Microsoft on Tuesday launched 71 patches touching 10 product households. Seventeen of the addressed points, all affecting Home windows, are thought of by Microsoft to be of Crucial severity and all have a CVSS base rating of 8.1 or greater. Ten of those contain Distant Desktop Companies. At patch time, one of many points addressed (CVE-2024-49138, an Necessary-severity Home windows Widespread Log File system driver difficulty) is thought to be underneath exploit within the wild, with 6 extra CVEs extra more likely to be exploited within the subsequent 30 days by the corporate’s estimation. 5 of this month’s points are amenable to detection by Sophos protections, and we embrace info on these in a desk beneath.
Along with these patches, the discharge consists of advisory info on two Edge CVEs (patched final week), a Protection-in-Depth replace for a particular model of Microsoft Venture, and data on six bulletins launched by Adobe this week. We’re as at all times together with on the finish of this submit extra appendices itemizing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product household.
Lastly, this month we’re including a brand new appendix that breaks out every month’s Home windows Server patches by affected model. Directors are inspired to make use of this appendix as a place to begin to establish their particular publicity, as every reader’s scenario — particularly because it issues merchandise out of mainstream help — will differ.
- Whole CVEs: 71
- Publicly disclosed: 1
- Exploit detected: 1
- Severity
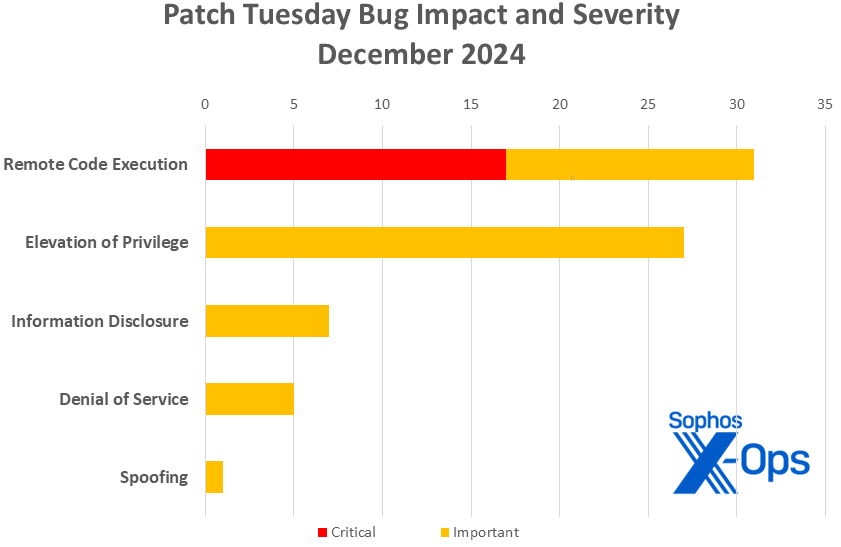
- Crucial: 17
- Necessary: 54
- Affect
- Distant Code Execution: 31
- Elevation of Privilege: 27
- Data Disclosure: 7
- Denial of Service: 5
- Spoofing: 1
- CVSS base rating 9.0 or better: 1
- CVSS rating 8.0 or better: 27
Determine 1: December’s CVEs embrace no spoofing, denial of service, or safety function bypass points, however there are many Crucial-severity RCEs to maintain system directors busy
Merchandise
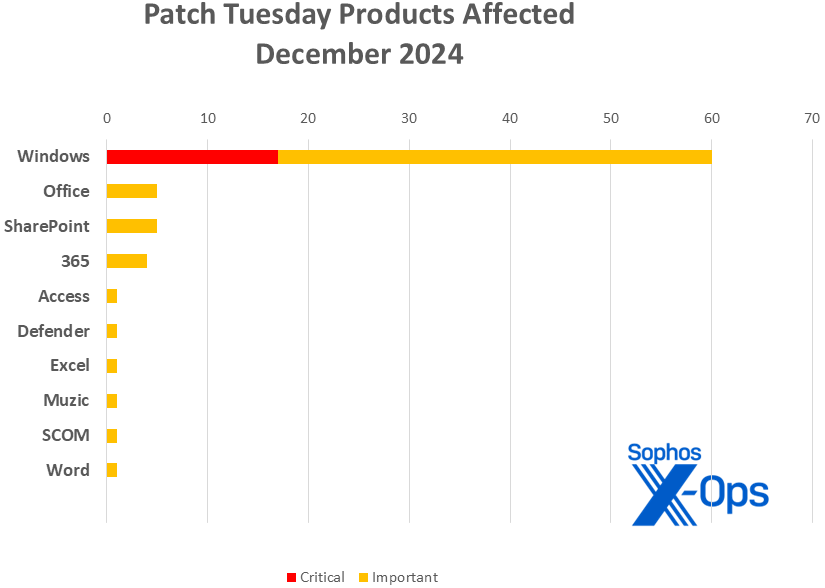
- Home windows: 59
- Workplace: 5
- SharePoint: 5
- 365 Apps: 4
- Entry: 1
- Defender: 1
- Excel: 1
- Muzic: 1
- SCOM: 1
- Phrase: 1
As is our customized for this checklist, CVEs that apply to multiple product household are counted as soon as for every household they have an effect on.
Determine 2: Six of the ten product households lined on this month’s updates have only one patch apiece. Muzic is a music-generation venture on Github (https://github.com/microsoft/muzic) initially developed by a group from Microsoft Analysis Asia
Notable December updates
Along with the problems mentioned above, plenty of particular gadgets advantage consideration.
CVE-2024-49112 — Home windows Light-weight Listing Entry Protocol (LDAP) Distant Code Execution Vulnerability
The one CVE this month with a CVSS base rating over 9.0, this Crucial-severity RCE weighs in at 9.8/10 and impacts not solely all supported variations of Home windows 10 and 11, however all variations of Server stretching again to 2008. Complexity is low (it requires a maliciously crafted set of LDAP calls), it requires neither privileges nor person interplay, and the attacker capable of efficiently exploit the bug positive aspects the flexibility to execute arbitrary code throughout the context of the LDAP service. For directors unable to prioritize this patch for no matter motive, Microsoft advises them to make sure that area controllers should not configured to entry the web, and that inbound RPC from untrusted networks is disallowed.
CVE-2024-49138 — Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability
The one December CVE that’s recognized to be underneath lively exploit within the wild, this Necessary-severity elevation of privilege difficulty likewise impacts all supported consumer and server variations of Home windows. A profitable attacker would acquire system privileges.
CVE-2024-49117 – Home windows Hyper-V Distant Code Execution Vulnerability
An attacker efficiently using this Crucial-severity RCE may doubtlessly execute a cross-VM assault, leaping out of the initially compromised machine to compromise others.
CVE-2024-49114 — Home windows Cloud Recordsdata Mini Filter Driver Elevation of Privilege Vulnerability
This Necessary-severity difficulty is an interesting instance of what simply is perhaps a brand new class of vulnerability: False File Immutability, wherein sure assumptions constructed into sure Home windows componentry may result in untrustworthy information, dangerous system behaviors, or different vulnerabilities. However, Microsoft categorizes this CVE as an Elevation of Privilege difficulty, another more likely to be exploited throughout the subsequent 30 days.
12 CVEs – RDP points
As lined in our Lively Adversary technical experiences, RDP continues to be the Microsoft part most frequently abused by attackers. Each client-side and server-side installations are in for it this month, with 10 of those CVEs classed as Crucial-severity by Microsoft.
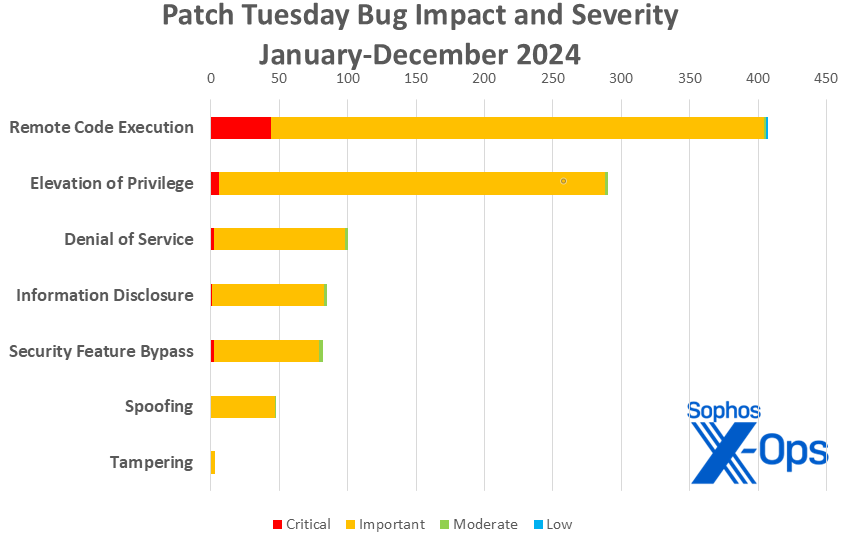
Determine 3: And as 2024 concludes, Distant Code Execution vulnerabilities retain their standing as the most typical bug species to be squashed, retaining the title seized from Elevation of Privilege on the finish of 2023
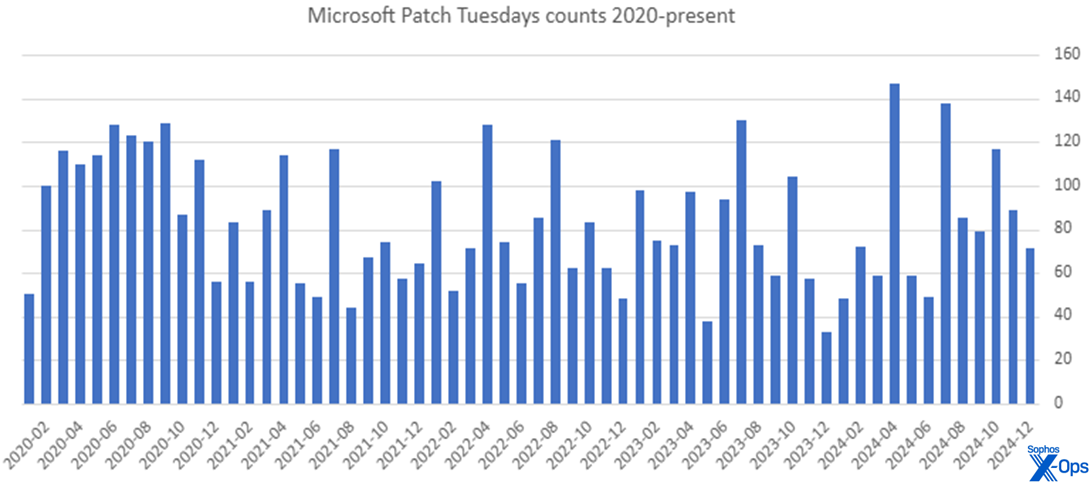
Although it began off with three comparatively mild months, 2024 ends with 1015 CVEs addressed by way of the Patch Tuesday course of – the very best annual rely since 2020’s complete of 1245 patches. 2024 additionally included the 2 single highest one-month patch counts, in April (147) and July (138). For these curious, December 2023 had the bottom rely of the previous 5 years, with 33 patches.
Determine 4: If it felt like 2020 was a loopy yr for Microsoft patches, you’re not unsuitable. Although 2024 had a number of banner months, 2020 was general the heaviest patch load in 4 years for many directors
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-49088 | Exp/2449088-A | Exp/2449088-A |
| CVE-2024-49090 | Exp/2449090-A | Exp/2449090-A |
| CVE-2024-49093 | Exp/2449093-A | Exp/2449093-A |
| CVE-2024-49122 | sid:2310400 | sid:2310400 |
| CVE-2024-49138 | Exp/2449138-A | Exp/2449138-A |
As you may each month, if you happen to don’t need to wait to your system to drag down Microsoft’s updates itself, you may obtain them manually from the Home windows Replace Catalog web site. Run the winver.exe software to find out which construct of Home windows 10 or 11 you’re operating, then obtain the Cumulative Replace package deal to your particular system’s structure and construct quantity.
Appendix A: Vulnerability Affect and Severity
This can be a checklist of December patches sorted by affect, then sub-sorted by severity. Every checklist is additional organized by CVE.
Distant Code Execution (31 CVEs)
| Crucial severity | |
| CVE-2024-49105 | Distant Desktop Shopper Distant Code Execution Vulnerability |
| CVE-2024-49106 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49108 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49112 | Home windows Light-weight Listing Entry Protocol (LDAP) Distant Code Execution Vulnerability |
| CVE-2024-49115 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49116 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49117 | Home windows Hyper-V Distant Code Execution Vulnerability |
| CVE-2024-49118 | Microsoft Message Queuing (MSMQ) Distant Code Execution Vulnerability |
| CVE-2024-49119 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49120 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49122 | Microsoft Message Queuing (MSMQ) Distant Code Execution Vulnerability |
| CVE-2024-49123 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49124 | Light-weight Listing Entry Protocol (LDAP) Shopper Distant Code Execution Vulnerability |
| CVE-2024-49126 | Home windows Native Safety Authority Subsystem Service (LSASS) Distant Code Execution Vulnerability |
| CVE-2024-49127 | Home windows Light-weight Listing Entry Protocol (LDAP) Distant Code Execution Vulnerability |
| CVE-2024-49128 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49132 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| Necessary severity | |
| CVE-2024-49063 | Microsoft/Muzic Distant Code Execution Vulnerability |
| CVE-2024-49065 | Microsoft Workplace Distant Code Execution Vulnerability |
| CVE-2024-49069 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49070 | Microsoft SharePoint Distant Code Execution Vulnerability |
| CVE-2024-49079 | Enter Technique Editor (IME) Distant Code Execution Vulnerability |
| CVE-2024-49080 | Home windows IP Routing Administration Snapin Distant Code Execution Vulnerability |
| CVE-2024-49085 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-49086 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-49089 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-49091 | Home windows Area Title Service Distant Code Execution Vulnerability |
| CVE-2024-49102 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-49104 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-49125 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-49142 | Microsoft Entry Distant Code Execution Vulnerability |
| CVE-2024-49063 | Microsoft/Muzic Distant Code Execution Vulnerability |
| CVE-2024-49065 | Microsoft Workplace Distant Code Execution Vulnerability |
| CVE-2024-49069 | Microsoft Excel Distant Code Execution Vulnerability |
Elevation of Privilege (27 CVEs)
| Necessary severity | |
| CVE-2024-43594 | System Heart Operations Supervisor Elevation of Privilege Vulnerability |
| CVE-2024-43600 | Microsoft Workplace Elevation of Privilege Vulnerability |
| CVE-2024-49059 | Microsoft Workplace Elevation of Privilege Vulnerability |
| CVE-2024-49068 | Microsoft SharePoint Elevation of Privilege Vulnerability |
| CVE-2024-49072 | Home windows Job Scheduler Elevation of Privilege Vulnerability |
| CVE-2024-49073 | Home windows Cell Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49074 | Home windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-49076 | Home windows Virtualization-Based mostly Safety (VBS) Enclave Elevation of Privilege Vulnerability |
| CVE-2024-49077 | Home windows Cell Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49078 | Home windows Cell Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49081 | Wi-fi Huge Space Community Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49083 | Home windows Cell Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49084 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-49088 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-49090 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-49092 | Home windows Cell Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49093 | Home windows Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2024-49094 | Wi-fi Huge Space Community Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49095 | Home windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability |
| CVE-2024-49097 | Home windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability |
| CVE-2024-49101 | Wi-fi Huge Space Community Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49107 | WmsRepair Service Elevation of Privilege Vulnerability |
| CVE-2024-49109 | Wi-fi Huge Space Community Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49110 | Home windows Cell Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49111 | Wi-fi Huge Space Community Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49114 | Home windows Cloud Recordsdata Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-49138 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
Data Disclosure (7 CVEs)
| Necessary severity | |
| CVE-2024-49062 | Microsoft SharePoint Data Disclosure Vulnerability |
| CVE-2024-49064 | Microsoft SharePoint Data Disclosure Vulnerability |
| CVE-2024-49082 | Home windows File Explorer Data Disclosure Vulnerability |
| CVE-2024-49087 | Home windows Cell Broadband Driver Data Disclosure Vulnerability |
| CVE-2024-49098 | Home windows Wi-fi Huge Space Community Service (WwanSvc) Data Disclosure Vulnerability |
| CVE-2024-49099 | Home windows Wi-fi Huge Space Community Service (WwanSvc) Data Disclosure Vulnerability |
| CVE-2024-49103 | Home windows Wi-fi Huge Space Community Service (WwanSvc) Data Disclosure Vulnerability |
Denial of Service (5 CVEs)
| Necessary severity | |
| CVE-2024-49075 | Home windows Distant Desktop Companies Denial of Service Vulnerability |
| CVE-2024-49096 | Microsoft Message Queuing (MSMQ) Denial of Service Vulnerability |
| CVE-2024-49113 | Home windows Light-weight Listing Entry Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2024-49121 | Home windows Light-weight Listing Entry Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2024-49129 | Home windows Distant Desktop Gateway (RD Gateway) Denial of Service Vulnerability |
Spoofing (1 CVE)
| Necessary severity | |
| CVE-2024-49057 | Microsoft Defender for Endpoint on Android Spoofing Vulnerability |
Appendix B: Exploitability
This can be a checklist of the December CVEs judged by Microsoft to be both underneath exploitation within the wild or extra more likely to be exploited within the wild throughout the first 30 days post-release. The checklist is organized by CVE.
| Exploitation detected | |
| CVE-2024-49138 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| Exploitation extra possible throughout the subsequent 30 days | |
| CVE-2024-49070 | Microsoft SharePoint Distant Code Execution Vulnerability |
| CVE-2024-49088 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-49090 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-49093 | Home windows Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2024-49114 | Home windows Cloud Recordsdata Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-49122 | Microsoft Message Queuing (MSMQ) Distant Code Execution Vulnerability |
Appendix C: Merchandise Affected
This can be a checklist of December’s patches sorted by product household, then sub-sorted by severity. Every checklist is additional organized by CVE. Patches which might be shared amongst a number of product households are listed a number of instances, as soon as for every product household. Points affecting Home windows Server are additional sorted in Appendix E.
Home windows (59 CVEs)
| Crucial severity | |
| CVE-2024-49105 | Distant Desktop Shopper Distant Code Execution Vulnerability |
| CVE-2024-49106 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49108 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49112 | Home windows Light-weight Listing Entry Protocol (LDAP) Distant Code Execution Vulnerability |
| CVE-2024-49115 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49116 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49117 | Home windows Hyper-V Distant Code Execution Vulnerability |
| CVE-2024-49118 | Microsoft Message Queuing (MSMQ) Distant Code Execution Vulnerability |
| CVE-2024-49119 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49120 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49122 | Microsoft Message Queuing (MSMQ) Distant Code Execution Vulnerability |
| CVE-2024-49123 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49124 | Light-weight Listing Entry Protocol (LDAP) Shopper Distant Code Execution Vulnerability |
| CVE-2024-49126 | Home windows Native Safety Authority Subsystem Service (LSASS) Distant Code Execution Vulnerability |
| CVE-2024-49127 | Home windows Light-weight Listing Entry Protocol (LDAP) Distant Code Execution Vulnerability |
| CVE-2024-49128 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| CVE-2024-49132 | Home windows Distant Desktop Companies Distant Code Execution Vulnerability |
| Necessary severity | |
| CVE-2024-49072 | Home windows Job Scheduler Elevation of Privilege Vulnerability |
| CVE-2024-49073 | Home windows Cell Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49074 | Home windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-49075 | Home windows Distant Desktop Companies Denial of Service Vulnerability |
| CVE-2024-49076 | Home windows Virtualization-Based mostly Safety (VBS) Enclave Elevation of Privilege Vulnerability |
| CVE-2024-49077 | Home windows Cell Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49078 | Home windows Cell Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49079 | Enter Technique Editor (IME) Distant Code Execution Vulnerability |
| CVE-2024-49080 | Home windows IP Routing Administration Snapin Distant Code Execution Vulnerability |
| CVE-2024-49081 | Wi-fi Huge Space Community Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49082 | Home windows File Explorer Data Disclosure Vulnerability |
| CVE-2024-49083 | Home windows Cell Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49084 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-49085 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-49086 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-49087 | Home windows Cell Broadband Driver Data Disclosure Vulnerability |
| CVE-2024-49088 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-49089 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-49090 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-49091 | Home windows Area Title Service Distant Code Execution Vulnerability |
| CVE-2024-49092 | Home windows Cell Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49093 | Home windows Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2024-49094 | Wi-fi Huge Space Community Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49095 | Home windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability |
| CVE-2024-49096 | Microsoft Message Queuing (MSMQ) Denial of Service Vulnerability |
| CVE-2024-49097 | Home windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability |
| CVE-2024-49098 | Home windows Wi-fi Huge Space Community Service (WwanSvc) Data Disclosure Vulnerability |
| CVE-2024-49099 | Home windows Wi-fi Huge Space Community Service (WwanSvc) Data Disclosure Vulnerability |
| CVE-2024-49101 | Wi-fi Huge Space Community Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49102 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-49103 | Home windows Wi-fi Huge Space Community Service (WwanSvc) Data Disclosure Vulnerability |
| CVE-2024-49104 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-49107 | WmsRepair Service Elevation of Privilege Vulnerability |
| CVE-2024-49109 | Wi-fi Huge Space Community Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49110 | Home windows Cell Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2024-49111 | Wi-fi Huge Space Community Service (WwanSvc) Elevation of Privilege Vulnerability |
| CVE-2024-49113 | Home windows Light-weight Listing Entry Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2024-49114 | Home windows Cloud Recordsdata Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-49121 | Home windows Light-weight Listing Entry Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2024-49125 | Home windows Routing and Distant Entry Service (RRAS) Distant Code Execution Vulnerability |
| CVE-2024-49129 | Home windows Distant Desktop Gateway (RD Gateway) Denial of Service Vulnerability |
| CVE-2024-49138 | Home windows Widespread Log File System Driver Elevation of Privilege Vulnerability |
Workplace (5 CVEs)
| Necessary severity | |
| CVE-2024-43600 | Microsoft Workplace Elevation of Privilege Vulnerability |
| CVE-2024-49059 | Microsoft Workplace Elevation of Privilege Vulnerability |
| CVE-2024-49065 | Microsoft Workplace Distant Code Execution Vulnerability |
| CVE-2024-49069 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49142 | Microsoft Entry Distant Code Execution Vulnerability |
SharePoint (5 CVEs)
| Necessary severity | |
| CVE-2024-49062 | Microsoft SharePoint Data Disclosure Vulnerability |
| CVE-2024-49064 | Microsoft SharePoint Data Disclosure Vulnerability |
| CVE-2024-49065 | Microsoft Workplace Distant Code Execution Vulnerability |
| CVE-2024-49068 | Microsoft SharePoint Elevation of Privilege Vulnerability |
| CVE-2024-49070 | Microsoft SharePoint Distant Code Execution Vulnerability |
365 (4 CVEs)
| Necessary severity | |
| CVE-2024-49059 | Microsoft Workplace Elevation of Privilege Vulnerability |
| CVE-2024-49065 | Microsoft Workplace Distant Code Execution Vulnerability |
| CVE-2024-49069 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49142 | Microsoft Entry Distant Code Execution Vulnerability |
Entry (1 CVE)
| Necessary severity | |
| CVE-2024-49142 | Microsoft Entry Distant Code Execution Vulnerability |
Defender (1 CVE)
| Necessary severity | |
| CVE-2024-49057 | Microsoft Defender for Endpoint on Android Spoofing Vulnerability |
Excel (1 CVE)
| Necessary severity | |
| CVE-2024-49069 | Microsoft Excel Distant Code Execution Vulnerability |
Muzic (1 CVE)
| Necessary severity | |
| CVE-2024-49063 | Microsoft/Muzic Distant Code Execution Vulnerability |
SCOM (1 CVE)
| Necessary severity | |
| CVE-2024-43594 | System Heart Operations Supervisor Elevation of Privilege Vulnerability |
Phrase (1 CVE)
| Necessary severity | |
| CVE-2024-49065 | Microsoft Workplace Distant Code Execution Vulnerability |
Appendix D: Advisories and Different Merchandise
This can be a checklist of advisories and data on different related CVEs within the December launch.
Microsoft info:
| CVE / identifier | Product | Title |
| ADV240002 | Venture 2016 | Microsoft Workplace Protection in Depth Replace |
| CVE-2024-12053 | Edge | Chromium: CVE-2024-12053 Kind Confusion in V8 |
| CVE-2024-49041 | Edge | Microsoft Edge (Chromium-based) Spoofing Vulnerability |
Adobe Reader advisories:
| CVE | Bulletin | Title |
| CVE-2024-49531 | APSB24-92 | NULL Pointer Dereference (CWE-476) |
| CVE-2024-49530 | APSB24-92 | Use After Free (CWE-416) |
| CVE-2024-49532 | APSB24-92 | Out-of-bounds Learn (CWE-125) |
| CVE-2024-49533 | APSB24-92 | Out-of-bounds Learn (CWE-125) |
| CVE-2024-49534 | APSB24-92 | Out-of-bounds Learn (CWE-125) |
| CVE-2024-49535 | APSB24-92 | Improper Restriction of XML Exterior Entity Reference (‘XXE’) (CWE-611) |
Appendix E: Affected Home windows Server variations
This can be a desk of CVEs within the December launch affecting 9 Home windows Server variations — 2008 by way of 2025. The desk differentiates amongst main variations of the platform however doesn’t go into deeper element (eg., Server Core). Crucial-severity points are marked in purple; an “x” signifies that the CVE doesn’t apply to that model. Directors are inspired to make use of this appendix as a place to begin to establish their particular publicity as every reader’s scenario, particularly because it issues merchandise out of mainstream help, will differ.
| 2008 | 2008-R2 | 2012 | 2012-R2 | 2016 | 2019 | 2022 | 2022 23H2 | 2025 | |
| CVE-2024-49072 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49073 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49074 | × | × | × | × | × | ■ | × | × | × |
| CVE-2024-49075 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49076 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49077 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49078 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49079 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49080 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49081 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49082 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49083 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49084 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49085 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49086 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49087 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49088 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49089 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49090 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49091 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49092 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49093 | × | × | × | × | × | × | × | × | ■ |
| CVE-2024-49094 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49095 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49096 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49097 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49098 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49099 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49101 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49102 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49103 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49104 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49105 | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49106 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49107 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49108 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49109 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49110 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49111 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2024-49112 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49113 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49114 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49115 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49116 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49117 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2024-49118 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49119 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49120 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49121 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49122 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49123 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49124 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49125 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49126 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49127 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49128 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49129 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-49132 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2024-49138 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |