On October 28th, 2024, the Dutch Nationwide police, alongside the FBI, Eurojust, and several other different legislation enforcement organizations, carried out a takedown of the notorious RedLine Stealer malware-as-a-service (MaaS) operation, and its clone known as META Stealer. This international effort, named Operation Magnus, resulted within the takedown of three servers within the Netherlands, the seizure of two domains, two individuals being taken into custody in Belgium, and the unsealing of expenses in opposition to one of many alleged perpetrators in the US.
Again in April 2023, ESET participated in a partial disruption operation of the RedLine malware, which consisted of the elimination of a number of GitHub repositories used as dead-drop resolvers for the malware’s management panel. Round that point, we investigated beforehand undocumented backend modules of this malware household in collaboration with fellow researchers at Flare. These modules don’t work together instantly with the malware, however quite deal with authentication and supply performance for the management panel.
Since RedLine has now been taken down, we’re revealing our findings from 2023 publicly, together with some more moderen discoveries that had been made based mostly on supply code and samples shared with us by the Dutch Nationwide Police.
Be aware that even with the takedown, RedLine could proceed working to some extent for a time: panels that had been already working would nonetheless be capable of obtain knowledge, even when unable to construct new samples or reconnect after logging out. Furthermore, there are additionally previous, cracked copies of the malware which may nonetheless work. Due to these elements, we’re describing the RedLine operation as whether it is an ongoing exercise.
Key factors of the blogpost:
- In 2023, ESET researchers, in collaboration with legislation enforcement, collected a number of modules used to run the infrastructure behind RedLine Stealer.
- We analyzed these beforehand undocumented modules to offer perception into the interior workings of this malware-as-a-service empire.
- We had been capable of establish over 1,000 distinctive IP addresses used to host RedLine management panels.
- The 2023 variations of RedLine Stealer we investigated intimately used the Home windows Communication Framework for communication between the parts, whereas the most recent model from 2024 makes use of a REST API.
- Primarily based on our evaluation of the supply code and backend samples, we’ve got decided that Redline Stealer and META Stealer share the identical creator.
RedLine Stealer is info stealing malware first found in 2020 by Proofpoint. Somewhat than being centrally operated, RedLine operates on a MaaS mannequin during which anybody should purchase a turnkey infostealer answer from varied on-line boards and Telegram channels. Shoppers, known as associates, can go for a month-to-month subscription, or a lifetime license; in alternate for his or her cash, they get a management panel that generates malware samples and acts as a C&C server for them. The generated samples can gather a big number of info, together with native cryptocurrency wallets; cookies, saved credentials, and saved bank card particulars from browsers; and saved knowledge from Steam, Discord, Telegram, and varied desktop VPN purposes.
Utilizing a ready-made answer makes it simpler for the associates to combine RedLine Stealer into bigger campaigns. Some notable examples embody posing as free downloads of ChatGPT in 2023, and masquerading as online game cheats within the first half of 2024.
Be aware on terminology used
Due to its MaaS mannequin, any complete dialogue of RedLine will contain a number of totally different parts and layers of community infrastructure. To restrict any doable confusion, we’ll use the next phrases persistently all through the textual content:
- RedLine malware: The RedLine Stealer malware or a pattern thereof.
- RedLine panel: GUI management panel used to handle infostealing campaigns.
- RedLine backend: Assortment of modules that present authentication and performance for the RedLine panel.
- RedLine: The entire malware operation. This contains the RedLine malware, the RedLine panel, and the RedLine backend modules.
- Backend server: A server on which the RedLine backend runs.
- Sufferer: Entity focused with the RedLine malware.
- Operator: The person or staff that develops RedLine, sells licenses, and operates the licensing and related backend infrastructure.
- Affiliate: Entity that operates infostealing campaigns through an occasion of the RedLine panel. They often have a license purchased from the operator, however might also use a cracked model of the panel.
Overview
On this blogpost we doc modules working on RedLine’s backend servers to offer a larger understanding of the internal workings of this MaaS empire. We additionally present some info on the RedLine panel. Determine 1 accommodates a simplified overview of the entire RedLine operation.
Ordinarily, identified samples of RedLine panel distributed to associates are closely packed and virtualized after the primary layer of obfuscation is utilized. However as we had been trying via our telemetry for exercise associated to RedLine Stealer and its panel, we got here throughout an previous model of the RedLine panel that was solely obfuscated with .NET Reactor, making it a lot simpler to investigate.
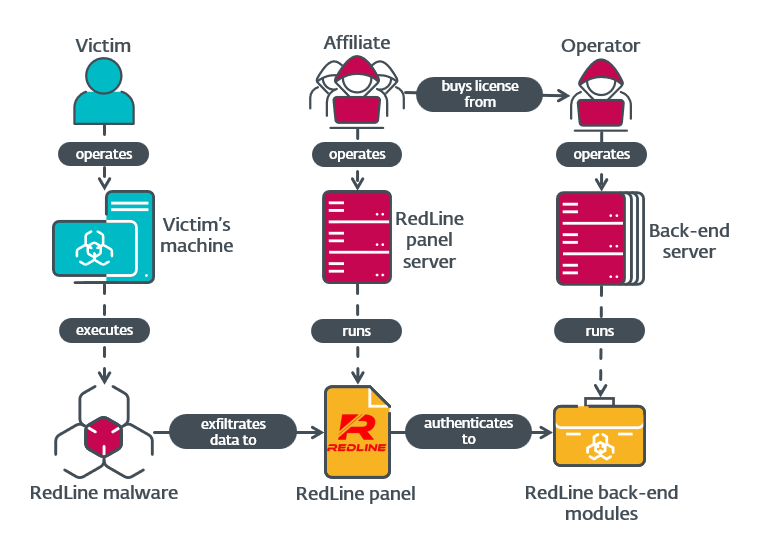
RedLine’s toolset
All of the parts of RedLine, from the malware itself to the backend authentication server, are written in C# with the .NET framework. The variations we analyzed used the Home windows Communication Basis (WCF) framework to speak with one another. This framework permits one to outline an API utilizing contracts, that are statements utilized to courses and interfaces to specify how objects and actions are translated between their illustration within the code and the community communications. Thus, applications that work together utilizing this framework should share definitions of those knowledge buildings or courses. These shared fashions proved helpful in our evaluation of the obfuscated parts.
Be aware that the most recent 2024 RedLine model makes use of a REST API as an alternative of WCF to speak with the backend.
RedLine panel
This management panel is what associates should purchase on boards and Telegram channels. Licenses promote for US$150 per 30 days or US$900 for a lifetime license. In alternate for the cash, the associates get a GUI via which they handle their campaigns, with options to configure what info to gather, create malware samples, view and handle collected info, and combine with a Telegram bot to promote stolen info.
The 2023 variations of the panel we investigated had been closely obfuscated utilizing DNGuard, a widely known .NET obfuscator, and BoxedApp, a business packer and virtualization library. Fortunately for us, RedLine used the WCF framework so the panel needed to share some courses and interfaces with different parts. By analyzing these shared parts from the malware and backend parts, that are much less protected, we had been capable of perceive numerous the panel’s performance regardless of the protections.
All RedLine panels from 2023 had been signed with certificates issued to AMCERT,LLC by Sectigo, which have since been revoked after we reported them. AMCERT,LLC corresponds to an organization registered in Armenia that doesn’t appear to have a web based presence – fairly uncommon for a purported software program developer.
Authentication
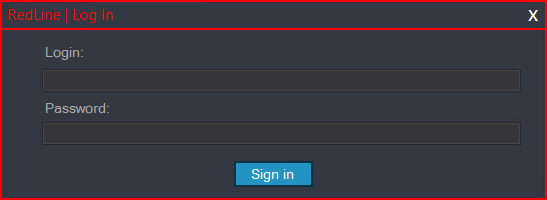
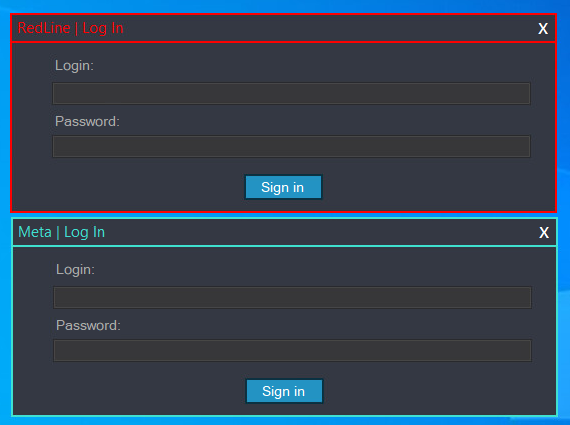
So as to use a RedLine panel, associates should first authenticate. Determine 2 reveals the login immediate.
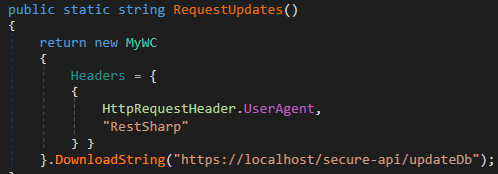
The RedLine panels we analyzed use GitHub repositories, just like the one in Determine 3, as dead-drop resolvers for his or her authentication servers. The deal with of this repository is hardcoded within the panel, however it isn’t the identical for all variations of the panel. Discovering and eradicating a number of of those repositories in cooperation with GitHub is what enabled us to briefly disrupt RedLine operations in April 2023. Whereas the elimination didn’t have an effect on the malware’s backend, it pressured the operators to distribute new variations of the panels. For a short time after the disruption, they moved the dead-drop resolvers to Pastebin, earlier than selecting to make use of their very own domains in Might 2023, as described in our joint speak with Flare at Sleuthcon 2023. Within the newest model of the RedLine panel, the risk actors deserted the dead-drop resolvers utterly and easily used a hardcoded URL https://fivto[.]on-line/secure-api/. Extra info on the dead-drop resolvers could be discovered within the Community infrastructure part.
By working the backend server parts in a digital community, we managed to create affiliate accounts and authenticate with our personal occasion with out having to purchase a subscription.
The primary display screen proven to associates upon logging in, seen in Determine 4, is full of adverts. Whereas we have no idea the precise nature of the adverts served by the actual authentication servers, we had been capable of create some in our personal occasion of the backend server for demonstration functions. The backend server doesn’t host the precise pictures current in these adverts, solely their URLs.

The Black Lists tab permits associates to disregard incoming knowledge by nation, IP deal with, Construct ID, or HWID (a singular ID computed from a sufferer machine’s area identify, username, and serial quantity). Whatever the exclusions chosen right here, samples of RedLine Stealer all comprise code to stop execution if the locale is ready to one of many following nations: Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Tajikistan, Uzbekistan, Ukraine, and Russia.
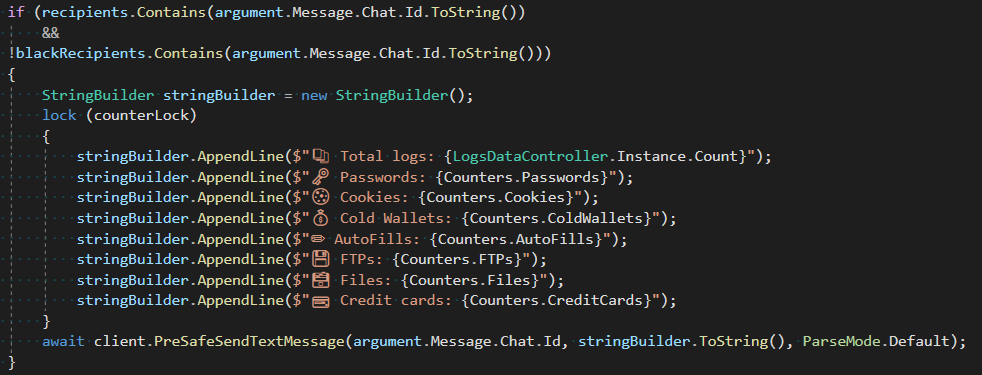
The Telegram tab, proven in Determine 5, permits associates to configure a Telegram bot to submit stolen knowledge to particular chats or channels. The affiliate should present a sound API token for the bot, after which can choose which entries shall be shared based mostly on the nation, Construct ID, OS model, and domains present in cookies or saved logins. The bot will also be configured to share the total logs or solely particular info as outlined within the Message Format area, and to share statistics with the chosen recipients (see Determine 6).
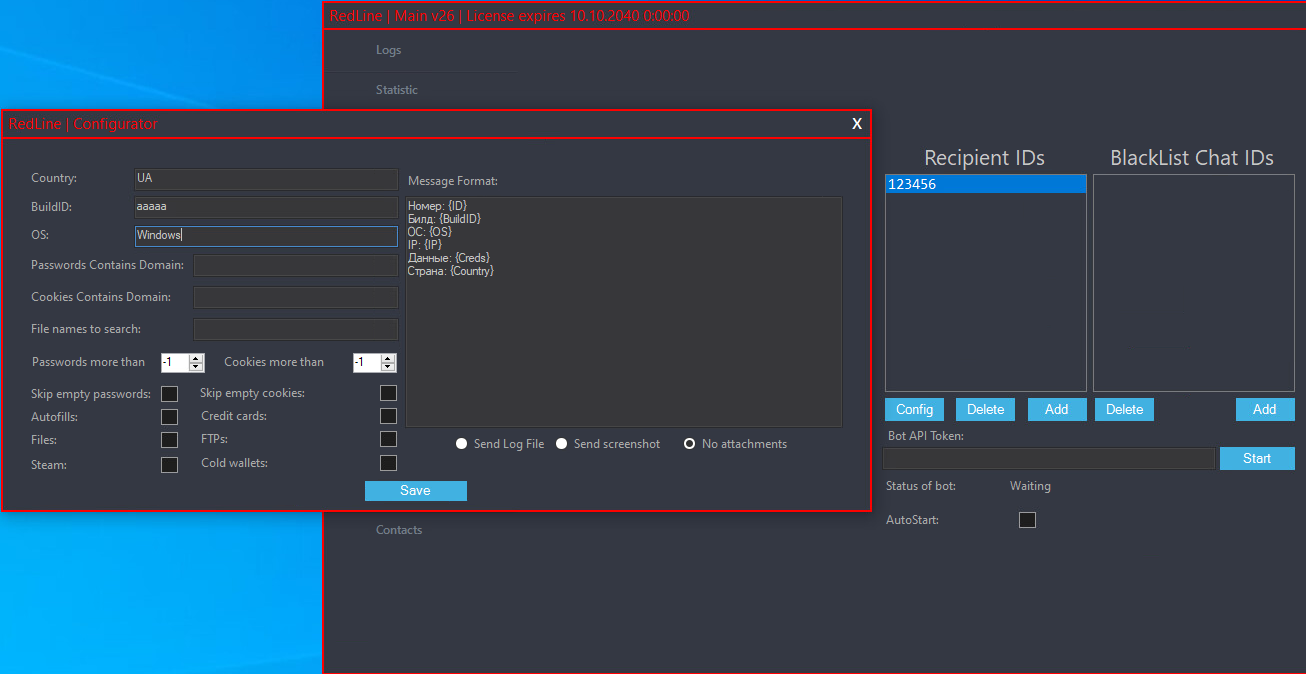
Creating malware samples within the entrance finish
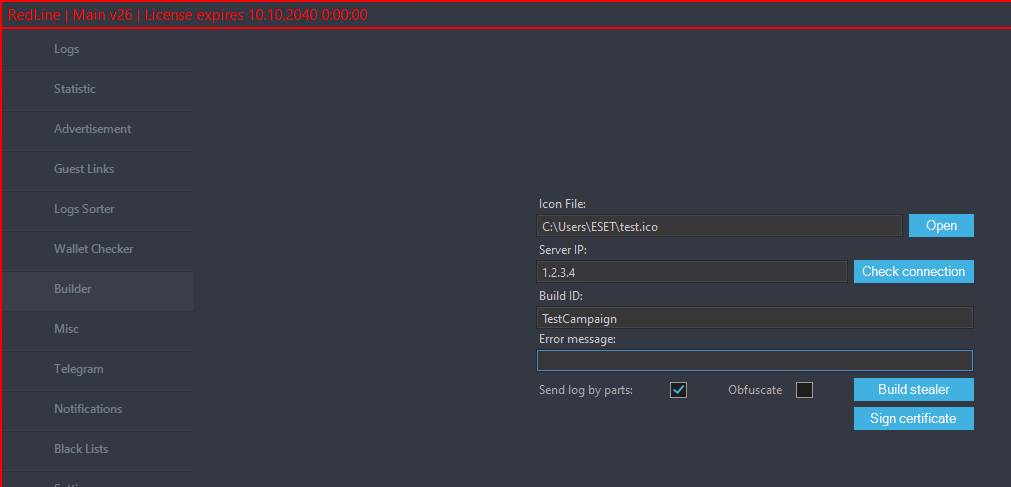
The Builder tab, proven in Determine 7, permits associates to create new RedLine Stealer samples by offering a RedLine panel server deal with, a Construct ID, an error message to show, and a picture for use because the icon for the created pattern. These final two are elective, with the picture serving because the icon of the software program RedLine is impersonating, whereas the error message can be utilized to mislead the sufferer as to why the anticipated software wasn’t began.
The Construct ID is used as a marketing campaign identifier and is shipped by the samples together with stolen info. Whereas some beforehand leaked variations of the RedLine panel included an executable to create builds domestically, in newer variations that is carried out by the backend server. This modification makes any leaked or cracked RedLine panel a lot much less helpful since associates gained’t have the power to create samples to make use of with it. We describe the construct course of within the RedLine.Nodes.LoadBalancer part.
RedLine backend
The RedLine backend we analyzed in 2023 consists of two modules. The primary one, named RedLine.Nodes.DbController, manages affiliate and commercial knowledge. Regardless of its identify, this module doesn’t use a standard database, however quite shops data as Protobuf-encoded objects in particular person information, with a selected subdirectory for every sort of knowledge. The second module, named RedLine.Nodes.LoadBalancer, capabilities because the server and offers a lot of the performance utilized by the RedLine panel.
We additionally discovered a module known as RedLine.MainServer, which might be the ancestor of RedLine.Nodes.DbController and RedLine.Nodes.LoadBalancer. In later variations, it was cut up off as a separate module that handles consumer and commercial knowledge.
Within the 2024 model of the backend, DbController and LoadBalancer have been changed by a single module named Nodes.Api.
RedLine.Nodes.DbController
In DbController, affiliate knowledge is represented by a category named ClientData, detailed in Desk 1.
Desk 1. Description of ClientData properties
That is principally simple however presents a couple of fascinating quirks, primarily the way in which passwords and lifelong licenses are dealt with.
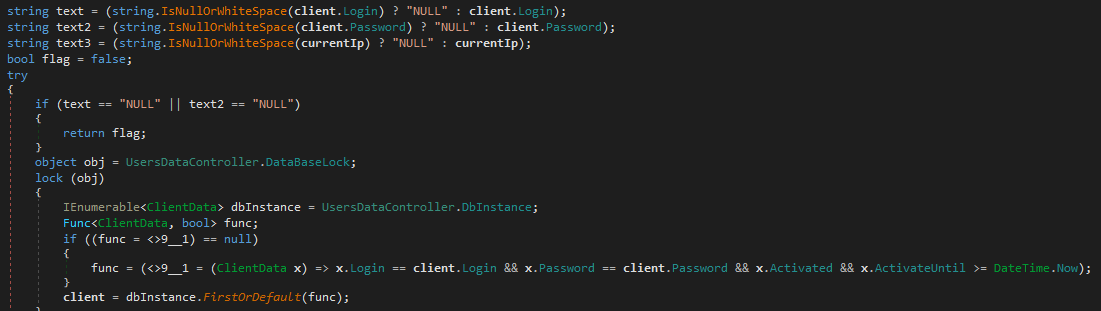
Wanting on the code used to authenticate associates (proven in Determine 8) makes it apparent that passwords are saved in cleartext. The submitted password is in contrast on to the saved one with none hashing operate being concerned.
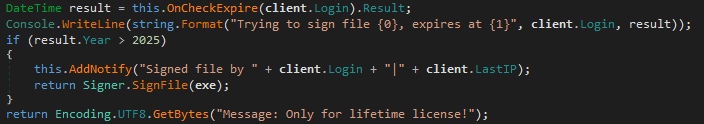
Determine 9 reveals {that a} lifetime license, which associates should purchase for US$900, is represented by setting the expiration date of a given license to any date after 2025. That is alternatively known as a Professional License elsewhere within the code.
RedLine.Nodes.LoadBalancer
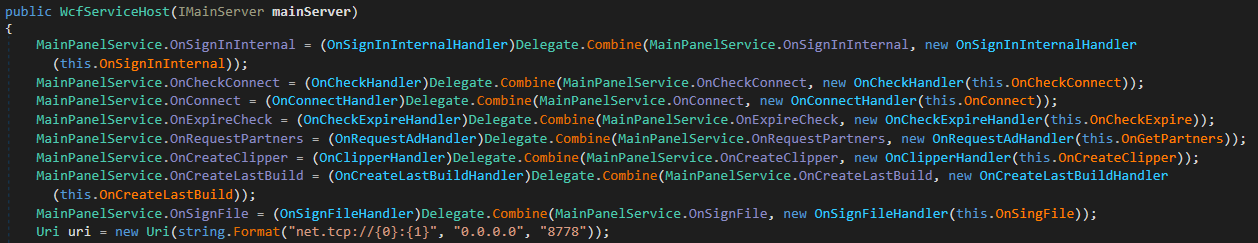
As seen in Determine 10, the LoadBalancer module listens on port 8778. This screenshot additionally reveals the handlers outlined within the MainPanelService WCF contract. The handlers which are associated to affiliate and commercial knowledge – specifically OnSignInInternal, OnConnect, OnCheckExpire, and OnGetPartners – delegate requests to the corresponding handler of DbController. The OnCheckConnect handler is utilized by the Redline panel to test whether or not its C&C server is reachable from the outside. The remainder of the handlers all relate to the creation of malware samples.
Pattern creation in Redline backend
Because it was first documented in 2020, RedLine Stealer has been rewritten to make use of the WCF framework, and later a REST API, for community communication. As seen in Determine 11, the interior identify for these rewritten variations seems to be RedLine.Reburn.
To create samples of the RedLine Stealer malware, the OnCreateLastBuild handler proven in Determine 10 makes use of the CreateBuild technique from the customized VSBuilder class. When a CreateBuild request is obtained, the cleartext password for the affiliate’s account is logged to the console. This reveals an informal disregard for well-known safety practices.
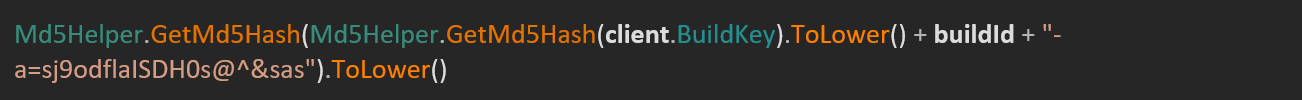
If within the request no port is specified for the C&C server, the builder defaults to port 6677. When constructing a pattern, the code in Determine 12 is used to derive a token from the marketing campaign’s Construct ID and the affiliate account’s Construct Key. We imagine this corresponds to the worth of the ns1.Authorization header utilized in communication between the samples and panel. This header appears to be utilized by the panel to filter out connections from samples not created by the present account.
The VSBuilder.CreateBuild technique makes use of a neighborhood C# answer to create samples. Among the supply information are learn into reminiscence to switch particular values earlier than being written again to disk. Whereas we had been unable to gather the undertaking’s information, the decompiler output for this technique together with that of a RedLine Stealer pattern present sufficient context to grasp that the modified values are:
- C&C deal with (encrypted),
- Construct ID (encrypted),
- pretend error message (encrypted),
- decryption key,
- flag to point whether or not to ship stolen info in components or abruptly,
- authentication token, and
- meeting identify.
As soon as these values are changed, Visible Studio is invoked to construct the undertaking.
If the affiliate has chosen the corresponding choice, and has a lifetime license, the compiled executable is obfuscated with the commercially out there Babel Obfuscator. Within the 2024 model, obfuscation is applied for all customers and is finished through .NET Reactor as an alternative.
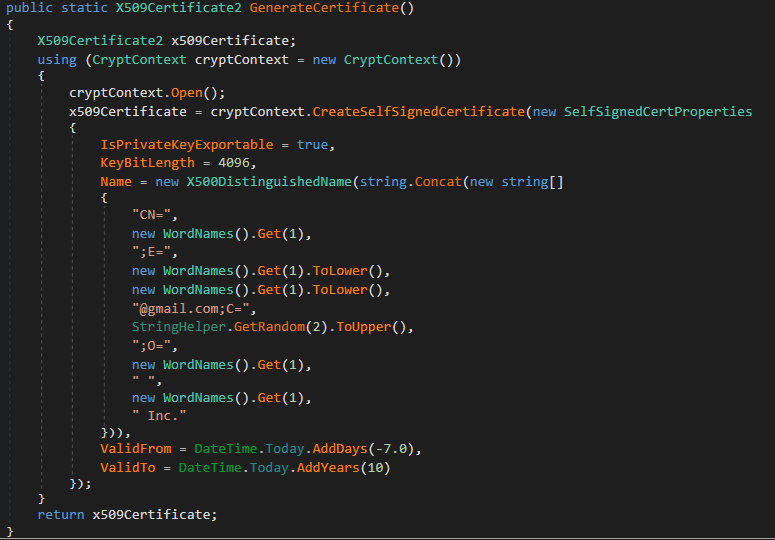
Lastly, a self-signed certificates is generated with the code from Determine 13, and used to signal the executable. The fields of its Distinguished Identify (DN) are full of random dictionary phrases. The certificates generated this manner use the hardcoded password 123321 and have a validity interval extending from seven days earlier than their era to 10 years after.
The LoadBalancer module additionally supplied an OnCreateClipper handler. Because the identify suggests, this was used to generate clipboard hijacking malware; on this case, it was used to hijack cryptocurrency transactions by changing pockets addresses within the clipboard with these of attacker-controlled wallets. This performance has been eliminated within the newest variations of the Redline backend.
Apparently, the Builder class additionally contained useless code to generate a malware pattern from a stub executable. We imagine this was a leftover from the strategy used to generate earlier variations of RedLine Stealer. The newest model of the Redline backend doesn’t comprise the code anymore.
One other handler, named OnSignFile, permits associates with lifetime licenses to signal arbitrary information with a certificates situated on the backend server. We had been unable to gather this certificates, however have motive to imagine that it might be the identical certificates used to signal RedLine panels, because it has additionally been used to signal a lot of RedLine Stealer and different malware samples. One other possible candidate is the certificates with the thumbprint 28F9A8E7601F5338BF6E194151A718608C0124A8, issued to Hangil IT Co., Ltd. This, possible stolen, certificates has been used to signal many RedLine Stealer samples and different malicious information. It has already been revoked.
RedLine.MainServer
The RedLine.MainServer module combines among the performance of the 2 earlier modules with a GUI that permits the admin to simply handle affiliate accounts and commercial knowledge. Regardless of this added performance, a number of elements point out that this model of MainServer might be an ancestor of LoadBalancer and DbController quite than a successor:
- MainServer samples are compiled with an older model of the .NET framework (4.6.2 vs 4.8).
- The meeting’s copyright yr is 2020 as an alternative of 2021.
- Some MainServer samples don’t comprise performance for ads.
- The principle WCF service’s contract (MainPanelService) doesn’t embody the IsAlive handler that’s current in the identical class as LoadBalancer. This handler is utilized by all the newest RedLine panels we’ve got analyzed.
Be aware that in later variations of the RedLine backend, the GUI administration panel has been cut up off into its personal module additionally named MainServer.
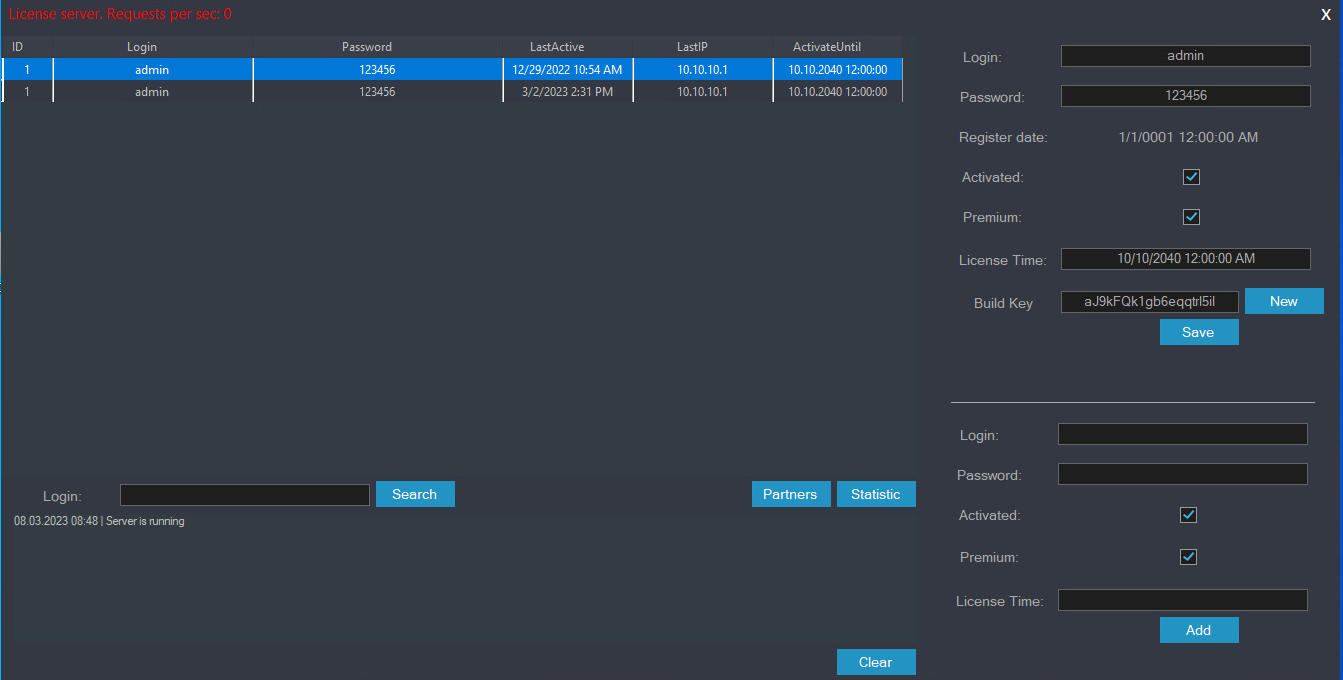
The examined model of the GUI gave us fascinating perception into RedLine administration. It offers a kind to create and edit affiliate account knowledge, as proven in Determine 14. The fields correspond to the ClientData class described beforehand.
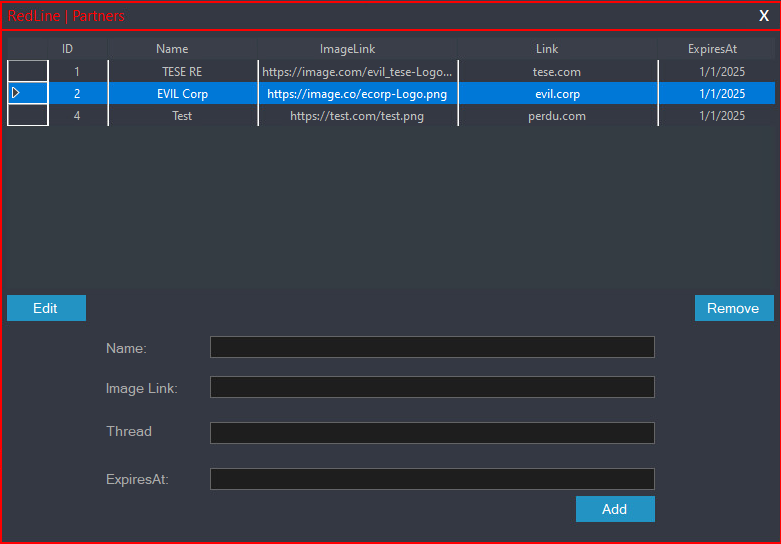
The same kind, in Determine 15, exists to handle ads.
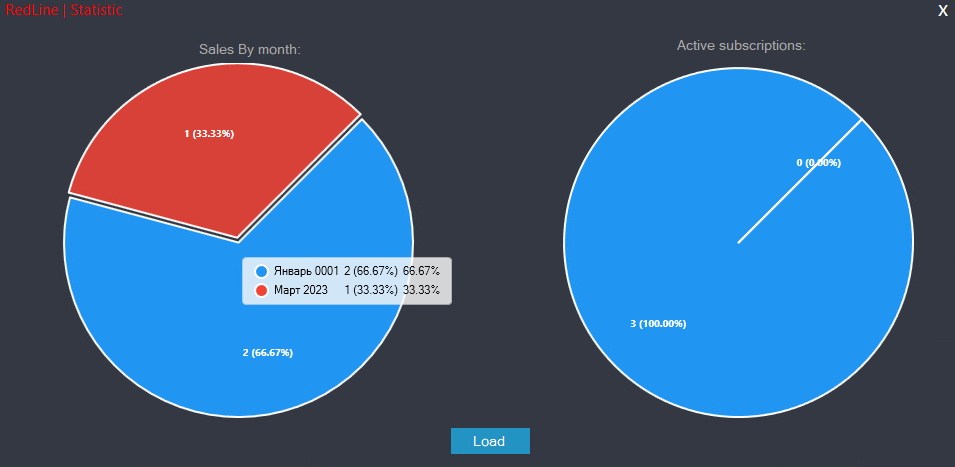
Lastly, the rudimentary dashboard in Determine 16 offers the operator an outline of license gross sales.
Nodes.Api
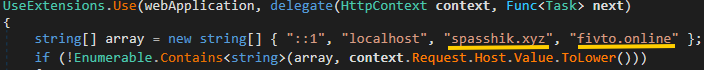
Evaluation of samples shared by Dutch legislation enforcement reveals that within the newest RedLine variations, the functionalities of the LoadBalancer and DbController modules have been mixed into a brand new one named Nodes.Api. This backend module is packaged as a single-file .NET software and makes use of the WebApplication class from ASP.NET to offer the REST API utilized by the panels. As seen in Determine 17, the module handles requests despatched to each RedLine (fivto[.]on-line) and META (spasshik[.]xyz) servers, displaying that the 2 infostealers share the identical operators.
Desk 2 lists the endpoints uncovered by the REST API together with the corresponding WCF handler from earlier variations.
Desk 2. RedLine endpoints
| Endpoint | Corresponding WCF Handler | Description |
| /api/take a look at | N/A | Most likely used to check connectivity. This merely returns the worth OK. |
| /secure-api/sign-in | OnSignInInternal | Handles logins from the panel. |
| /secure-api/getBanners | OnGetPartners | Returns the adverts to be displayed within the panel. |
| /secure-api/createFile | OnCreateLastBuild | Creates an occasion of the stealer malware. |
| /secure-api/checkConnect | OnCheckConnect | Pings the required deal with and port to test whether or not it’s externally reachable. |
| /secure-api/updateDb | N/A | Makes the backend reload affiliate knowledge. That is solely achieved if the request comes from a loopback deal with. |
| /edk92hd/createRandom | N/A | Creates a brand new affiliate entry with a random username and password. |
| /edk92hd/renew | N/A | Extends the license validity interval of the required affiliate. |
| /Panel.zip | N/A | Returns the Panel.zip file from disk. This password-protected archive accommodates the most recent model of the panel. |
Not like the 2023 variations of the backend we initially analyzed, lifetime licenses not seem within the code of the brand new module. Since licenses of this sort had been nonetheless being offered, we imagine they had been possible dealt with by merely setting their expiration to a date far sooner or later. Performance associated to code signing has additionally been utterly eliminated.
Samples created by the Nodes.Api module are obfuscated utilizing .NET Reactor whether it is current on the hardcoded path C:Program Recordsdata (x86)Eziriz.NET ReactordotNET_Reactor.exe. This corresponds to its default set up path.
Past the aforementioned modifications, options that had been current in older variations behave a lot as they did earlier than. Nonetheless, a few fascinating functionalities have been added.
Affiliate administration
Three endpoints used to handle affiliate knowledge are uncovered. These look like meant to be used solely by the operator, however that is dealt with in two very other ways. The /secure-api/updateDb endpoint causes the server to reload consumer knowledge from disk. Determine 18 reveals the replace technique invoked by the MainServer module at any time when a brand new entry is created or modified. The operation is just carried out by the Nodes.Api module if the request comes from a loopback deal with, which prevents Panel customers from utilizing it.
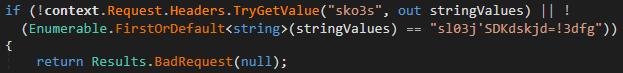
The opposite two endpoints, /edk92hd/createRandom and /edk92hd/renew, use a special technique of mitigating unauthorized entry. As seen in Determine 19, they’ll solely be invoked if the request accommodates an sko3s header set to a seemingly random hardcoded worth.
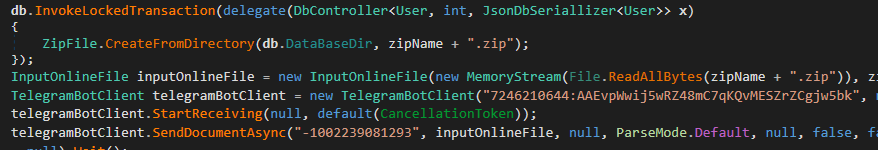
Backups
The opposite fascinating function is the power to again up affiliate knowledge, performance that was lacking within the older variations of the code. Since this knowledge is saved in a collection of information on disk, the backup is a ZIP archive of the listing that accommodates the information. This archive is then despatched through Telegram utilizing a hardcoded Chat ID proven in Determine 20.
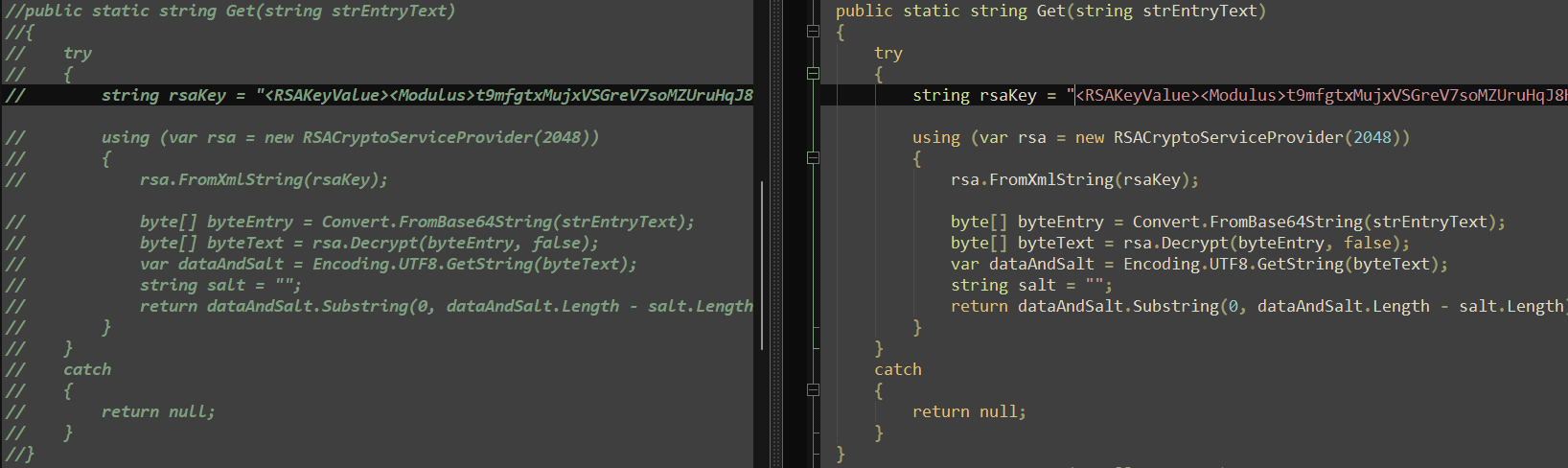
Hyperlinks with META Stealer
META Stealer is the opposite infostealer disrupted alongside RedLine Stealer. In keeping with an article by Kela, META Stealer was first introduced on cybercrime boards in March 2022. The writer claimed that it used the identical code as RedLine Stealer and supplied the identical performance and panel. META Stealer hasn’t been investigated as totally as RedLine Stealer, however our analysis signifies that the claims it initially made are correct. Primarily based on the supply code, the 2 infostealers are likely made by the identical particular person. Whereas there are some variations, a lot of the code is identical with cases of the string RedLine changed by Meta. As could be seen in Determine 21, the code that’s commented out to be inactive in RedLine is current in META.
As we already talked about, one other piece of proof pointing in the direction of RedLine and META having the identical operators is seen within the code of the Nodes.Api module, which handles requests despatched to each RedLine and META servers, as proven in Determine 17.
We additionally discovered two samples of the META panel signed with a certificates that was additionally used to signal samples of the RedLine panel. This panel used the identical dead-drop resolver schemes, going so far as utilizing the identical AES and RSA keys, solely with a special GitHub repository. Moreover, as Determine 22 reveals, a comparability of the panels utilized by META and RedLine reveals solely minor beauty variations.
META Stealer makes use of the identical mixture of DNGuard and BoxedApp to guard its panel from evaluation. Nonetheless, META’s authentication course of couldn’t be accomplished when run in opposition to our occasion of the RedLine backend from 2023, so it appears to have been modified from that of RedLine.
Community infrastructure
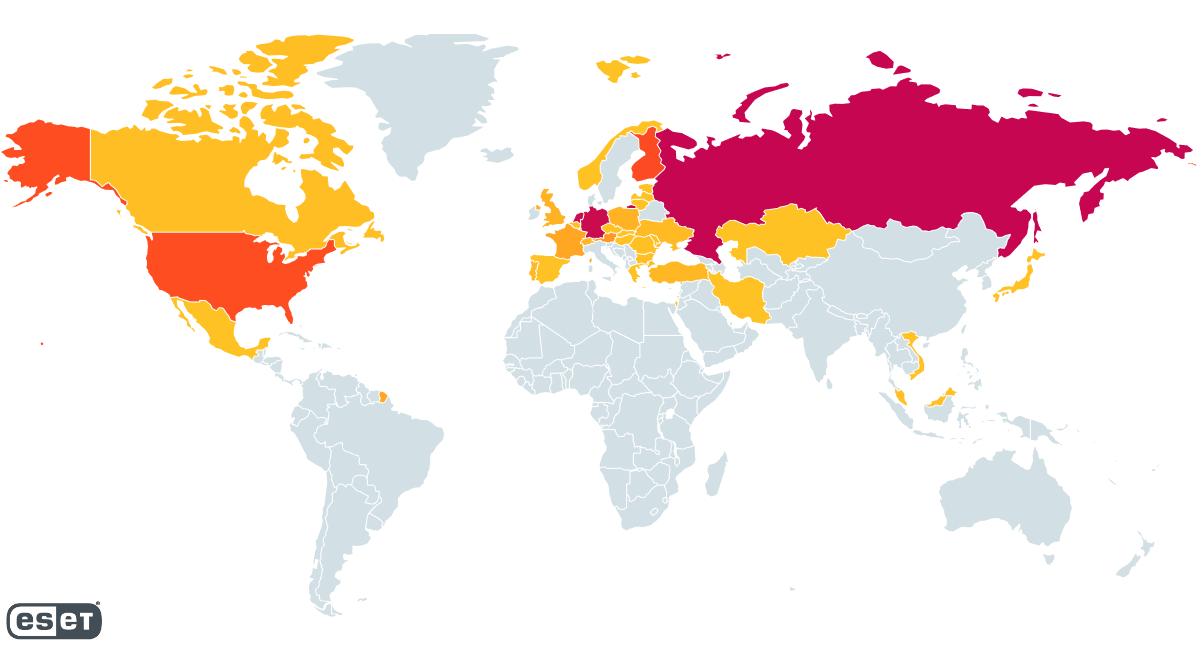
By parsing samples of RedLine that we detected between November 30th, 2022 and March 23rd, 2023, we had been capable of establish over 1,000 distinctive IP addresses used to host RedLine panels. Determine 23 reveals the geographical distribution of those hosted panels. Russia, Germany, and the Netherlands every account for about 20% of the overall, whereas Finland and the US every signify round 10%. Although this knowledge solely comes from samples focusing on our prospects, we imagine it paints a reasonably correct image almost about the general distribution of the malware.
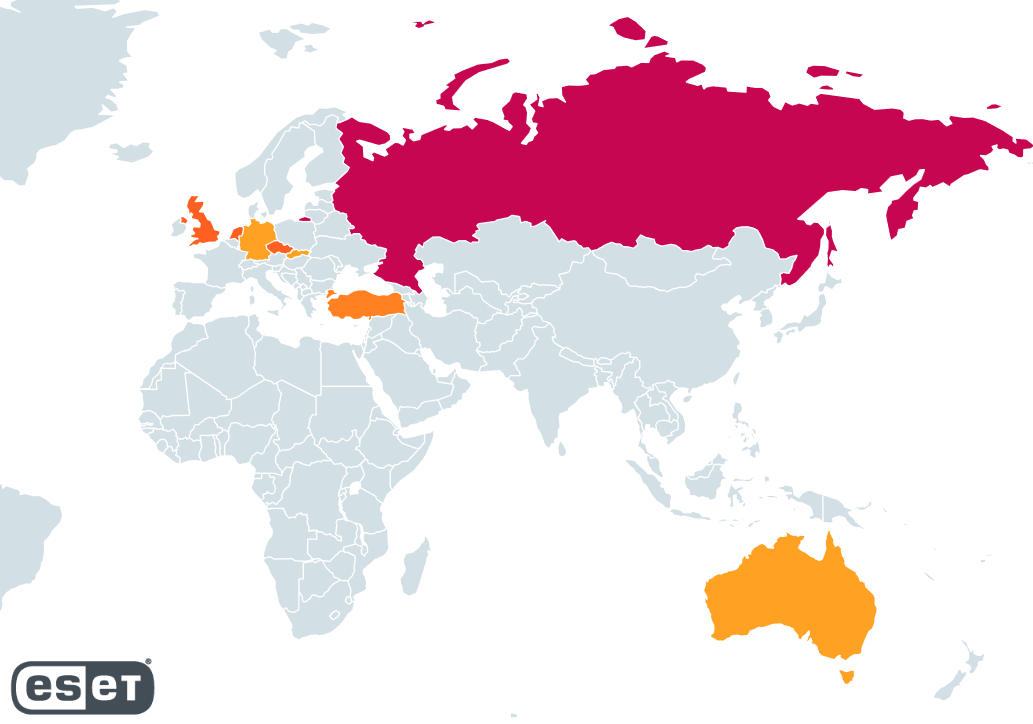
We had been additionally capable of establish a number of distinct backend servers. It’s possible that there have been extra within the dead-drop resolvers that we couldn’t decrypt. Primarily based on their geographical distribution, proven in Determine 24, the servers are primarily situated in Russia (a few third of them) whereas the UK, the Netherlands, and the Czech Republic every signify round 15% of the servers we recognized.
Useless-drop resolvers
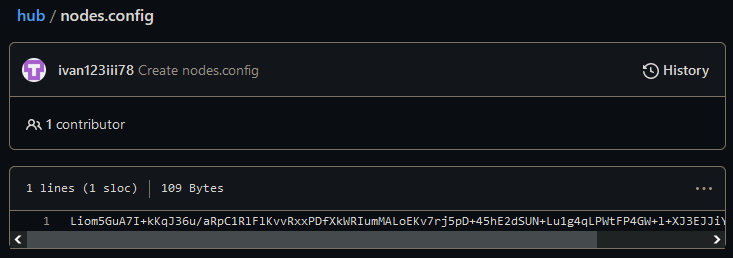
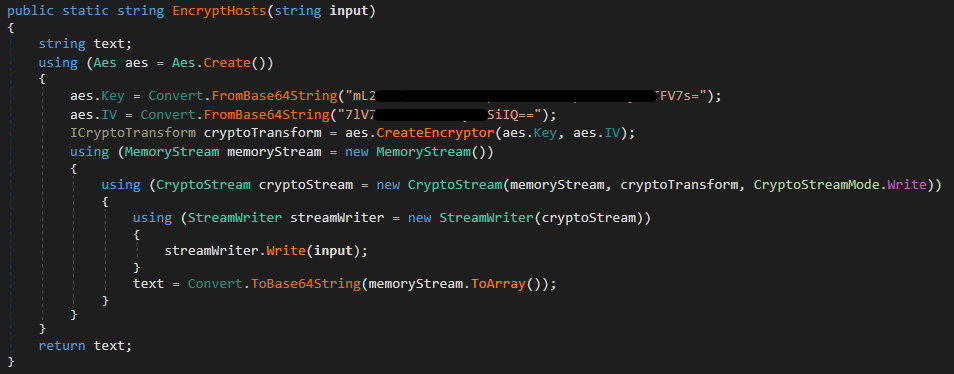
As we already talked about, the 2023 variations of the RedLine panel used GitHub repositories as dead-drop resolvers for its authentication servers. These repositories all contained a file with an encrypted record of server addresses. The file was encrypted utilizing a customized module merely named RSA. In a single model of this module, proven in Determine 25, the record was encrypted utilizing AES-CBC with a hardcoded key and IV, and saved to a file named nodesUpdate.config.
Newer variations, which had been in use not less than till mid 2024, make use of RSA encryption as an alternative (see Determine 26), with the output written to a file named nodes.config. On this case, the hot button is learn from a file quite than being hardcoded within the executable. Nonetheless, the category used to carry out RSA encryption can also be current within the LoadBalancer module, with hardcoded default values for the private and non-private keys. Be aware the usage of “nodes” once more to check with the backend servers.
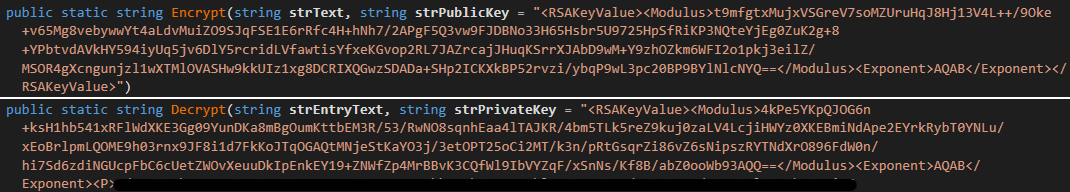
We have now noticed GitHub repositories that comprise not less than one such encrypted file. Together with the keys proven above, we had been capable of extract an RSA personal key from a pattern of the panel. This allowed us to acquire lists of authentication servers, which we shared with legislation enforcement businesses.
Conclusion
Earlier than Operation Magnus, RedLine was among the many most widespread of infostealer malware with a really giant variety of associates utilizing its management panel. Nonetheless, the malware-as-a-service enterprise appears to be orchestrated by solely a handful of individuals, a few of whom have been recognized by legislation enforcement.
META Stealer, RedLine Stealer’s clone and likely created by the identical risk actors, made its entry into the sector in 2022. It doesn’t look like a successor to RedLine, for the reason that growth of each households has continued in parallel. It was taken down alongside RedLine Stealer.
Our in-depth evaluation of the behind-the-scenes components of RedLine – its management panel and backend – hopefully offers a extra holistic understanding of this risk.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis presents personal APT intelligence stories and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
A complete record of indicators of compromise (IoCs) and samples could be present in our GitHub repository.
Recordsdata
| SHA-1 | Filename | Detection | Description |
| 1AD92153B56FC0B39F8F |
Nodes.Api.exe | N/A | RedLine backend single-file software. |
| 8A0CAFE86C0774F1D9C7 |
MainServer.exe | N/A | RedLine backend consumer and commercial administration module (2024 model). |
| 607DBA5F630A1DBFF0E1 |
Nodes.Api.dll | N/A | RedLine backend primary module. |
| FB3ABAC1FAC852AE6D22 |
Panel.exe | MSIL/Spy.RedLine.O | META stealer panel (2024 model). |
| EE153B3F9B190B1492DE |
RedLine.MainPanel.exe | MSIL/Spy.RedLine.H | RedLine stealer panel (2024 model). |
| 1AB006B1C5403BA46480 |
Panel.exe | MSIL/Spy.RedLine.O | RedLine stealer panel (2024 model). |
| DC3A236245AE8C4D5D07 |
RedLine.MainServer.exe | N/A | RedLine backend licensing server GUI. |
| 06A2A900561C122F4508 |
rsa.exe | N/A | Software to encrypt the record of C&C servers. |
| 1626F2666782710FC28D |
RedLine.Nodes |
N/A | RedLine backend server module. |
| 37D1221CE6BB82E7AD08 |
RedLine.SharedModels |
MSIL/Spy.RedLine.Ok | RedLine WCF fashions and contracts definitions. |
| 66C0E7E74C593196E092 |
Panel.exe | Win32/GenCBL.ATC | RedLine panel (v22.4). |
| 2E5D9F2ED82C81609F4C |
RedLine.MainPanel.exe | MSIL/Spy.RedLine.H | RedLine panel (non-virtualized). |
| 47B78A5698A289C73175 |
RedLine.SharedModels |
MSIL/Spy.RedLine.J | RedLine fashions and contracts definitions. |
| 49BE1D7C87AC919BB908 |
Panel.exe | MSIL/Spy.RedLine.H | META Stealer Panel. |
| 4BF4D42EED7FCA8FD528 |
RedLine.Nodes |
N/A | RedLine backend server consumer and commercial administration module. |
| 27BD472729439D5B8814 |
Panel.exe | MSIL/Spy.RedLine.H | RedLine panel (v26). |
| A154DFAEDC237C047F41 |
Panel.exe | MSIL/Spy.RedLine.H | RedLine Panel (leaked cracked model). |
Community
Be aware that the domains within the desk beneath have been seized by legislation enforcement. The opposite panel and server addresses that we collected had been shared with legislation enforcement businesses frequently to assist in their actions and are not energetic.
| IP | Area | Internet hosting supplier | First seen | Particulars |
| N/A | spasshik[.]xyz | N/A | 2024-06-02 | META backend REST server. |
| N/A | fivto[.]on-line | N/A | 2024-08-03 | RedLine backend REST server. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 15 of the MITRE ATT&CK framework.
| Tactic | ID | Identify | Description |
| Useful resource Growth | T1583.003 | Purchase Infrastructure: Digital Personal Server | Situations of the RedLine again finish are hosted on leased digital personal servers. |
| T1583.004 | Purchase Infrastructure: Server | Situations of the RedLine again finish are hosted on servers that look like unique to RedLine. | |
| T1587.001 | Purchase Infrastructure: Internet Companies | Operators of RedLine have created a number of GitHub accounts and repositories. | |
| T1587.002 | Develop Capabilities: Malware | Operators of RedLine have developed their very own malware households, management panels, and back-end servers. | |
| T1588.003 | Develop Capabilities: Code Signing Certificates | The RedLine again finish mechanically generates self-signed certificates when creating samples. | |
| T1608.002 | Get hold of Capabilities: Code Signing Certificates | RedLine panels are signed with legitimate certificates issued to AMCERT,LLC. | |
| T1608.001 | Stage Capabilities: Add Malware | Again-end parts of RedLine are uploaded to non-public servers. | |
| Protection Evasion | T1622 | Debugger Evasion | The RedLine panel mechanically terminates itself if it detects a debugger or evaluation instruments. |
| T1027.002 | Obfuscated Recordsdata or Data: Software program Packing | Samples of the RedLine panel are packed utilizing DNGuard and BoxedApp. | |
| Command and Management | T1132.001 | Knowledge Encoding: Customary Encoding | RedLine makes in depth use of base64 encoding in its community communications. Community communication makes use of the usual binary encoder of the WCF framework. |
| T1573.001 | Encrypted Channel: Symmetric Cryptography | Communications between the panel and back-end server use AES encryption. In some instances, dead-drop resolver content material is encrypted with AES-CBC. |
|
| T1573.002 | Encrypted Channel: Uneven Cryptography | Communications between the panel and back-end server use RSA encryption. In some instances, dead-drop resolver content material is encrypted with RSA. |
|
| T1071.001 | Software Layer Protocol: Internet Protocols | Community communication in current variations is finished through a REST API over HTTPS. | |
| T1095 | Non-Software Layer Protocol | Community communication is finished with the WCF Framework over TCP. | |
| T1102.001 | Internet Service: Useless Drop Resolver | The RedLine panel makes use of GitHub repositories as dead-drop resolvers to acquire the deal with of back-end servers. | |
| T1571 | Non-Customary Port | By default, the RedLine panel’s Visitor Hyperlinks performance runs an HTTP server on port 7766. |


