for probably the most half, the menace group centered on stealing delicate knowledge from South Korean authorities companies and companies, says Tim Peck, a senior menace researcher at Securonix.
“We noticed proof of each espionage and monetary motivation, although leaning extra towards espionage,” he says. “This aligns with Kimsuky’s historic focusing on of South Korean authorities companies, enterprises, and strategic industries.”
North Korean cyber-operations teams have constantly focused South Korea and the US, with South Korean authorities companies and corporations among the many hottest targets. In September 2024, the FBI warned that North Korean teams deliberate to launch a surge of assaults in opposition to organizations with important cryptocurrency reserves, and Kimsuky launched a related multistage assault in opposition to South Korean targets final yr.
A Prolific Group
Kimsuky is not monolithic, however has 5 menace teams which have overlap with what different firms take into account to be the identical group, says menace intelligence agency Recorded Future. One group tends to give attention to the healthcare and hospitality sectors, for instance, whereas one other focuses on cryptocurrency markets.
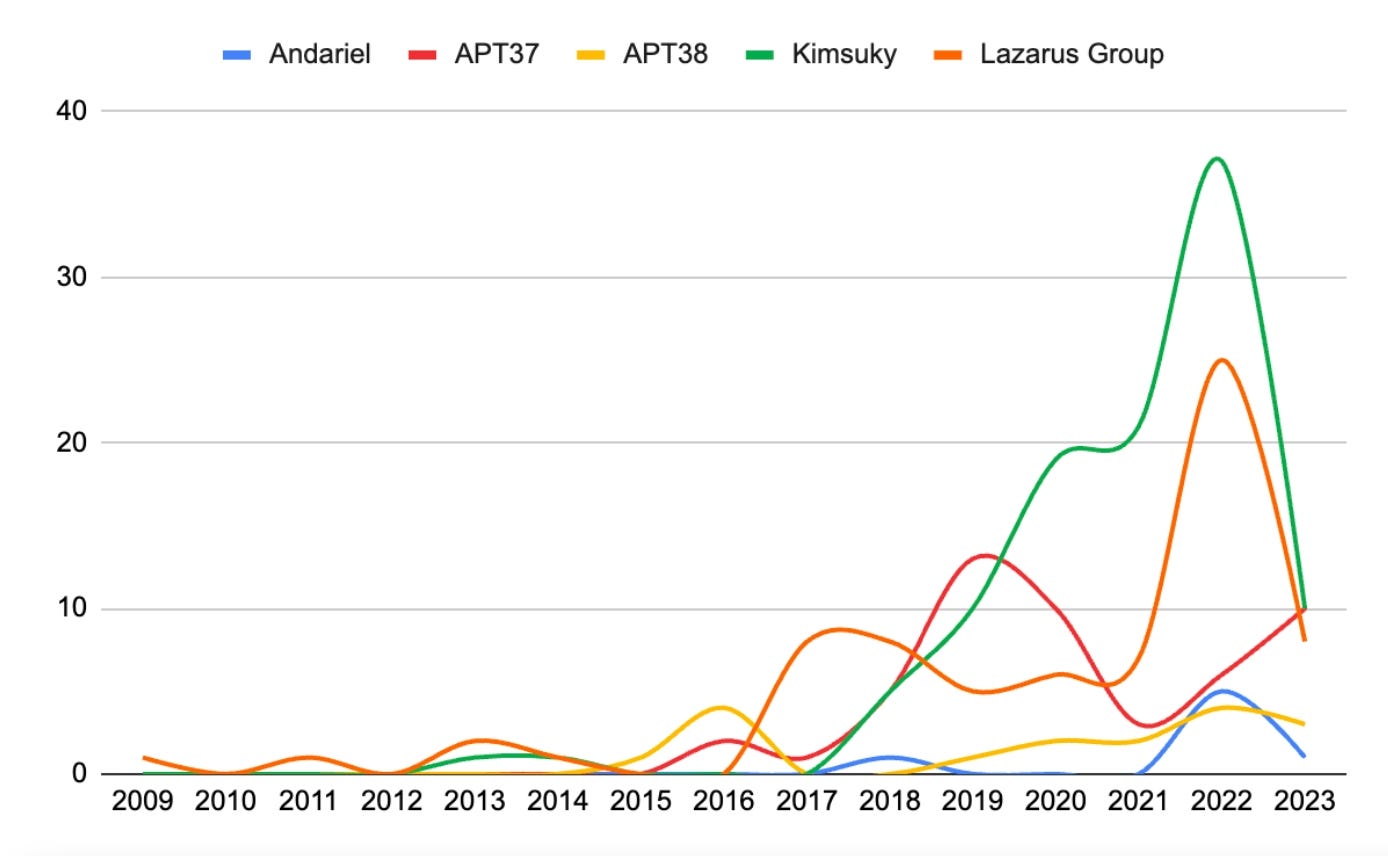
By mid-2023, Kimsuky turned probably the most prolific North Korean group. (More moderen knowledge not obtainable.) Supply: Recorded Future’s “North Korea’s Cyber Technique” report
The Kimsuky teams accounted for probably the most assaults recognized as North Korean in origin between 2021 and 2023, in line with Recorded Future’s “North Korea Cyber Technique” report. In 2024, the teams continued to account for a excessive quantity of assaults, says Mitch Haszard, senior menace intelligence analyst with Recorded Future.
“These teams conduct excessive quantity phishing campaigns, primarily focusing on people and organizations in South Korea, whereas often focusing on entities in different international locations,” he says. “Within the exercise we see, these teams look like going for quantity, slightly than extra time-consuming, tailor-made spear-phishing operations.”
Different well-known North Korean teams, similar to Lazarus and Andariel, will not be as prolific because the Kimsuky menace actors. Whereas a few of these teams are extra centered on gathering delicate data, practically all even have a monetary motivation.
Hundreds of Victims?
In the DEEP#DRIVE marketing campaign, following the compromise of a system, the Kimsuky group’s assault scripts add knowledge on the system configuration to one in every of a number of Dropbox folders. Whereas the Securonix researchers weren’t in a position to collect intelligence from all of the suspected Dropbox areas, they uncovered indicators of greater than 8,000 configuration recordsdata, though some look like duplicates, Peck says.
Whereas which means they probably got here from the identical sufferer organizations, the marketing campaign seems to be fairly profitable, he says.
“There have been two elements which contributed to the ‘uniqueness’ of the configuration file, the username, and IP deal with,” Peck says. “Some usernames had been related to dozens of comparable IP addresses, which may point out lateral motion by the attacker — [that is], infecting dozens of machines from the identical entity.”
The info from a compromised system contains the host IP deal with, the system uptime, particulars in regards to the OS kind and model, any put in safety software program, and an inventory of working processes.
Kimsuky Improves Its OpSec
The marketing campaign additionally highlighted North Korean cyber-operations teams’ enhancements to operational safety. The group used OAuth-based authentication on its Dropbox folders, stopping conventional URL-blocking or network-based defenses from following the hyperlinks. The menace actors additionally rapidly took down elements of their infrastructure quickly after the Securonix researchers started investigating, Securonix’s Peck says.
“This stage of operational consciousness will not be at all times current in phishing-driven malware campaigns,” he says.
For firms, the menace group’s ways underscore that the hidden file extensions must be disabled, shortcut recordsdata must be blocked from executing in person folders, and solely signed PowerShell scripts be allowed to execute. These three countermeasures make the attackers’ exercise a lot simpler to detect, Peck says.
As well as, firms in focused industries — similar to cryptocurrency exchanges and authorities companies — ought to bolster their electronic mail safety and repeatedly practice staff on easy methods to spot phishing threats, says Recorded Future’s Haszard.
“Most North Korean cyberattacks nonetheless begin with social engineering and a phish,” he says. “Firms ought to be sure that they’ve an electronic mail safety resolution in place and repeatedly practice staff on phishing threats, in addition to conduct simulated phishing exams.”

