A now-patched iOS vulnerability might let malicious apps silently steal your iCloud information with no alerts, and no consent.
The crew at Jamf Menace Labs has found an enormous safety problem in Apple’s Transparency, Consent, and Management (TCC) system. The flaw, tagged as CVE-2024-44131, can let apps entry your personal stuff like photographs and site particulars with out you even realizing.
Apple has already mounted the vulnerability in iOS 18 and macOS 15, however it’s a wake-up name about cellular safety and holding our information personal. The TCC system is meant to provide you with a warning when apps need to entry your personal information, like your photographs or location.
However this vulnerability takes benefit of weaknesses in Apple’s FileProvider and fileproviderd processes, letting unhealthy apps slip previous the checks. As soon as they exploit this, they will seize your information with out elevating any alarms or asking for permission.
Unauthorized entry to iCloud
Each macOS and iOS methods are affected, displaying that unhealthy actors at the moment are concentrating on vulnerabilities throughout completely different platforms, particularly with regards to providers like iCloud. Such vulnerabilities problem the assumption that cellular gadgets are safer than desktops.
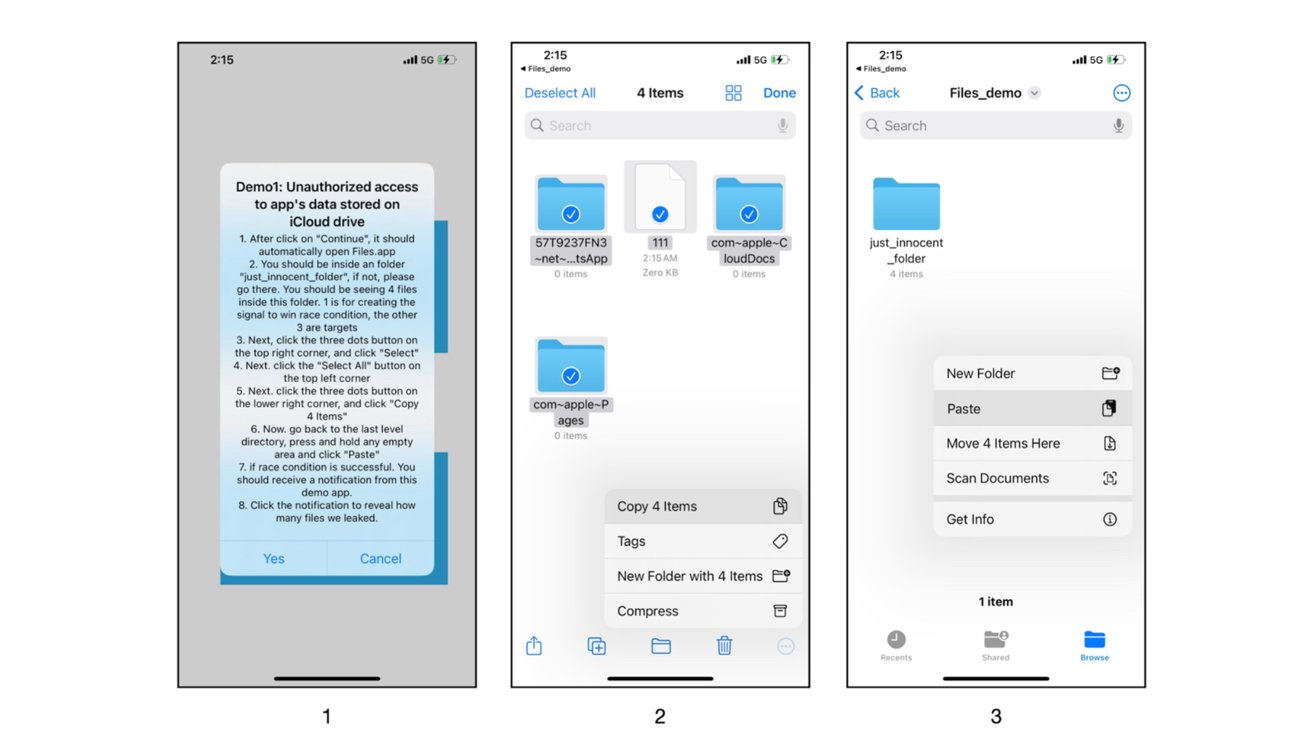
The exploit messes with symlink race circumstances in Apple’s Information.app and fileproviderd processes.
- Symlink Trickery: A shady app hijacks file operations by Information.app, rerouting them to directories it controls utilizing completely timed symlinks.
- Taking Benefit of Privileges: By abusing the fileproviderd’s elevated privileges, the rogue app can seize delicate consumer information with out triggering any TCC alerts.
For instance, Apple’s defenses can detect symlinks on the finish of file paths, however this trick drops symlinks within the center, sneaking previous detection.
The exploit targets particular listing paths that Information.app and fileproviderd can entry. This is what they’re after:
- iCloud Knowledge: Paths like /var/cellular/Library/Cellular Paperwork/ may very well be hit, together with backups for apps like WhatsApp, Apple’s Pages, and different iCloud-synced information.
- Widespread UUID Directories: Whereas many apps use distinctive UUIDs for safety, some shared directories (like /Cellular Paperwork/com~apple~CloudDocs/) are constant throughout gadgets, making them simpler to take advantage of.
The way to keep protected
Apple mounted the vulnerability in iOS 18 and macOS 15 after Jamf alerted the corporate. It is excellent news, however it reveals that no platform is protected from getting hacked.
First, make certain all of your gadgets are operating the newest iOS and macOS variations so you may have the newest safety patches. Companies and customers have to deal with cellular gadgets like they’re high-risk endpoints. Strengthening cellular safety is now not optionally available.
To maintain your iPhone protected, control who can entry it and look ahead to any unusual file exercise. This additional layer of safety will help you see any makes an attempt to interrupt in and forestall any information breaches.